Easily Reduce Your Cyber Risk With Duo Device Trust
This is the final blog of the 4 part series showcasing how organizations can verify device trust with Duo. In the first blog we saw the importance and the need for device visibility. The second blog informed on how organizations can block vulnerable devices. The third blog showed how organizations can prevent breaches and achieve compliance. In this blog, we will summarize how organizations can easily reduce their exposure to cyber risk with the newly available capabilities that make up Duo Device Trust.
The Complicated Problem of Endpoints
Enterprise and SMBs struggle with managing all the endpoints that need access to corporate data. As the workforce becomes more diverse with remote workers, vendors and contractors more third-party devices and BYOD enter the network. This onslaught of unmanaged devices creates complicated challenges for IT to address. Questions arise around how to verify and make an access decision on these devices that have different OS platforms. Do these devices have the recent critical security update installed? What endpoint security settings are required to stay compliant with corporate policies and data security regulations? These devices reside outside of the control of corporate EMM (enterprise mobility management) and MDM (mobile device management) solutions. Enforcing security policies for BYOD and third-party devices can be an arduous undertaking.
Almost half (49%) of enterprise devices are being used without any managed update policy and about 40% of organizations surveyed said they had experienced a mobile-related compromise.
— Verizon Mobile Security Index 2020
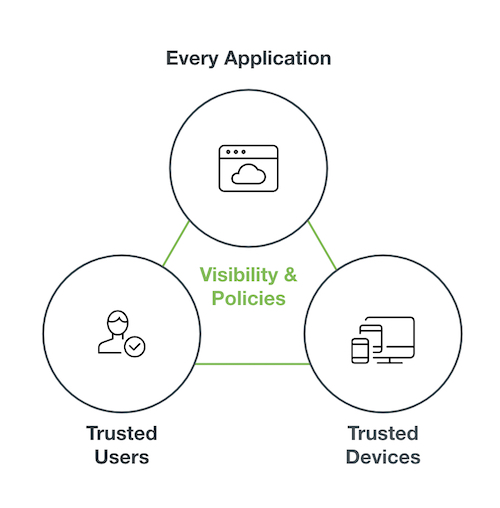
Consistently applying policies for managed and unmanaged devices and having the capabilities to verify the trustworthiness of a device is essential to protecting an organization from risk while providing seamless access for the diverse workforce.
Simplifying Device Trust
Duo is known for democratizing security with easy to use multi-factor authentication, but we haven’t stopped there. Knowing which devices to trust and who is accessing your applications is a key tenant to achieving a zero trust framework. Duo is committed to making this security framework simple and achievable for businesses of all sizes.
Duo is tackling the complicated endpoint problem by developing solutions that help solve the challenges around establishing trust in devices regardless of their management status. To that effect, we are delighted to announce exciting new Device Trust capabilities that build on the functionality that Duo has been offering - Device Insight and Trusted Endpoints. The new capabilities further help organizations minimize their risk surface by verifying trust and enforcing security policy compliance across any device that requires access to corporate applications.
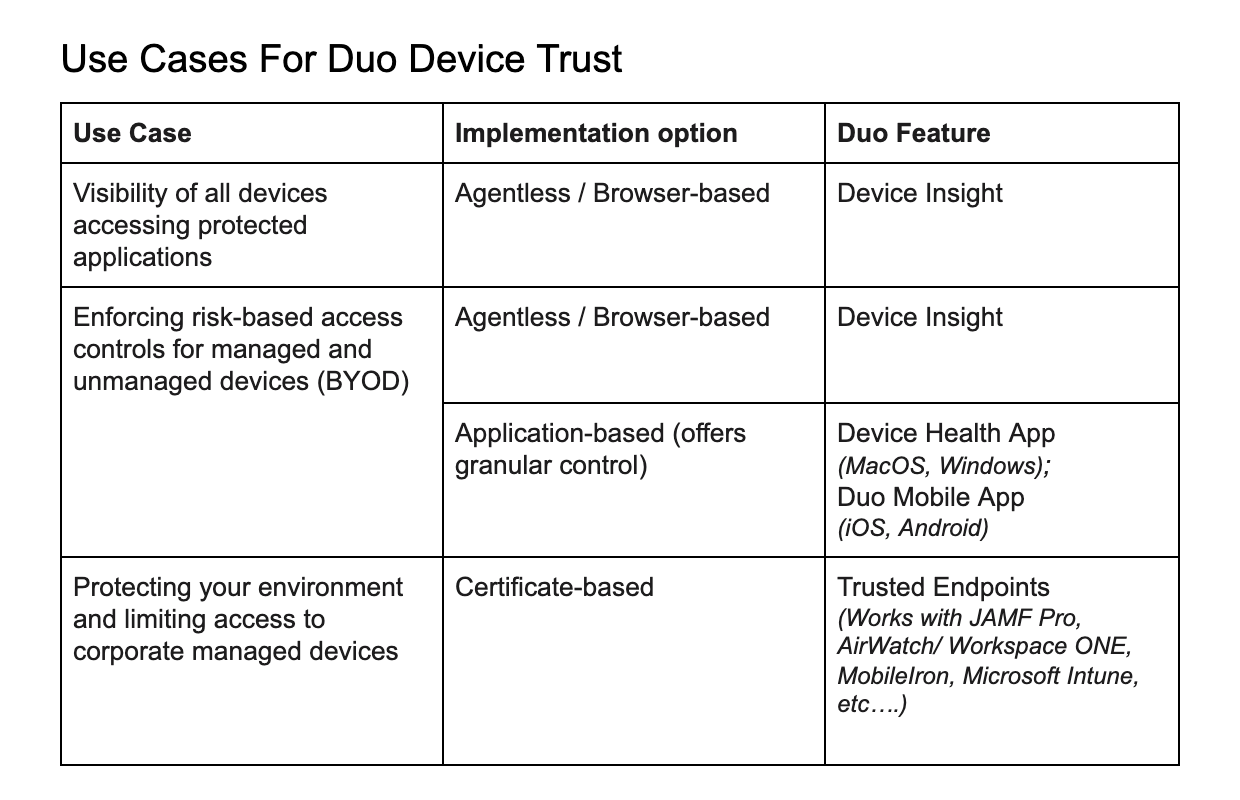
The following new device trust capabilities make it easy for organizations to assess the health and security posture of any device (managed or unmanaged), on any platform (Windows, MacOS, iOS and Android), and enforce adaptive access control policies in order to reduce risks of security and non-compliance.
Verifying Trust on Managed and Unmanaged Devices
