Duo Analytics: Android Device Security
Recently, the Duo Labs team analyzed the current state of security of Android devices. Our large sample includes users' personal devices used to access their employers systems and data, authenticating with Duo's two-factor authentication.
This is the first in a series on our findings from this study, starting with a general overview of Android ecosystems and comparison to our iOS device security findings, which you can find in Identifying Bad Apples: Getting to the Core of iOS Vulnerabilities. The ratio of active iPhones to Android is 2:1, according to Duo's dataset.
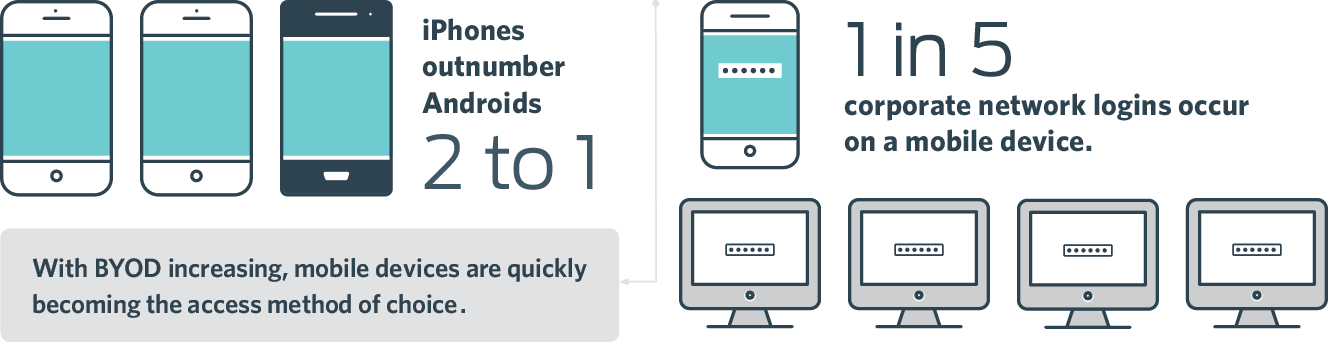
While the industry talks about Bring Your Own Device (BYOD) broadly, it often does little to discuss actual adoption or usage, beyond typical user and company surveys. We recently reported that 1 in 5 authentication events come from mobile devices, and that number is on the rise.
As these platforms continue to become the dominant choice for accessing data and services, understanding platform security on mobile becomes that much more critical.
Key Highlights: Android Device Security Findings
In our sample set of Android devices, we observed some fascinating early trends - a few key security highlights include:
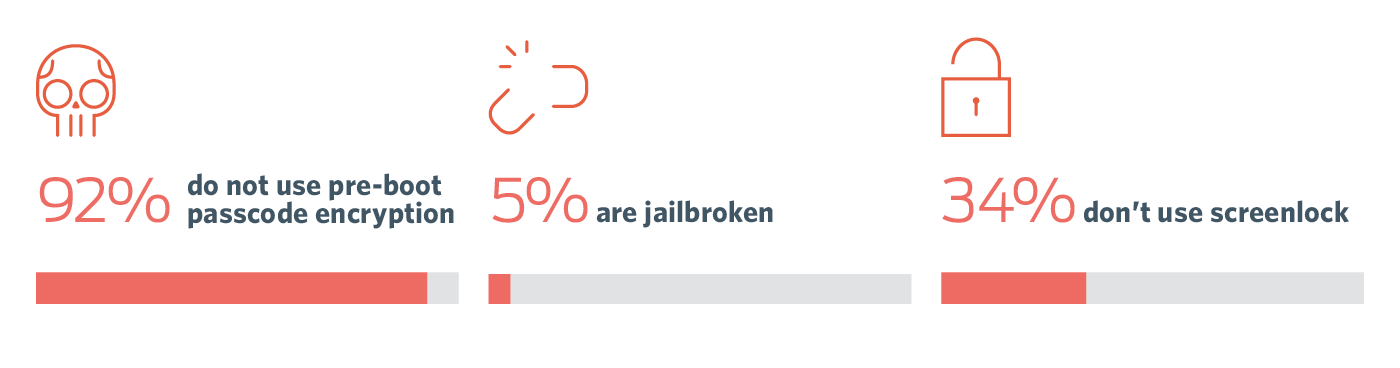
- Only 1 in 10 Android devices have enabled pre-boot passcode device encryption
- 1 in 3 Android devices don't use passcodes on their lock screens, compared to 1 in 20 on Apple devices don't have passcode lock screens enabled
