C-Level Executives’ Credentials Most Coveted in 2019 Verizon Security Report
Pull up a chair, and get ready to dig into the changing security landscape.
According to the 2019 Verizon Data Breach Investigations Report (DBIR), which analyzed 41,686 security incidents in over 86 countries, with 2,013 confirmed data breaches from 73 data sources and 63 external private and public entities (including the FBI), “no organization is too large or too small to fall victim to a data breach. No industry vertical is immune to attack.” The report notes corporate executives and small businesses are increasingly the top targets by bad actors.
Security Incident vs. Security Breach
Security Incident: A security event such as impersonation, denial of service and website defacement that doesn’t involve the theft of sensitive personal data.
Security Breach: A security incident that involves the release of personally sensitive, protected and/or confidential data, such as social security numbers and personal health records.
Corporate Executive Credentials Highly Desirable
While business email compromised (BEC) attacks on Human Resource personnel have decreased by six times from last year, corporate executives were targeted nine times more for social breaches and C-Level executives (CEO, CFO, CMO etc.) were targeted 12 times more for social incidents according to Verizon.
Corporate leadership, which often has privileged access to valuable information and computer systems coupled with undisputed and unquestioned authority to make requests, is an obvious sweet spot for bad actors. Corporate executives are often seen as easy marks with big impact – they’re frequently on the move with limited time to digest large amounts of information, making them targets of dedicated social engineered attacks such as phishing, spear phishing and more.
Security does not have to be complicated and it does not have to be scary either. Luckily, these attacks can easily be thwarted by multi-factor authentication, one of the building blocks of zero-trust security, to establish and protect trusted users.
“Security must remain front and center when implementing these new applications and architectures. Technical IT hygiene and network security are table stakes when it comes to reducing risk. It all begins with understanding your risk posture and the threat landscape, so you can develop and action a solid plan to protect your business against the reality of cybercrime.”
— George Fischer, president of Verizon Global Enterprise
What is Causing Data Breaches?
Phishing
Use of stolen credentials
Top Application Vector Threats