Duo's Device Health application gives organizations control over which laptop and desktop computers can access corporate applications based on device security — even if that device is not controlled by corporate management systems and/or isn’t directly on the corporate network. Customizable access policies can block access if the device is unhealthy or has a weak security configuration, and provides self-remediation options to users so they can address issues themselves alleviating the burden on helpdesks.
Organizations can prevent a breach caused by vulnerable devices, while protecting all users accessing any application, from any location. With Duo, you can prevent malware infection, identify shadow devices on your network, block risky devices and protect access to your data.
Existing Duo Access customers can set policies to require Duo Health App and verify device posture before granting access. And existing Duo Beyond customers can additionally set policies to verify the presence of one of the following AVs.
Cisco AMP for Endpoints
CrowdStrike Falcon Sensor
Symantec Endpoint Protection
Windows Defender
Device Health application is available on Windows and Mac OS platforms.
Extending Trust to Devices Managed by Microsoft Intune
Device trust for the enterprise often extends even further with more complex IT environments with managed devices. Through our partnership with Microsoft we have extended our Trusted Endpoints capabilities to integrate with Microsoft Intune, helping organizations to set adaptive access policies around unmanaged endpoints (BYOD) and managed endpoints based on their enrollment status with Microsoft Intune.
This feature will be supported on Windows, iOS and Android platforms and existing Duo customers can reach out to their reps to participate in the beta program
Block Infected Devices Using Cisco AMP for Endpoints
The modern workforce prefers to work in a variety of places outside of the normal office, which may include unsecure networks which could potentially expose devices to additional risk of malware and ransomware. To address this scenario we have integrated with AMP for Endpoints, which allows administrators to enforce a Trusted Endpoint policy. This provides the ability to automatically block access to Duo protected applications from devices that are running AMP and have been flagged in AMP as an infected endpoint containing malware. This automates the response to an infected endpoint device, preventing the propagation of malware and reducing the risk of data breaches. Since Duo only blocks the infected device, the user can access the application from a different device that passes the trust checks as per policy and be productive.
This feature is now generally available and supported on Windows and MacOS platforms. Existing Duo Beyond customers can leverage this feature along with Cisco AMP.
3 Reasons Customers Choose Duo for Device Trust
Duo offers the most comprehensive device trust capabilities in the market today that is easy to use for end-users and simple to manage for administrators.
Duo’s unique approach to verifying the trustworthiness of devices caters to a wide variety of use cases and a diverse population of workforce devices.
Duo helps organizations to improve security in a manner that is user friendly and enables productivity. Users are empowered with self remediation for out of policy devices, so security does not interrupt daily tasks.
For organizations, all this translates to reducing cyber risk while enabling productivity and realizing lower total cost of ownership.
Get started with Duo Device Trust today, sign-up for a free trial now.
For details on pricing and packaging, click here.
Watch on-demand webinars to learn why Device Trust is important and how Duo can help.


