How Duo Does Duo
Duo Security is the first customer of Duo Security. We eat our own dog food, so to speak; that is, we use Duo to protect Duo, because how can we expect customers to trust Duo without also exceeding the expectations of our own employees? Duo Beyond, which enables secure access to all applications, for any user, from any device, anywhere, is a central pillar of our information security program.
It should come as no surprise that weak authentication is the number one cause of breaches today. Duo utilizes its own product to protect its business and customer data.
Duo can be configured to be flexible enough to fit into any organization. Internally, we’ve made policy decisions to keep our company as secure as possible from the risk of credential compromise while still providing an accommodating and convenient end-user experience.
Factor Choices
We want security at Duo to be something that our users enjoy participating in rather than an unnecessary obstacle to getting their work done. So while we do only allow the strongest factors, these are also the ones that require the least amount of an end user’s time. On day one, every Duo employee receives a hardware U2F token and enrolls it along with their mobile device using the Duo Mobile application. U2F and WebAuthn are the strongest authentication methods available today, and they are also the most convenient from an end user’s perspective. U2F and WebAuthn, however, only work in the context of a web browser, so we also utilize Duo Push which is secure, convenient, and gives us insight into the security hygiene of our users’ phones so that we can ensure devices are healthy before they are allowed to access Duo systems.
Duo Mobile passcodes, phone callback, hardware tokens, and SMS-delivered passcodes are less convenient for the end user and introduce friction into the authentication process. In addition, these factor choices do not provide security properties that are as strong as Duo Push and U2F.
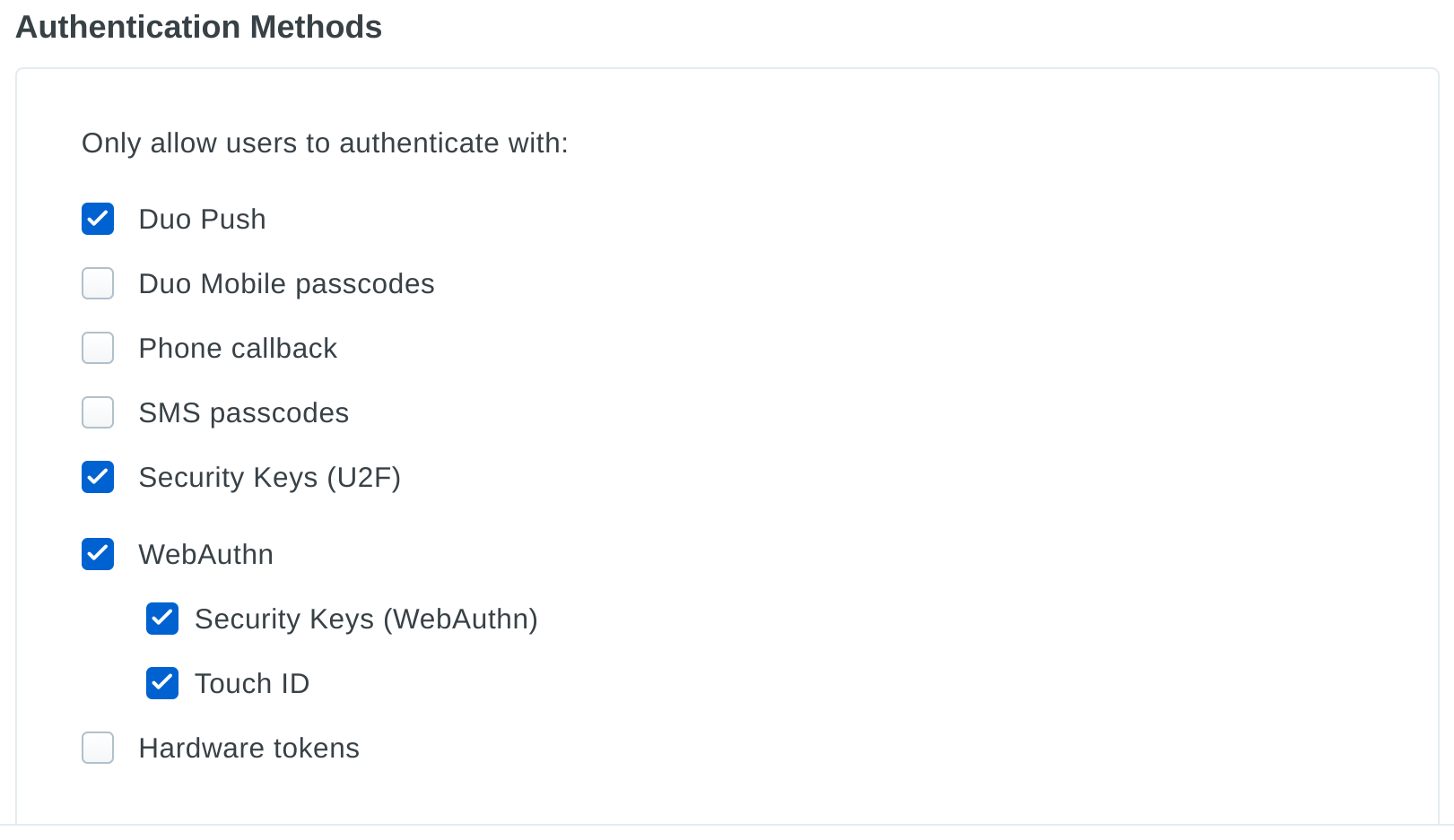
Policy Decisions
In Duo Access and Beyond editions, administrators can make a number of policy configurations to improve the experience for their end users. For example, enabling the “Remembered Devices” policy will reduce the amount of friction users encounter by allowing them to reauthenticate less frequently from devices that recently accessed Duo-protected applications, without sacrificing security.
