5 Principles to Achieve Zero Trust for the Workforce - Enforce Adaptive Policies (Part 4)
Editor’s note: The journey to zero trust is a multi-step process that encompasses three key areas: the workforce, the workload and the workplace. Week one we explored the history of zero trust and how to establish user trust. Week two we delved into the history of endpoint security and gaining visibility into devices. Week three we reviewed zero-day exploits and establishing device trust. Today we will explore the fourth principle in this five-part blog series — how to enforce adaptive policies.
Zero trust is not a single product, rather it is a security framework based on the model of “trust no one.” User trust is not granted until the user can be authenticated and authorized first through multi-factor authentication. The history of the zero-trust journey coincides with the mass adoption rate of mobile devices (endpoints) and devices connected to the internet (screens, IoT, APIs, application and services) that have access to the corporate network. As we learned in previous posts, the zero-trust philosophy was born from the need to think past the firewall and expand the perimeter to anywhere, to ensure protection from stolen or lost credentials, and to protect access to all applications, for any user and device across the network.
The History of Networking and the Path to Micro-Segmentation
Networking is about moving information from one computing device and system to another. Long ago, in a world distant yet not so far away, TCP/IP was the preferred platform for network engineers to control the flow of data and traffic with its Physical Layer 1 hubs and cables, Link Layer 2 switches and modems, Layer 3 Internet Protocol or IP (routers), and the firewall or transport (Transmission Control Protocol or TCP) as Layer 4. You could use a router to divide your IP segments, you could use a firewall to divide your network ports and you could plug and unplug cables to move computers on or off a network.
The TCP/IP protocols were initially developed as part of the research network developed by the United States Defense Advanced Research Projects Agency (DARPA or ARPA). Initially, this fledgling network, called the ARPAnet, was designed to use a number of protocols that had been adapted from existing technologies. — The TCIPGUIDE
The 90’s introduced the Virtual Local Area Network (VLAN), which lowered computing costs, and networking moved to 3-layer switches with flexible segmentation. Security teams focused on restricting access, while IT operations focused on helping the business grow with more and more connections. The network could sit behind security, and traffic could flow past the firewall perimeter with automatic trust and access. There, configurations were never exactly optimal or frictionless with a combo of hardware and software applications managing data movement.
Around 2013, Cisco introduced the Application Centric Infrastructure (ACI) which changed networking. Eventually, new multi-tiered applications brought new network and security challenges and the need for more granular controls through micro-segmentation that ACI solved for through policies. The modern version of this is called the Cisco Tetration platform that uses machine learning to build policy around every packet in the data center.
Now modern networking requires cloud, on-prem and hybrid applications to move toward a zero-trust security model, which expands the perimeter to anywhere, any device, any application on any platform. Zero-trust security starts before workforce devices ever hit the network by enforcing adaptive device policies.
STEP 4 - ENFORCE ADAPTIVE POLICIES
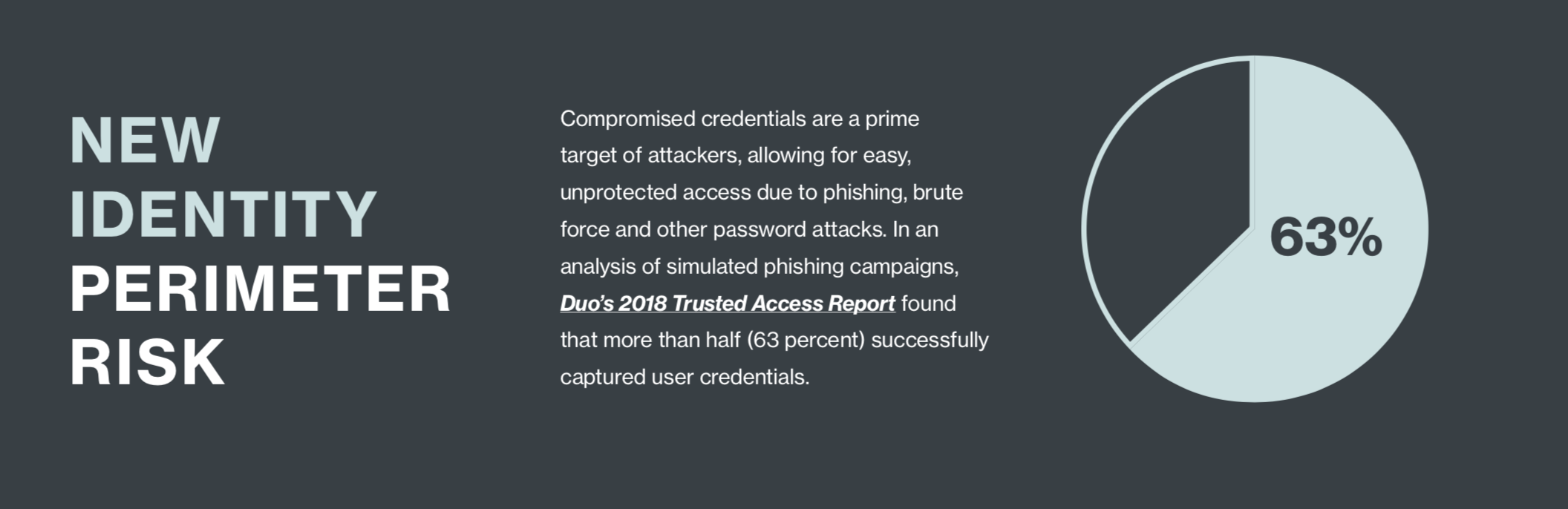
The ability to set granular controls through multi-factor authentication (MFA), which requires two or more authentication factors to verify trustworthiness and rebalance risk is essential to adopting zero-trust security.