- 1 in 20 Android devices are jailbroken, compared to 1 in 250 iPhones are rooted/jailbroken
- Twenty percent of Android devices are running 5.1.1, a version behind the latest, which is now 6.0.1
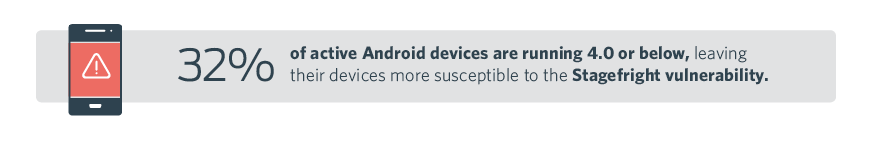
- Thirty-two percent of active Android devices are running version 4.0 and below, which makes their devices more susceptible to the Stagefright vulnerability due to lacking helpful security features added in later Android versions
Many Different Android Devices, Many Running Older Versions
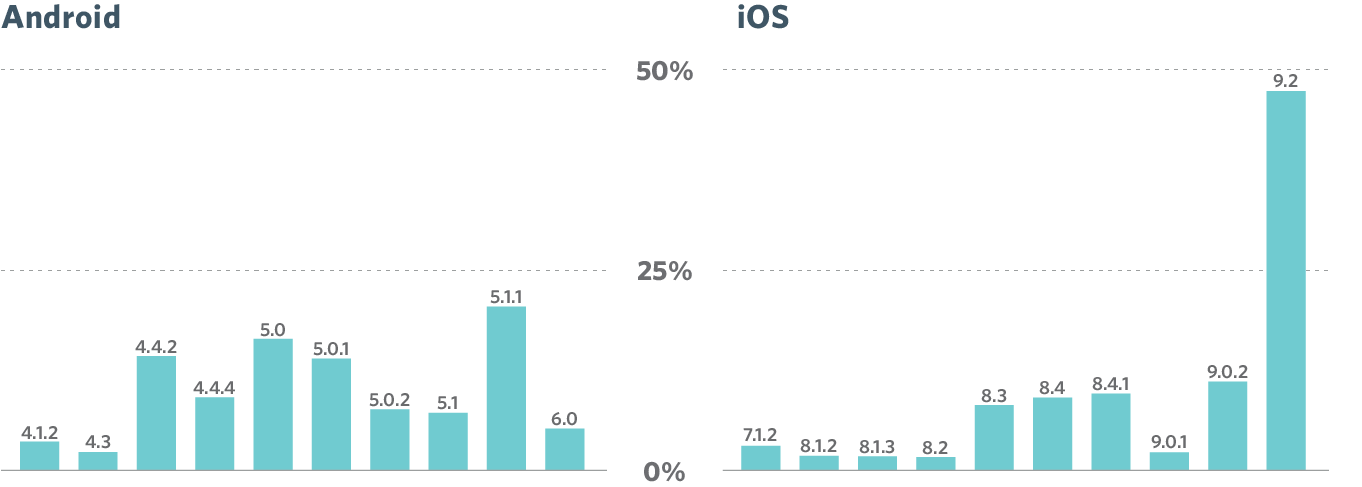
Additionally, the top 10 versions running Android vs. the top ten versions of iOS reveal key differences between platform support:
- Popular Android devices in use today, such as Galaxy S III, are no longer supported by older versions of Android due to hardware limitations
- However, Apple continues to support system updates for iPhone 4S, released over four years ago
Many Android devices are running different, older versions of the OS. The top 5 are distributed as follows:
- 5.1.1 (20%)
- 5.0 (16.42%)
- 4.4.2 (14%)
- 5.0.1 (14%)
- 4.4.4 (9%)
This is due to the large number of hardware manufacturers and models in the ecosystem - several studies, such as OpenSignal, suggest there are over 10,000 unique Android devices in existence. At Duo, if we eliminate devices in our dataset that are obviously emulators, then we can see over 3,700 unique Android hardware models.