Email accounts (OWA or O365)
Web applications (SaaS/cloud)
Workstations
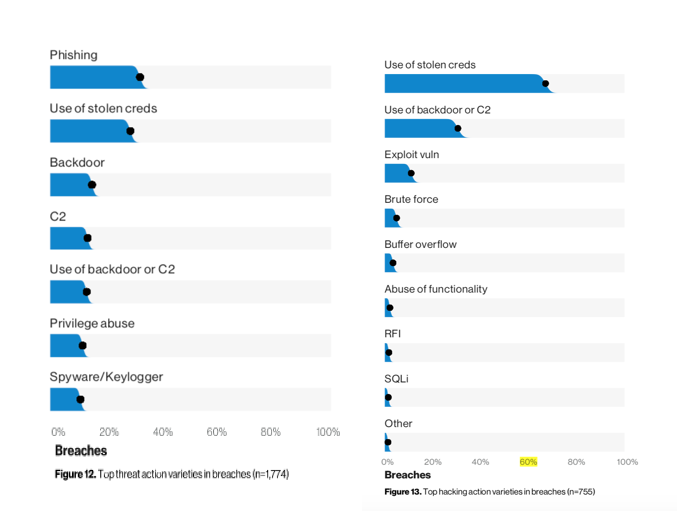
Important Findings for Stolen Credentials and Application Threat Vector
60% of the time, the compromised web application vector was the front-end to cloud-based email servers
Workstations, web applications, and surprisingly, mail servers are in the top group of assets affected in data breaches
Most often, those compromised credentials were to cloud-based mail servers. There was an uptick in actors seeking these credentials to compromise a user’s email account. Once an actor has one credential, they can launch large phishing campaigns from the account, or if the account owner has a certain degree of clout, send more targeted and elaborate emails to employees who are authorized to pay bogus invoices
.png)
Mobile Users Are More Susceptible to Social Attacks
The small screen size of mobile screens restrict viewable information necessary to verify fraudulent emails
Many mobile browsers limit access to website SSL certificates
Prominent features on mobile like “accept, reply, send” make it easier for users to make snap decisions
Mobile users are often walking, driving, talking and more decreasing their attention to details
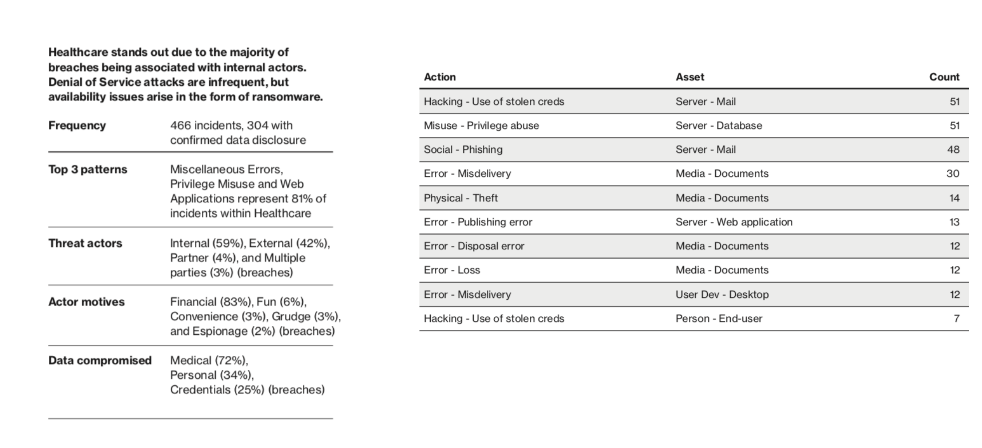
Healthcare Industry Breakdown
15% breaches in 2019
Attackers are going after email accounts via stolen credentials
72% of breaches result in medical data being compromised
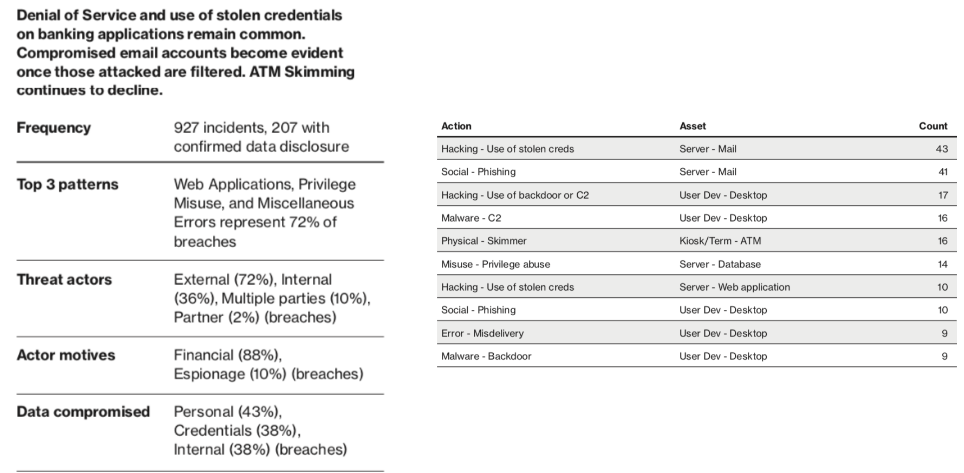
Financial Industry Breakdown
10% of breaches in 2019
Attackers are going after email accounts via stolen credentials
Attackers are leveraging Social Phishing as a means of obtaining comprised credentials
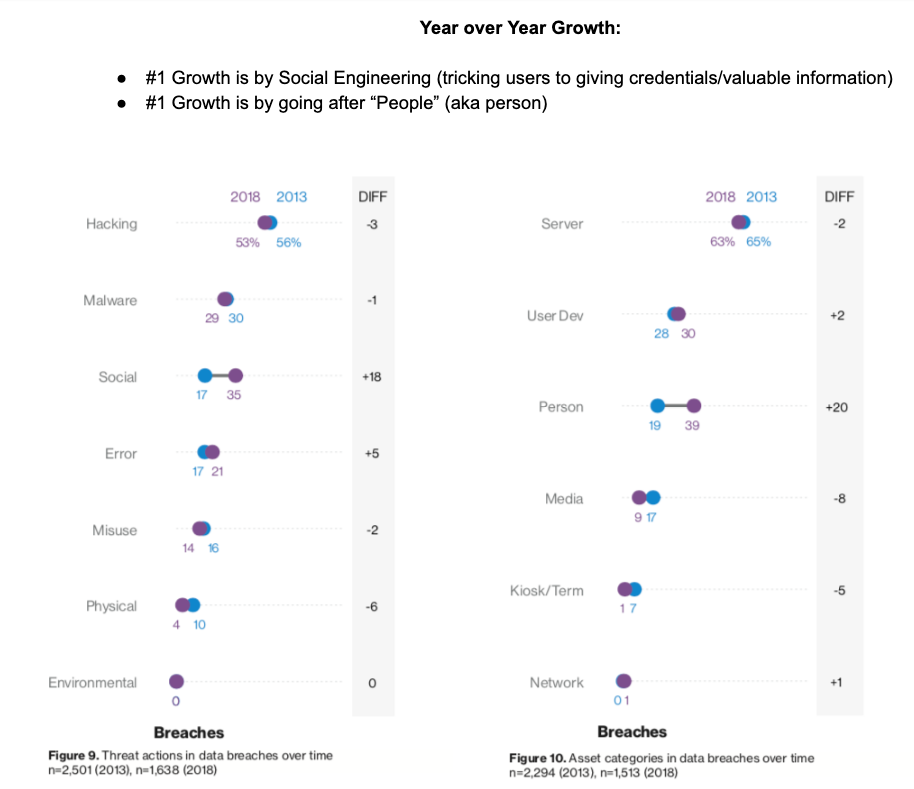
More Major Findings
69% of attacks are perpetrated by outsiders
39% of all attacks are perpetrated by organized criminal groups
23% of bad actors are identified as nation-state or state affiliated
43% of breaches involved small businesses victims
52% of breaches involved hacking
33% included social attacks
28% involved malware
12% increase in C-level executives proactively targeted by social breaches
98% rise of compromise of web-based email accounts using stolen credentials - seen in 60% percent of attacks involving hacking a web application
Outsider threats remain dominant: External threat actors are still the primary force behind attacks (69% of breaches) with insiders accounting for 34%
Misconfiguration (“Miscellaneous Errors”) led to a number of massive, cloud-based file storage breaches, exposing at least 60 million records analyzed in the DBIR dataset. This accounts for 21%of breaches caused by errors.
