Announcing the General Availability of Verified Duo Push
As attackers have figured out ways to get around traditional multi-factor authentication (MFA), Duo has continued to evolve to prevent fraudulent access and protect the workforce. Every day, users are inundated with notifications on their phones, and it can be difficult to appropriately respond to each buzz or alert. Some attack patterns, like push harassment, rely on the assumption that if you bother an end user enough times, they will eventually relent and accept the request.
In response to MFA fatigue and push-phishing attacks, we announced the Public Preview of Verified Duo Push in August of this year. Now, we are thrilled to announce the general availability of Verified Duo Push to all MFA, Access, and Beyond edition customers.
Making MFA More Secure
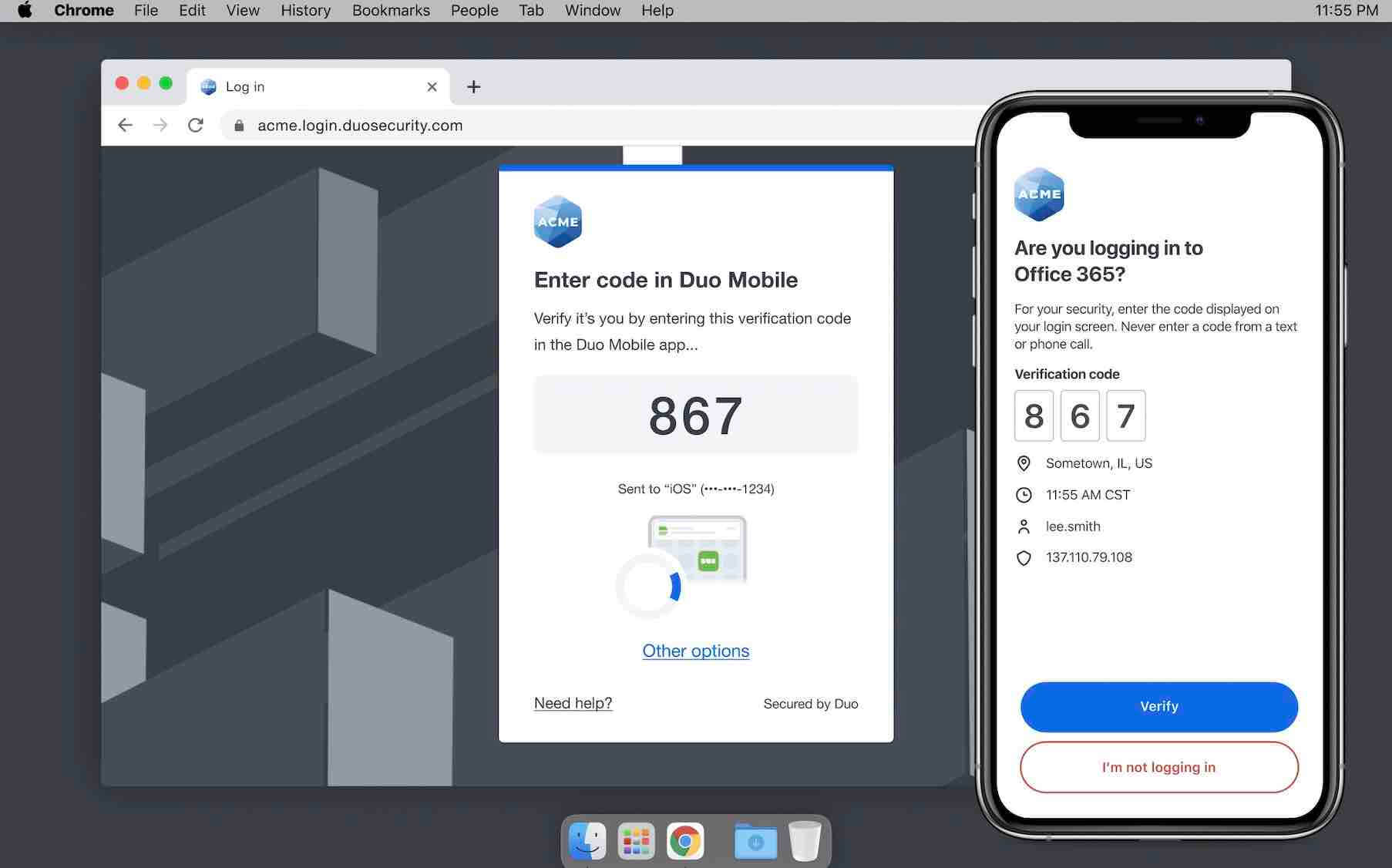
Verified Duo Push strengthens MFA security by adding friction to the authentication process. With a normal push request, an end user might absentmindedly click ‘Approve,’ but a Verified Duo Push requires the user to input a numeric code in order for the authentication to be successful. If the request is from a bad actor, the extra steps the user has to take means they have more time to realize they should deny the request and mark it as fraud. The user also will not have the unique code, which creates another barrier to access if the request is not valid.
Early adoption of Verified Duo Push has been strong, and we’ve received great feedback from our customers. Security teams who worried that employees would not tolerate the extra time necessary to access their applications have shared that the response has been so positive that they’ve rolled it out to their entire employee population instead of select groups. One customer told us that the experience was so seamless that they were able to enable it as a global policy without even telling their employees.
Today, we are thrilled to announce the general availability (GA) of Verified Duo Push. Verified Duo Push can be configured as a static Authentication policy and is available on all Duo editions.

Lessons from Public Preview
During public preview, we learned a lot from the hundreds of customers who participated. And we have used that feedback to continue to evolve the user experience. Our initial implementation of Verified Duo Push required users to input a 6-digit code to make it difficult for attackers to randomly guess the code correctly. However, customers wanted the option to customize the code length. With our GA release, Verified Duo Push can be configured to be between 3-6 digits long, depending on the preferred balance of security and end user experience.
Verified Duo Push helps strengthen the initial promise of MFA, even in light of new and emerging push attacks. Duo already supports FIDO2 authenticators, which offer the strongest protection against MFA-based attacks. But we know that rolling this out across an organization is a journey, and Verified Duo Push can help along the way. This is highlighted by a recent CISA Fact Sheet that recommended implementing a solution like Verified Duo Push to make MFA more secure.
However, some organizations might struggle to get organizational buy-in to add friction for every login. As an alternative approach, Duo’s new Risk-Based Authentication solution only steps up to the more secure method when risk signals in the environment indicate there are potential threats. Whether security teams enable Verified Duo Push for all users, or through a risk-based approach, this allows organizations to make decisions based on their risk appetite and organization’s needs.
As we continue to add to our Risk-Based Authentication policy stack, we know that Verified Duo Push will continue to play a big role in keeping users and organizations safe. Verified Duo Push is one step in customers’ security journey and Duo will continue to work towards the balance of protecting customers and providing a good user experience.