“If your device is going to access my corporate network, when you reach out to touch my network I’m going to mandate that that device is checked for its patch level. And I’m going to mandate that that device is pushed through a multi-factor authentication protocol. And lastly, I’m going to make sure that when that device gets into my network that it’s living and existing within a segment of a network that I have really good visibility on and really good response capabilities on. I’m not going to let that device just sort of jump onto the network and do whatever it needs to do and then roll out — that’s not the way that this should work.”
—Dr. Chase Cunningham, Principal Analyst at Forrester on "Federal Drive"
WHAT ARE ADAPTIVE POLICIES?
Adaptive authentication and policies are highly customizable contextual controls that add maximum multi-layered security for your environment. Adaptive authentication and policy enforcement allow organizations the freedom of BYOD (bring your own device) without the risk. Limit access to only what your users need to do their jobs and add stricter controls for access to more sensitive applications – without negatively impacting user workflows.
Contextual Access Policies
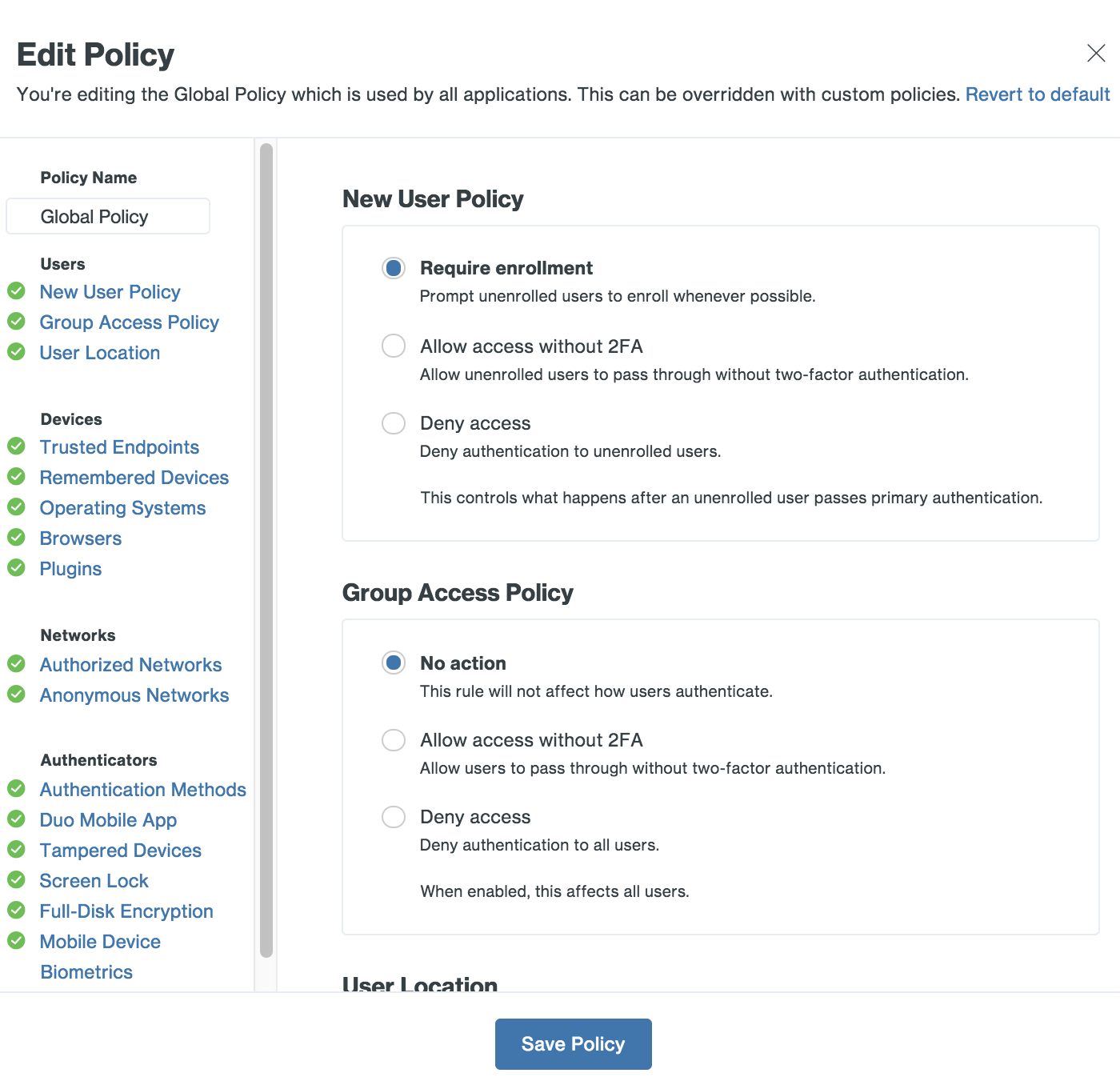
Customize policies to allow, deny or require stricter security based on user-specific roles and responsibilities, devices and applications.
Role-Based Policies
Not all users need access to every application. Customize access based on the type of user group. Give contractors or third-party providers temporary and restricted access to non-sensitive applications or systems.
App‐Specific Policies