As businesses embrace new digital ways of working, many are unaware of the new security risks to which they may be exposed. They really need access to cyber detection tools to gain access to a daily view of their security posture, supported with statistics on the latest cyber threats. Security needs to be seen as a flexible and smart strategic asset that constantly delivers to the businesses, and impacts the bottom line.”
— Bryan Sartin, executive director of Global Security Services at Verizon
Recommended Protection From Phishing
Verizon reports the ease of use and proliferation of bad actors accessing or stealing credentials to gain access to corporate environments is on the rise. The good news is protectection doesn’t have to be scary. Our founders created Duo multi-factor authentication to make security compliant, easy, affordable and accessible to companies regardless of their size.
Multi-factor authentication is recommended by the FBI and Department of Homeland Security as the first barrier to the protection of systems because it not only establishes user trust, it also authenticates users using several different factors that can not be replicated by bad actors. Multi-factor authentication uses the zero-trust criteria of trust no one until identity can be verified and permission validated.
Duo's Multi-Factor Authentication
Duo is a cloud-based zero-trust security platform that protects access to all applications, for any user and device, from anywhere. It’s designed to be both easy to use and deploy, while providing complete endpoint visibility and control.
.png)
Duo verifies users’ identities with strong multi-factor authentication (MFA), paired with deep insights into your users’ devices. Duo gives you the policies and control you need to limit access based on endpoint or user risk. Users get a consistent login experience with Duo’s single sign-on (SSO) that delivers centralized access to both on-premises and cloud applications.
Duo protects against compromised credentials and risky devices, as well as unwanted access to your applications and data. This combination of user and device trust builds a strong foundation for a zero-trust security model.
LEARN MORE ABOUT PHISHING
Phishing Assessment Made Easy
Duo Insight is a free phishing assessment tool by Duo Security that allows you to find vulnerable users and devices in minutes and start protecting them right away.
Go phishing!Download our ebook "Phishing: A Modern Guide to an Age-Old Problem"

Get a free trial for 30 days and quickly protect all users, devices and applications.

