Default Passwords: Breaching ATMs, Highway Signs & POS Devices
No matter how many times default passwords are pinpointed as the culprit of a high-profile, wide-spread, massive-scale data breach, they’re still out there. On everything, from highway sign software, to ATMs, POS (Point of Sale) devices, television station broadcasting systems and more.
Spanning from the Internet of Things (IoT) security to enterprise-level user and network security, default passwords transcend the delineation between devices, applications and other platforms as a weak entry point often easily exploited for unauthorized access.
To exemplify my point as well as put it into greater context, take the following incidents:
Bank of Montreal ATM Hack: Online Operating Manual Instructions + Default Password
The Winnipeg Sun reported on two 14-year-olds that hacked a Bank of Montreal’s ATM by finding an old ATM operating manual online that showed them how to get to the machine’s operator mode menu.
After being prompted for a password, they were able to get into the system on their first try with a six-character default password.
They immediately reported the vulnerability to the bank, but this type of hack shows the unsophisticated types of attacks that can have very real consequences - by following instructions found online and using a simple default password, they were able to:
- Find out how much money was currently in the machine, how many withdrawals happened in that day, and how much it made off of surcharges
- Change the surcharge amount - they changed the amount to one cent
- Change the ATM’s greeting to whatever message they wanted - they changed it to ‘Go away. This ATM has been hacked.
According to an article on the story by ZDNet.com, ATMs should be protected by a longer/more complicated password. The article also states (my favorite part in bold):
Modern ATM software allows for, and by policy should require, two-factor authentication. There's no excuse for authentication this weak other than laziness.
The SANS NewsBites newsletter reported on this story too, with an editor’s note on default passwords:
One day someone is going to create a list of default passwords and we will be forced to change them. Oh yeah, they already have: http://www.defaultpassword.com
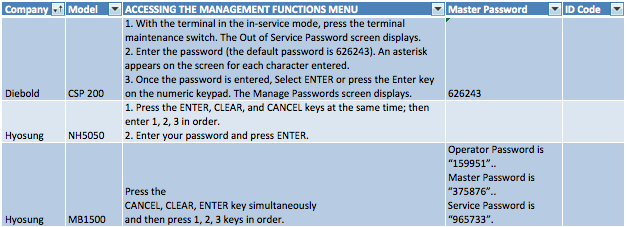
And it’s really not too difficult to find an ‘ATM cheat sheet’ online - after a quick Google search, I found one that listed many models of ATMs, how to get them into operator mode (aka management functions menu/diagnostic mode), and the corresponding default passwords for each. It’s from 2009, but many ATMs haven’t been updated since then…
U.S. Emergency Alert System (EAS) Hack: Default Passwords Published Online
Last February, hackers took control of the equipment used to broadcast warnings via the U.S. Emergency Alert System (EAS) to send the message that zombies were taking over (in so many words).
How’d they do this? By exploiting the use of default passwords on equipment, systems and public station broadcasts to interrupt televised programs with pre-recorded video warnings of the rising dead.
Consequences may not seem severe, but more so reminiscent of the power in creating mass chaos:
While EAS may not control nuclear power or hydroelectric dams or air traffic control, it can be used to cause widespread panic. - Stuart McClure, chief executive, Cylance Inc. as reported to the ChicagoTribune.com.
One of the equipment manufacturers, New York-based Monroe Electronics, told Reuters that some of the compromises occurred because they publish the default passwords for its equipment in user manuals that are available on its public website (why he would admit that is beyond me, but good to know).
In remediation, the FCC sent an advisory to TV stations requesting that they:
- Change default passwords on equipment from manufacturers to deliver emergency broadcasts to TV networks that interrupt regular programming
- Ensure they have secure firewalls in place
- Ensure hackers haven’t queued unauthorized alerts for future transmission
More Recent Highway Sign Hack: Highway Sign Config Software + Default Passwords
Again, more recently reported in early June, hackers changed electronic highway signs for means of notoriety, apparently, with their hacker name/Twitter handle displayed for all highway drivers to see, as KrebsonSecurity.com reports, with a reference to last year’s zombie highway hack.
How do they do it? Krebs cites a number of potential methods, as listed in an advisory by the Multi-State Information Sharing and Analysis Center (MS-ISAC), a nonprofit organization working as the ISAC for state, local, tribal and territorial governments:
Investigators in one state believe the compromise may be in part due to the use of weak Simple Network Management Protocol (SNMP) community strings. Investigators in another state believe the malicious actor used Telnet port 23 and a simple password cracker to gain remote access. In one state the malicious actor changed the modem passwords, forcing technicians to restore to factory default settings to regain access. - MS-ISAC, CIS Cyber Alert
A recent alert from the Industrial Control Systems Cyber Emergency Response Team from the U.S. Dept. of Homeland Security (ICS-ALERT-14-155-01A) warns of vulnerabilities found in Daktronics Vanguard highway notification sign config software. While I’m unsure if these two events are related, the timing is of interest, as the Krebs article broke on June 5, same as the the release date of the ICS alert.
“Daktronics reports that the password is not hardcoded as reported, but is a default password that can be changed upon installation," according to NextGov.com. Meaning, if the default password is left as such, anyone could easily hack into the highway software to display a custom message. This puts the onus on the security teams of the highway sign systems to protect access to their systems and devices by, at the very least, changing their defaults to more complex passwords.
The DHS recommends a number of ways to protect against the vulnerability, including:
- Minimize network exposure for control systems and devices
- Ensure they aren’t accessible to the Internet
- Put system networks and devices behind firewalls/isolate from business networks
- Use VPNs if remote access is required, with the knowledge that VPNs are only as secure as the devices they’re connecting
Unfortunately, that’s where the list ends. Two-factor authentication is another way to secure those VPN connections, as well as any logins, whether or not default passwords are involved.
Retailer Nightmare: POS Devices + Default Passwords
When it comes to POS (Point of Sale) intrusions targeting retailers, the 2014 Verizon DBIR details the most frequently occurring type of scenario that affects small businesses.
This scenario starts with compromised POS devices, which is easily done as the devices are open to the Internet, and protected with weak or default passwords.
While Verizon recommends enforcing strong password policies as a way to remedy this problem, they also strongly recommend using two-factor authentication as a security control:
Stronger passwords would cut out a huge chunk of the problem, but larger organizations should also consider multiple factors to authenticate third-party and internal users. - Verizon 2014 DBIR on recommended controls for POS intrusions
Since default passwords continue to be an issue in the retail and financial/banking industries, as well as the public sector, implementing stronger security controls, including two-factor authentication, can protect your organization from a potential data breach. Find out more about two-factor authentication in:
Facing Modern Information Security Challenges in Banking & Finance
Turning to Two-Factor After Password Exploits
ATM Admin Panels Hacked to Allow Unlimited Withdrawals, Warns FFIEC

