Bringing U2F to the Masses
Major tech companies like Google Dropbox and, more recently, Facebook have begun allowing users to log in with security keys. These security keys implement an open standard called Universal 2nd Factor, or U2F.
So What is U2F?
In 2011, Google, Yubico, and others created a second factor for authentication that used public key cryptography to securely authenticate a user to a web service. This process works by first having a device generate a keypair and register the generated public key with the server. Then, when a second authentication factor is required, the server sends a unique challenge to the device. To respond to the challenge, the device unlocks its generated private key after verifying a user is actually present (say, by having the user press a button or enter a pin), and then returns the challenge signed with the private key.
An important part of this challenge/response process is that it takes into account the hostname of the URL, or “origin” the user is currently on. Every keypair that is generated is tied to a particular origin. Before performing any signing operation, the device first confirms that the origin is correct, this essentially makes the authentication process unphishable.
In addition to the strong phishing protections, the U2F protocol design provides strong user-centric privacy properties to ensure U2F users have anonymity in the eyes of service providers. A U2F device is not bound to a user’s real identity, be that phone, fingerprint or computer, and as each registration generates a new keypair, it is impossible for a U2F device to be correlated across different services or even across different accounts on the same service.
The companies brought the idea for hardware-backed, unphishable second factor authentication under the umbrella of the FIDO Alliance as an open standard, which became known as U2F. Duo’s goal is to stay on the leading edge of usable, secure authentication, which is why we have proudly been a member of the FIDO Alliance and supported U2F for our customers since 2014.
Here’s how it works:
Driving Increased U2F Adoption
While the U2F standard has been around since 2014, the rate of adoption is not as high as we would hope for such a strong authentication technology. Authenticating via U2F requires having both the 2FA service provider (the Relying Party in U2F speak), and the browser vendor support the U2F protocol. It also requires the user to have a U2F-compliant device that the browser communicates with to perform the actual cryptographic signing. This hardware has, up until now, almost always came in the form of external keys connecting to systems over USB, NFC, or Bluetooth. Some of the best have come from Yubico.
Unfortunately, the requirement of needing an extra hardware device in order to make use of U2F creates some barriers to adoption for many businesses as well as end users due to the costs associated. These costs range from the capital expenditure costs of purchasing new security hardware devices themselves, to the technical logistical costs of losing access to one of the device’s already-limited USB ports (or lack of USB-A ports altogether - thanks Apple!).
While on the face of it, these can be seen as small issues that are easily surmountable for an organization that takes security seriously, the reality is that they can significantly reduce the ability of such projects to get a green light. Even when the barriers to hardware purchase have been circumvented, there is also a responsibility placed on the end user to have their U2F device either on hand or plugged into their device. If they don’t, then they will likely fall back to an alternate 2FA technology such as HOTP/TOTP or even SMS.