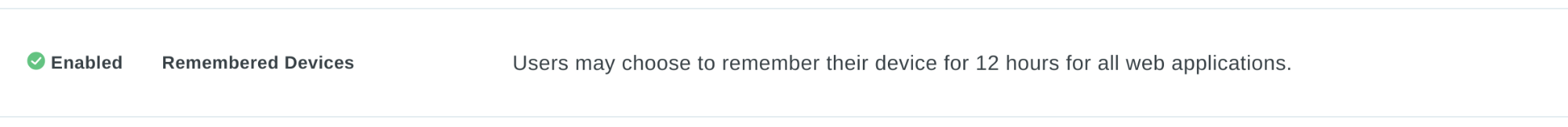
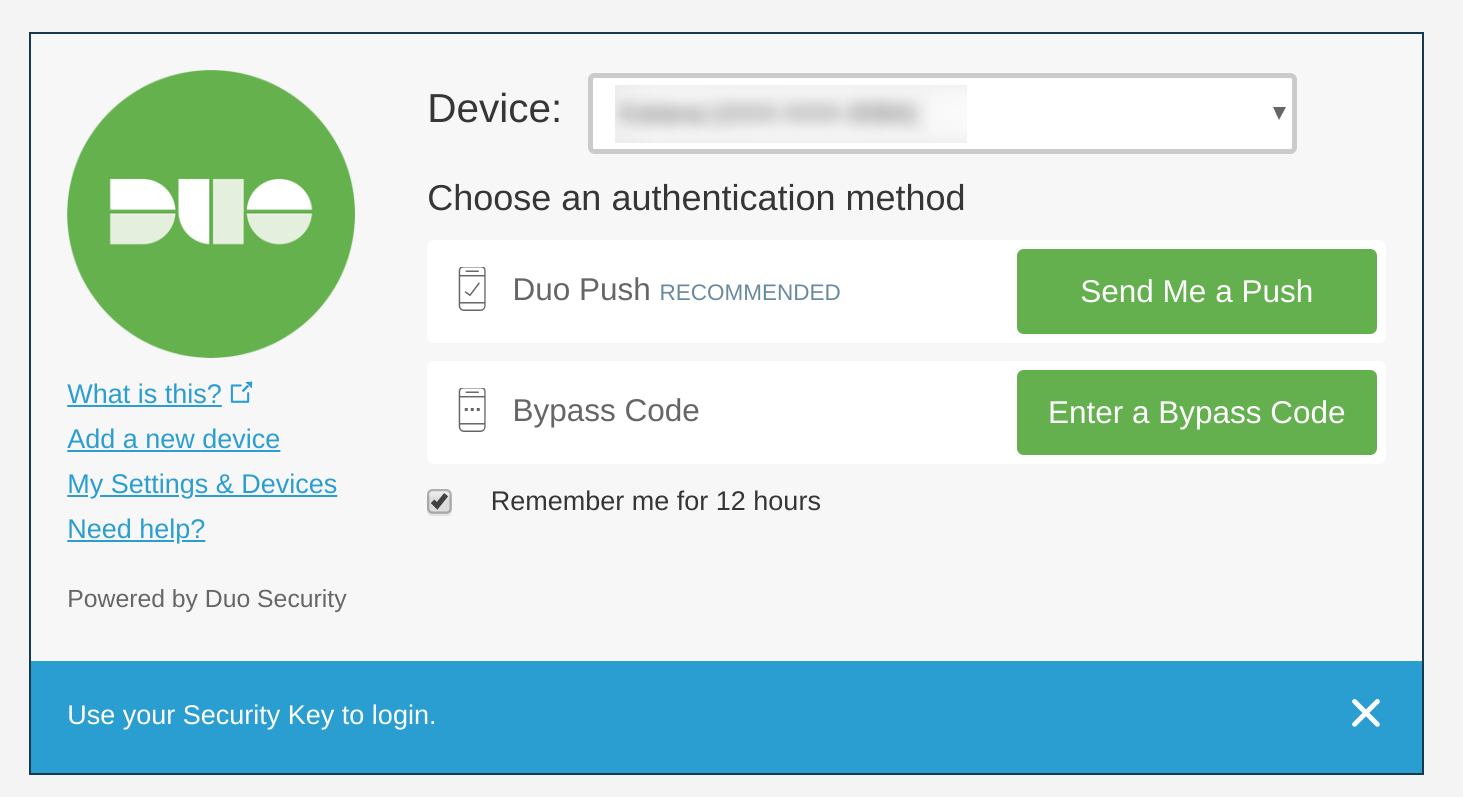
Because we encourage our users to use Duo Push, we can also ensure that their mobile devices are configured in a secure manner, and up-to-date with the latest security patches. When critical security updates to mobile devices become available, we are able to apply a more aggressive policy to ensure that devices are updated before accessing any Duo systems. We pair these more aggressive update requirements with internal communications so our end users are aware of the importance of upgrading as soon as possible.
Duo also utilizes the Trusted Endpoints feature, which requires the device to be managed with our security tooling in order for it to access our critical applications. This provides one final failsafe in the event of a multi-factor compromise.
