Smarter Security with Duo’s Risk-Based Authentication
In September 2022, we announced our public preview of Risk-Based Authentication: a set of adaptive policies that both improves security for the riskiest authentications and reduces end user friction for high-trust scenarios. Now, we are excited to announce the general availability of Risk-Based Authentication, a cornerstone of our Continuous Trusted Access offering.
What is Risk-Based Authentication?
Our Risk-Based Authentication policies address two core problems:
Attackers have figured out how to get around multi-factor authentication (MFA)
Users are tired of alerts, and their push fatigue can create security vulnerabilities
To address the ways in which attackers have evolved, we assess user and device telemetry to make decisions about which logins are most suspicious and present credible risk to an organization. Known attack patterns such as push spray, unrealistic travel, and push harassment flag only the highest risk authentications without causing undue friction for users.
When a high-risk login attempt is detected, Duo increases security by requiring a more secure factor, such as a FIDO2 authenticator or Verified Duo Push. The security properties of these factors confer additional confidence that the user is who they say they are, making the extra time and friction worth it.
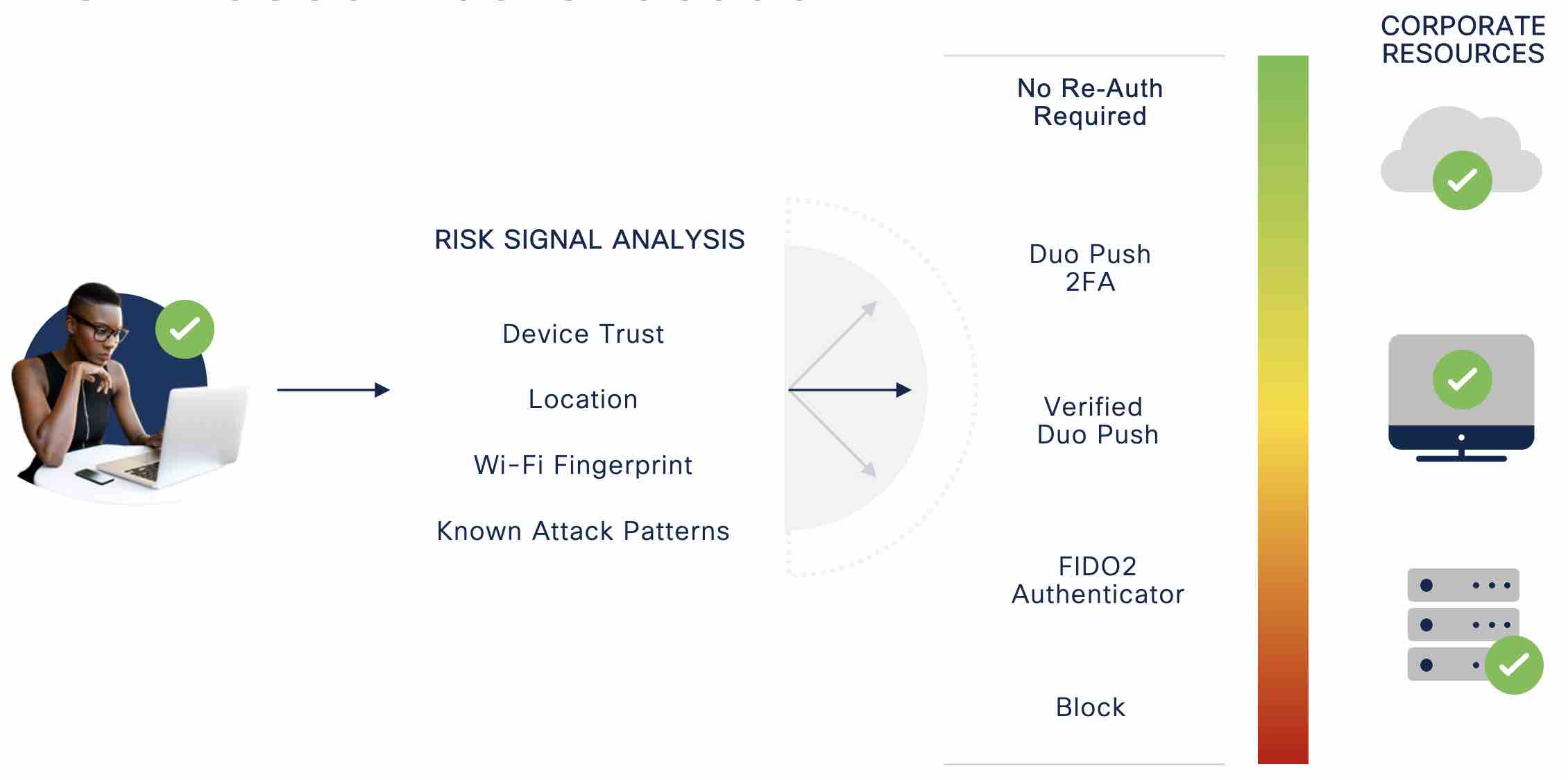
These authentications are costly for users, however, and Risk-Based Authentication takes that into consideration. That’s why we focus on known attack patterns, rather than on the employee who decides to work from a new coffee shop. We leverage users’ individual authentication histories, typical behavior within an organization, and an exciting new signal called a Wi-Fi Fingerprint to make more sophisticated and better decisions about risk.