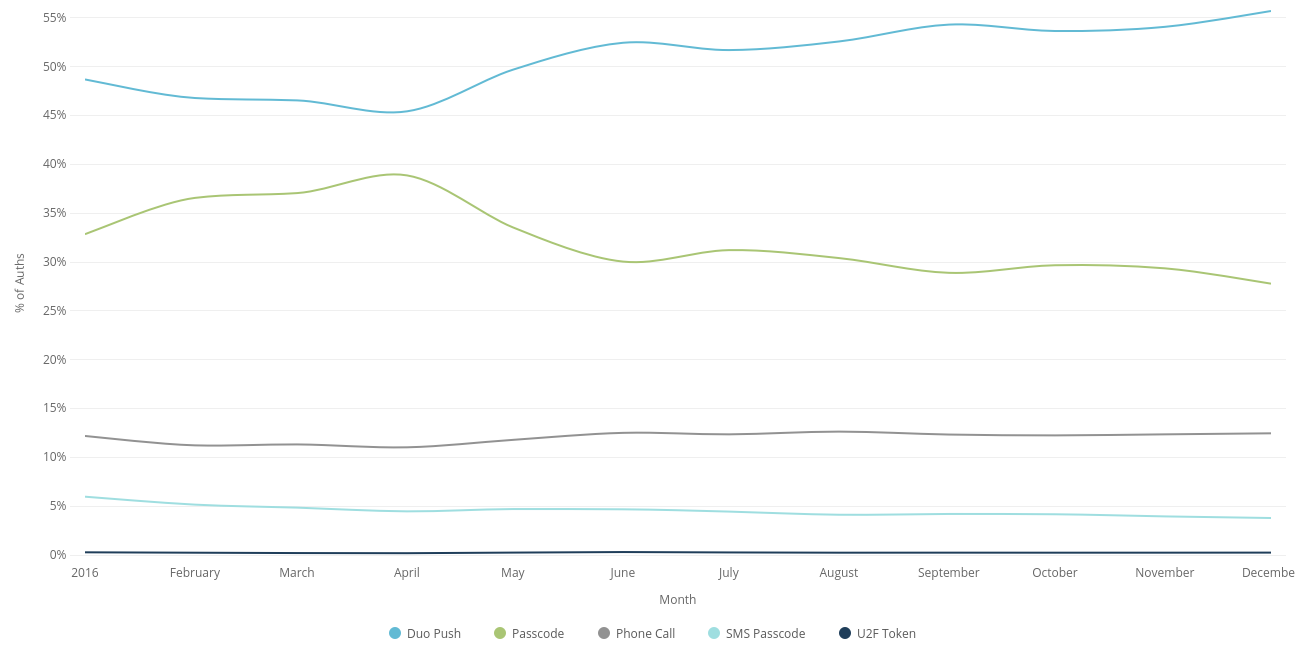
As can be seen from the graph below, only about 1% of all 2FA authentications that Duo sees currently make use of U2F, and this trend has not shifted upward to any significant degree over the last 12 months.
Duo Labs + Intel
Duo’s service is built to make effective, usable security as easy to deploy and manage as possible. In Duo Labs, we actively partner with other industry leaders and research teams to take advantage of the latest authentication technologies to better protect our customers as early as possible.
Intel’s 7th Generation Core Processors (codenamed Kaby Lake) ship with the Intel Converged Security and Manageability Engine (CSME) and provides the functionality needed for U2F, such as generating, registering and signing U2F challenges with a key pair. Intel has also created “Intel Online Connect,” which enables Windows computers to support the FIDO U2F standard natively without the need for any additional hardware.
The benefit of Intel’s work on bringing native U2F capabilities directly into the chipset means that companies and consumers no longer need to buy additional hardware to leverage U2F and that they can take advantage of it as a side benefit of updating their client fleets. Duo has worked to ensure that Intel’s latest hardware works seamlessly out of the box with the existing U2F support that has been available in Duo’s Trusted Access platform since 2014.
Intel took an interesting approach to their implementation of a U2F client. Instead of the USB hardware devices most people are already familiar with, Intel chose to implement their U2F client in software and display a square on the screen at a randomly-generated location that a user clicks on to fulfil the user presence test. Intel are making use of Protected Transaction Display technology to ensure that the input and output channels cannot be eavesdropped or bypassed programmatically. Once the user presence test has been completed, the U2F challenge is signed by a key that is securely stored in hardware and passed back to the browser.
The software-only U2F implementation will make strong U2F-based authentication available to every user of a Kaby Lake device without any further investment in hardware by users or organizations. From Duo’s perspective, the more people who are able to benefit from the strong second factor authentication offered by U2F the better - what’s a better way to ensure this than having a U2F device built directly into their system to enable a frictionless workflow. We are hopeful that as Kaby Lake devices begin to penetrate the market, we will see an uptick in the adoption of U2F as the user’s preferred second factor mechanism.
Intel & Duo at RSAC 2017
We were really pleased to be able to show off our prototype integration with Intel at this year’s RSA conference and to get to speak to so many people about how this might help increase the security of their organisations.
.@duosec + @intel online connect FIDO Authentication demo in action (1 of 2) pic.twitter.com/iNzIwprAEi
— The FIDO Alliance (@FIDOAlliance) February 16, 2017
.@duosec + @intel online connect FIDO Authentication demo in action (2 of 2) pic.twitter.com/nDNtV5dbFM
— The FIDO Alliance (@FIDOAlliance) February 16, 2017
Thanks to everyone who came by the Duo booth to say hi and chat about embedded security hardware! You can find our official press release here.

Security is always best when it’s built in, not bolted on. We’re excited to continue partnering with leaders like Intel to bring built-in native U2F support to businesses and consumers to help make it as easy to use as possible.