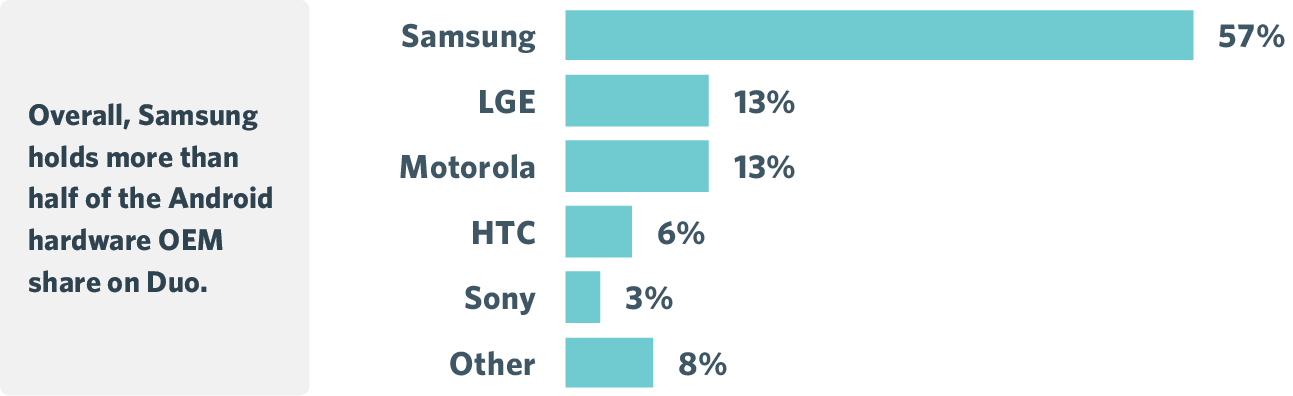
While some are not even recognized as Android devices, according to Google, over twenty of the top leading devices still only represent half the total number of Android devices in use with Duo. The most popular Android device model is Samsung Galaxy S5, which represents 14% of Androids across all carrier models, followed by the Galaxy S4.
Overall, Samsung holds 57% of the Android hardware OEM share on Duo, with LGE and Motorola far behind with 13% each.
On iOS, more than half of all iPhones are running some flavor of iOS 9, but on Android, theres no similar large lead for the most current operating system.
The numerous hardware OEMs and carrier partnerships influence whether or not a given hardware platform is supported, and the length of time for an update to reach the handsets that support it.
This results in a fragmented OS distribution of different Android versions, with many different devices spread across versions 4, 5 and 6.
See more statistics in our full infographic, The Current State of Android Security.
Real-World Security Implications for Android Devices
If your users are running outdated Android versions, they can be vulnerable to several known vulnerabilities. And if they're logging into your company's networks and apps with vulnerable devices, then the entire company could be at risk.
Stagefright Affects Version 4.0 & Below
Stagefright is an exploit deep within the Android OS that could allow for an attack via video sent over MMS (text message). The mechanism that processes Android video files is exploited, so that the attack could happen as soon as a user opens the text message.
Hundreds of millions of phones (some say up to 900 million) are vulnerable to this vulnerability, as it affects a processing mechanism used back in Android 2.2. A lead Android security engineer reported that Android devices running 4.0 and higher have a security mechanism, called ASLR (Address Space Layout Randomization) that can help deter attacks. However, in September, a Project Zero researcher reported that it was easy to bypass ASLR protections and carry out exploits.
In August, a list of manufacturers released patches for Stagefright. But that means devices running older versions can still be susceptible - and, according to our data, 32% percent of active Android devices are running version 4.0 and below, and thus lack these mitigating factors like ASLR.
Stagefright 2.0 Affects …Nearly Every Android Device
Two new Stagefright-related vulnerabilities were reported in early October of last year (also known as Stagefright 2.0), which could allow for remote code execution.
The first vulnerability impacts nearly every Android device since version 1.0 released in 2008, and was recently patched by Google.
Recent Update to 6.0.1
Google also recently released updates to patch for 16 vulnerabilities in Nexus handsets early December, which is the first update to the Android 6.0 Marshmallow mobile OS.
Four of the vulnerabilities were labeled critical, with one that could allow for remote code execution on affected devices while processing media files via email, web and MMS - making it even more imperative that users can update their Android mobile OS to the latest version to protect against these known vulnerabilities.
Duo's Security Recommendations
At a high level, there is some cause for concern about platform fragmentation over time, but this is generally controlled by an organization that allows BYOD or mobile devices for authentication.
Instead, the approach must be to get a better handle on visibility and device insight, to enable organizations to identify devices running legacy operating systems or using hardware that can't receive security updates.
This insight can be used to take appropriate and measured action based on the data. Here's a few security recommendations for organizations:
- Educate users on the fact that Android updates don't deploy automatically and on a timely basis, as they do for iOS users. It can take literally weeks or months for non-Nexus devices to get updates via hardware OEMs or carriers, so users can't assume that new Android updates will be available to them immediately.
- Recommend that users use Nexus devices that receive more frequent and direct platform update support that doesn't depend on carrier/OEM deployment to avoid associated delays.
- Detect users with missing supported security updates, and encourage them to run updates at a convenient time.
Another tool that can help users detect for known Android vulnerabilities is X-Ray, a Duo Labs tool that anyone can download and run on their Android-based phone and/or tablet. Now in version 2.0, this app safely scans for vulnerabilities and allows you to assess your current mobile security risk.