Until now, IP address has been the best we can do when it comes to user location. In a remote or hybrid work world, IP addresses have become increasingly noisy as users connect to VPN and work outside of the corporate network. With Wi-Fi Fingerprint, we can tamp down on false positives by using anonymized Wi-Fi network information to reasonably determine that the user is still sitting in their living room, not attempting to login from three states away. Wi-Fi Fingerprint protects user privacy while also reducing friction and saving them time.
To address user push fatigue, Risk-Based Authentication also builds on our Remembered Devices policy by removing the interactive component of low-risk authentications. When we recognize a user’s device and IP address, we allow the user to skip their authentication, though we log it and collect the telemetry in the Duo Admin Panel. In other words, the authentication becomes invisible to the user if the location and device context stays the same.
Unlike our regular Remembered Devices policy, once enabled, users do not have to opt-in to Risk-Based Remembered Devices. More time saved for end users!
What we learned from customers
During public preview, hundreds of customers tested both Risk-Based Factor Selection (our “step up authentication” policy) and Risk-Based Remembered Devices (our low friction policy). As one Duo administrator put it, Risk-Based Factor Selection helps him “stay one step ahead. MFA is not the silver bullet it used to be. Everyone’s using it. I need protection beyond regular MFA.” A hospital system told us that they calculated a 50% reduction in MFA requests once they enabled both policies. That is a huge amount of time saved for end users.
MFA is not the silver bullet it used to be. Everyone’s using it. I need protection beyond regular MFA.
Since the launch of public preview this fall, we have added two new detectors to our algorithm to monitor impossible travel between authentication attempts and risky attempts where the access and authentication device are in two different countries. We’ve also validated that Risk-Based Authentication step-ups are not too onerous for end users. On average, a step-up with a more secure factor is required about twice in every 1000 authentication attempts.
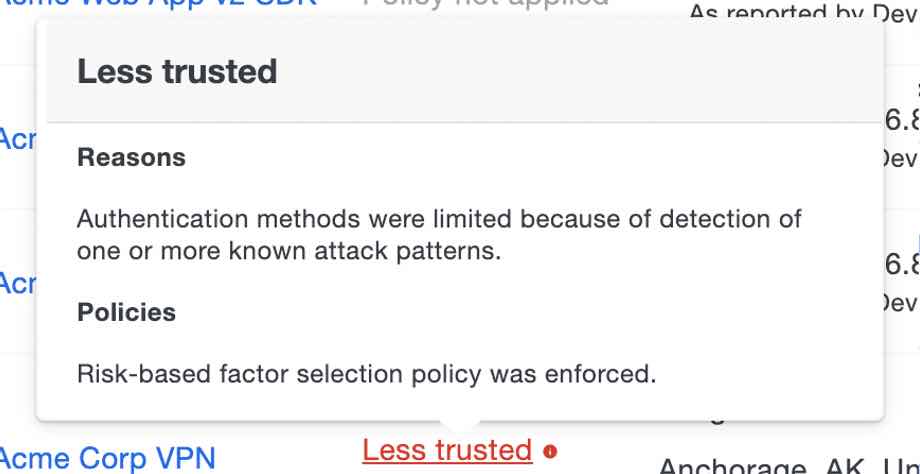
Customers told us that they wanted more information about step-up authentications in their auth logs, so we’ve added a Trust Assessment column, where Duo admins can view how the authentications are classified, including those covered by Risk-Based Remembered Devices that the user never saw. This allows customers to examine why the algorithm may have required a more secure factor so that additional investigation can be performed if necessary.
What is coming next?
We are thrilled to be launching Risk-Based Authentication today, and we continue to evolve our threat detection capabilities with many exciting enhancements planned for the coming months.
Continuous trusted access is all about assessing and responding to risk at different points in the user journey, from enrollment and beyond, and even within a user’s day. Risk-based Authentication will play a key role in continuously evaluating and adapting to a user’s behavior as they go about their workday. Specifically, we will work to detect new attack patterns, blocking the riskiest authentications in the case of a suspected first factor compromise, and responding to more threats at the network, rather than user level.
We are excited for you to try Risk-Based Authentication today! Sign up for a free, 30-day trial of Duo. And be sure to check out the other enhancements we’re making to the Cisco Security Cloud.