Your admins should be able to configure app-specific policies to require only the use of push-based or U2F security keys to verify your users’ identities before granting access to these applications.
Location-Based Policies
Prevent unauthorized access from any geographic location with user-based access policies. If you don’t do business in certain countries, you should be able to block access attempts originating from those regions.
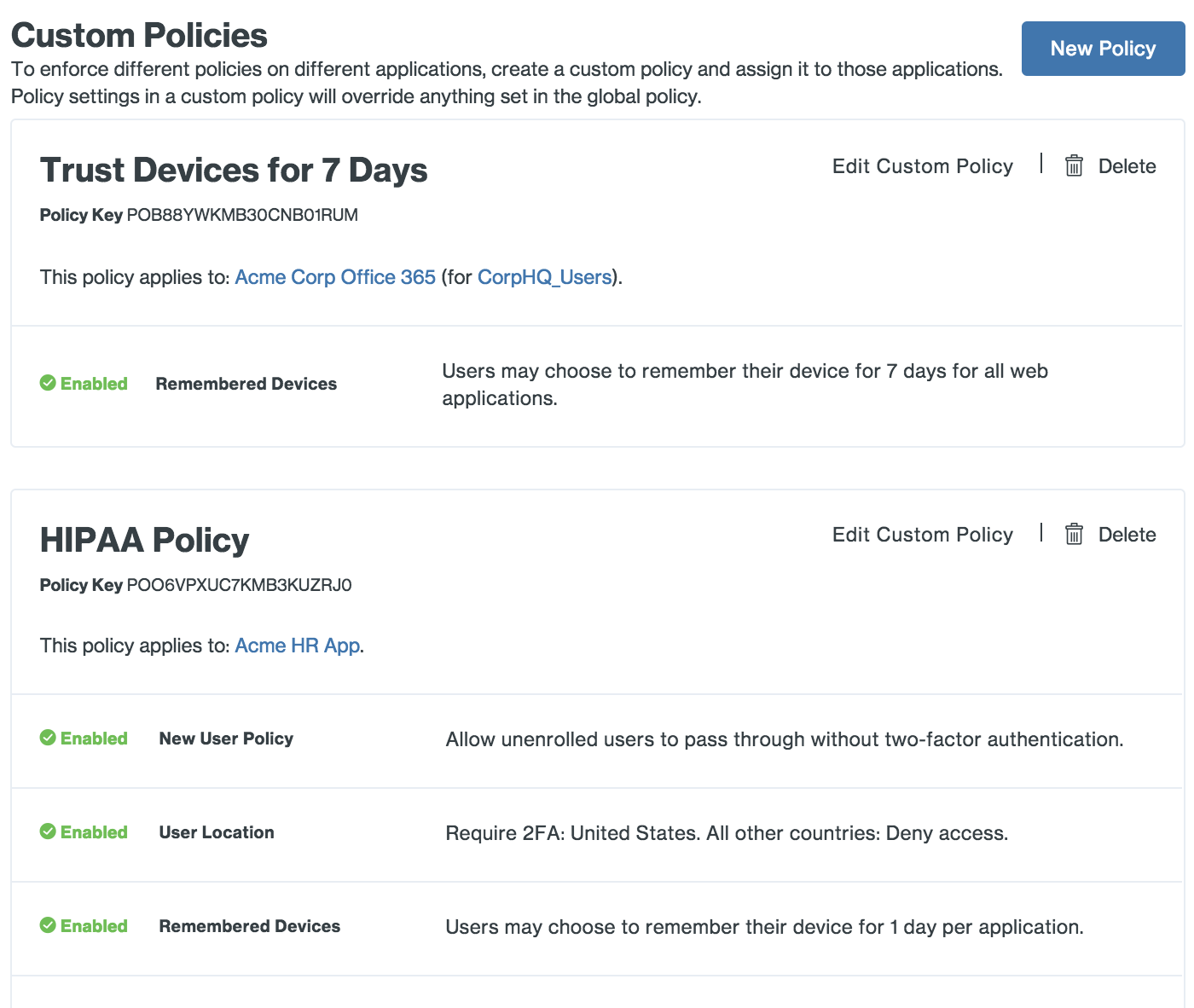
Custom Policies
If certain applications require policy and controls that differ from the Global Policy, you can create a Custom Policy and assign it to those applications. Custom policies for an application can also be limited to specific groups.
POLICIES ARE THE INFINITY STONES OF ZERO TRUST
Setting these granular and adaptive policies offers organizations amazing protective superpowers for their workforce. These policy controls work seamlessly in the background, persistently utilizing excessive trust to verify and authorize access to network environments.
This complete security solution prevents modern attackers that often target multiple areas – like credential theft and the exploitation of known software vulnerabilities from outdated software versions.
Duo Security verifies users’ identities with strong multi-factor authentication and gives you the policies and control you need to limit access based on endpoint or user risk. Users get a consistent login experience with Duo’s single sign-on that delivers centralized access to both on-premises and cloud applications.
View Duo’s Policy & Controls documentation