Sometimes edge cases come up where we need to deviate from our normal policies. For example, there may be a legitimate need for a Duo-protected application to support an additional authentication method. Because we’re able to apply policy on a per-application and even per-group basis, it’s easy for us to create new policies that empower us to enable business without opening up the factor to the rest of our users or systems.
Detection and Alerting
Duo’s authentication logs provide us with a unified single point of visibility across all of our systems (and using the same timezone!), enabling one-stop shopping for critical authentication information during investigations. We pull our logs into our centralized SIEM to enable automated security response activity and to identify trends such as which factors are most popular with which users to identify policy improvements. For example, if we found that users never accessed a Duo-protected application, we could assume that it is safe to deprecate that application. These logs also give us the ability to raise alerts and respond when our end users report fraud or when their account becomes locked out (these could indicate a compromise of primary credentials).
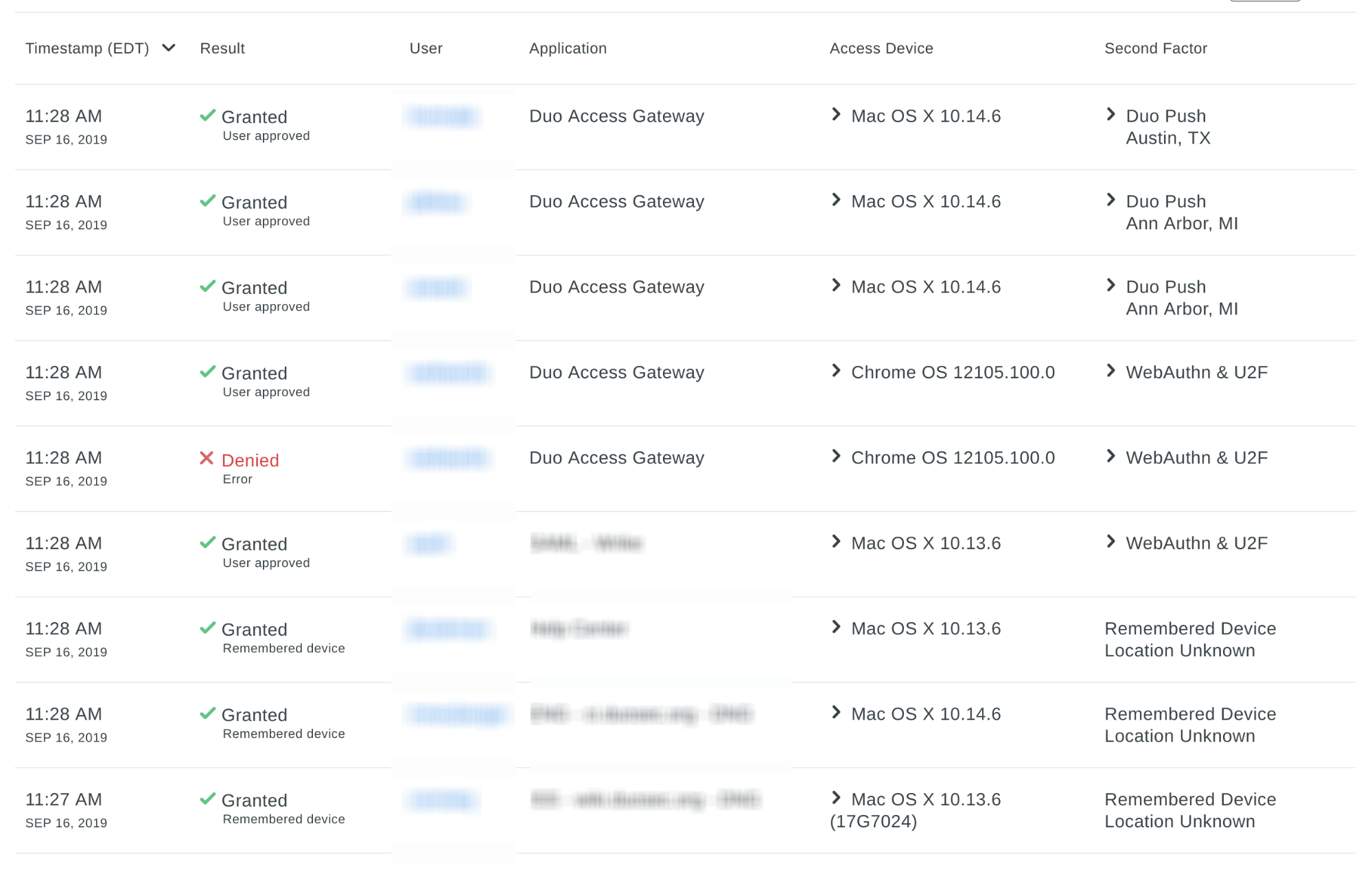
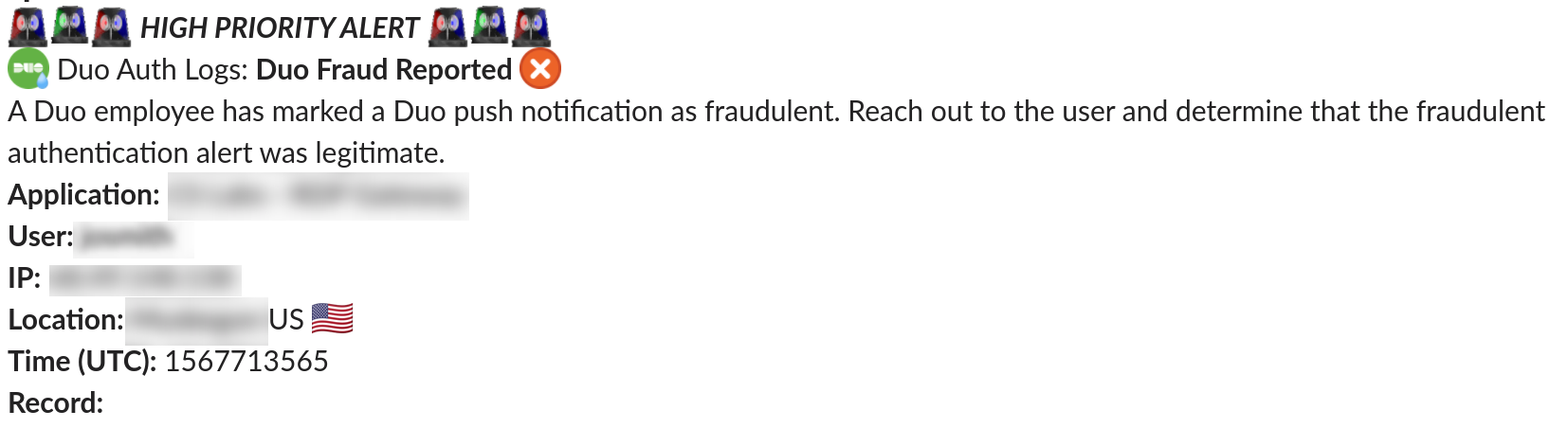
Each organization that uses Duo will have different needs and risk tolerances, which is why Duo provides the flexibility to right-size security and convenience with application and group level precision. It is important for Duo administrators to regularly review factor choices, policies, and the authentication logs in order to make policy decisions that continue to reflect the organization’s risk appetite.
Zero Trust: Going Beyond the Perimeter
A zero-trust approach shifts the secure perimeter to any place where you make an access control decision and prompts you to question your assumptions of trust every time there’s an access event.
In this guide, Zero Trust: Going Beyond the Perimeter, we examine the genesis of the zero-trust approach and introduce the three pillars of zero-trust security.
Free guide