“The old way was ‘I have a lock on the door of the data center and I can control who goes in it’ and ‘I have an internal network that’s protected by a very hard exterior.' Now, with cloud-based services, we have to take a lot more control of how we let people into those systems. The days of just username and password are long behind us. Duo is lightweight and inexpensive and gives a valuable, supplemental scope of insight and control over devices that is complementary to our MDM and extends into the desktop and laptop environment.”
— Dan Ayala, Director of Global Information Security, ProQuest
Have Confidence and Insight Into Maintaining the Networks
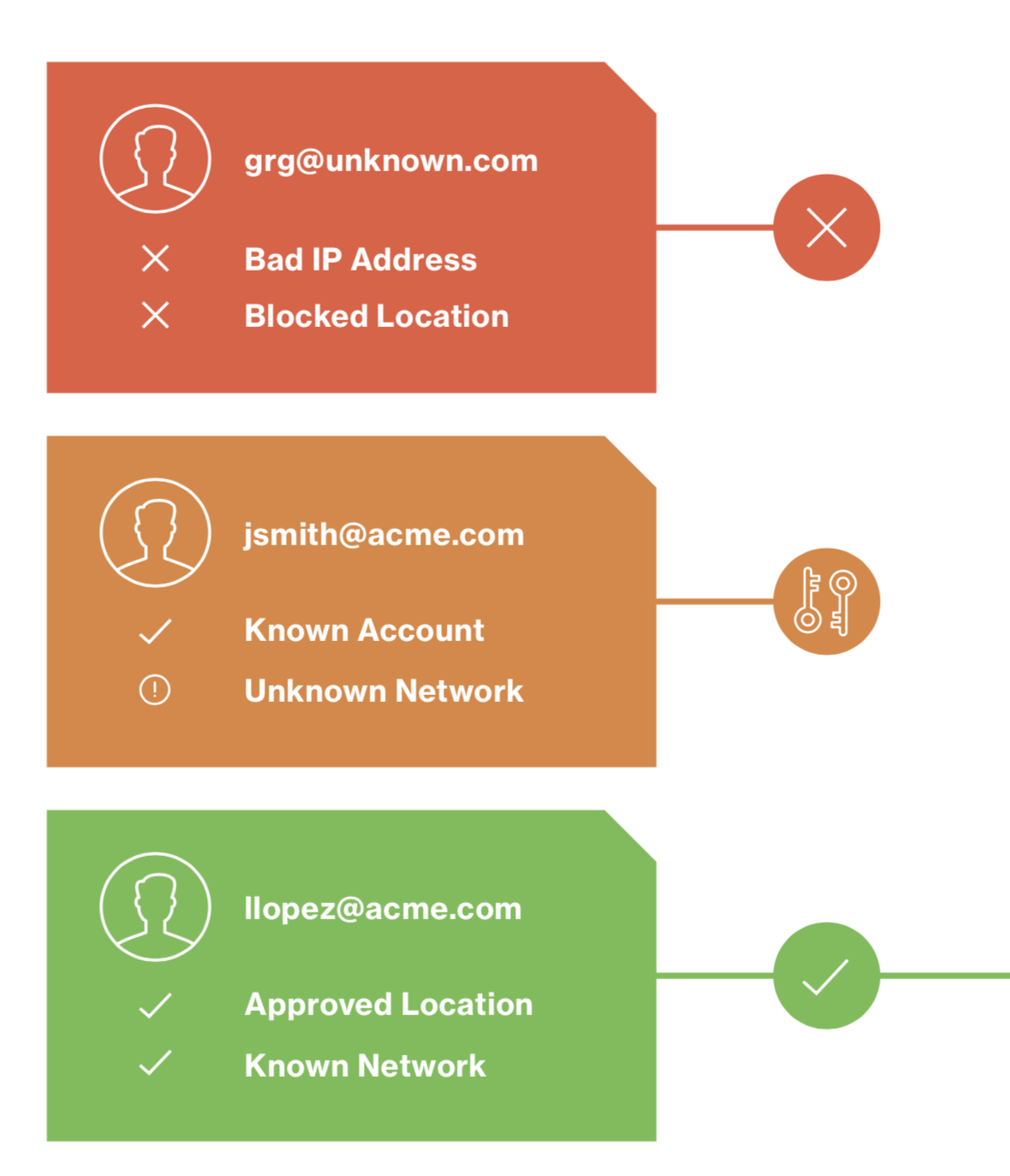
Prevent compromised credentials. When a user logs into an application, they verify their identity with Duo’s two-factor authentication (2FA), preventing the risk of unauthorized access due to stolen or weak passwords
Duo’s platform detects and tracks every device accessing protected applications, including desktop, laptop, mobile, corporate and personally-owned devices – without using an agent
Enforce endpoint controls. Whether or not you have a mobile device management (MDM) solution, Duo can block devices from accessing your applications
Notify users to update. Duo alerts users to install required updates to prevent risk
Have more policy control. Manage contextual policies, role-based policies, app-specific policies, location-specific policies and more with Duo.
Duo aims to democratize security so that every device is protected on every platform. Security should not be intimidating, complicated or difficult, and we designed Duo to be powerful, simple and easy to use for everyone.
Duo’s approach to zero-trust security for the workforce is different in four ways:
Speed-to-Security: Duo delivers all the zero-trust building blocks under one solution that is extremely fast and easy to deploy to users. Some clients can be running in a matter of minutes depending on their specific use case.
Ease of Use: Users can self-enroll as simple as downloading an app from the app store and signing in. Maintenance and policy controls are easy for admins to control and gain clear visibility.
Broadest Coverage of Applications: Our product is designed to be agnostic and work with legacy systems so no matter what IT and security vendors you use, you can still secure access to all work applications, for all users, from anywhere.
Lower Total Cost of Ownership (TCO): Because Duo is easy to implement and does not require replacing systems, far less resources in time and cost are required to get up and running and begin the journey to a zero-trust security model.
So far in this series we have covered the first principle to implementing a zero-trust framework; how to establish user trust. Gaining device visibility is the second principle to adopting zero-trust and establishing device trust is the third principle. In next week’s blog we will review the fifth principle to achieving zero trust: how to enable secure access to all applications.
Learn more about Duo Beyond, our zero-trust platform for the workforce- or sign up for a free 30-day trial to try it out today.

Zero Trust Evaluation Guide: Securing the Modern Workforce
We’ve released a new guide to help you understand the different criteria for a zero-trust security model. Secure your workforce - both users and devices, as they access your applications.
Download guide

