Securing Cloud Access With IAM & Two-Factor Authentication
According to the Cloud Security Report 2015 from Alert Logic, cloud environments are mostly affected by significantly increased numbers of app attacks, suspicious activity and brute force. The largest increase seen was in app attacks, which grew 45 percent over the last year, now accounting for 70 percent of attacks against cloud environments.
For on-premises data centers, brute force attacks saw a decrease in frequency. Many of these attacks targeted WordPress and SSH, with login attempts coming from scripts running on compromised devices. Most of the exploits also leveraged vulnerable plugins and themes.
Brute force attacks can be difficult to block, as an attacker can target a network with username and password combinations from many different/changing IP addresses, making it difficult for organizations to block these types of attacks.
With the continued increase in migration to the cloud for infrastructure support, attacks have increased accordingly for Alert Logic’s customers that use cloud environments.
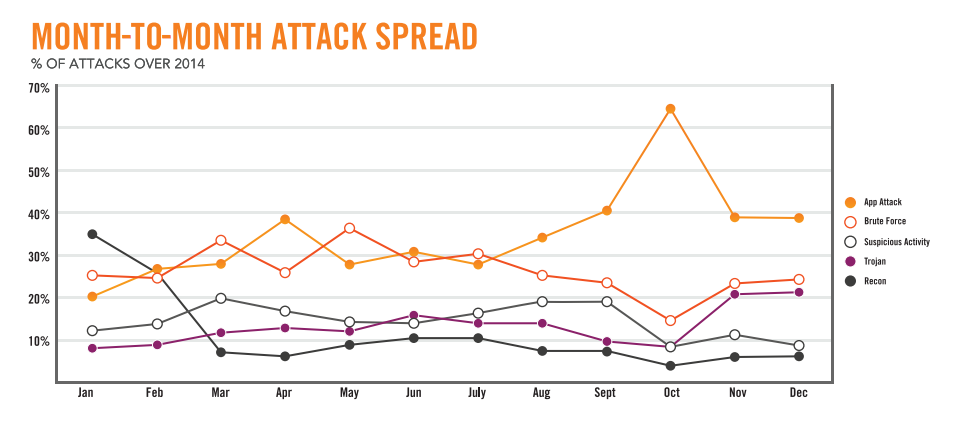
Since applications provide a gateway to sensitive data, app attacks continue to increase in popularity for attackers, targeting traditional websites, mobile apps and more. Alert Logic named a few industries that are affected the most by app attacks, including the transportation and public utilities sector and the real estate industry.
App and brute force attacks also affect the financial services industry, as they continue to adopt Internet-enabled services with website account access, mobile banking applications, SMS/text-based banking and email-based services.
Application attacks target financial service companies’ databases and backend systems, while brute force attacks can give attackers access to internal systems that allows for lateral movement from within.
Quit Storing Secret Keys in the Cloud
The report also focused on the disclosure of sensitive data, including theft of cloud credentials, security keys and API keys which attackers may find by scanning public code repositories like GitHub and Bitbucket.
Last year, Amazon Web Services (AWS) advised that developers on GitHub checked to ensure they didn’t accidentally expose their login credentials, as Australian ITNews.com reported. Apparently, a search on GitHub revealed that thousands of AWS secret keys could be found in plain text, allowing anyone to access those AWS accounts.
The Cloud Security report recommends never storing this type of sensitive cloud data in a public forum or code repository, and also recommends that if any credentials, keys or tokens are made public, they should be replaced immediately on all systems.
With access to those accounts, an attacker can delete files and destroy entire accounts - a disturbing thought for any developer that may be working on applications for corporations. Or, developers/organizations can get hit with major bills for bandwidth usage, as attackers have been known to use AWS credentials to spin up and run unauthorized servers.
AWS Credentials: Where You Least Expect Them
There are a few cautionary tales out there - like the WordPress developer that got a $6,000 bill for 600 servers running on his Amazon Elastic Compute Cloud (EC2) instances after he unknowingly uploaded a WordPress file with his AWS credentials to GitHub, with the intent to open source his website and learn from other developers.
While he had removed the wp-config.php file containing his AWS keys before uploading it, there was yet another file he didn’t check - wp-config.php.save - that also contained his access keys.
Securosis Analyst and CEO Rich Mogull blogged about getting notified by Amazon after they found his AWS access and secret key were publicly available on GitHub. He located his keys in a commented code section in a test file he had uploaded - somewhere he hadn’t thought to look previously.
Malicious hackers had located his credentials within 36 hours after he created and uploaded the files on GitHub, and started running unauthorized EC2 instances soon after, racking up charges on his account.
Securing Cloud Access Keys and Reducing Risk
Amazon does offer Identity and Access Management (IAM) to control different users and groups that have access to your AWS resources, which is basically role-based access control. That allows you to manage your users’ permissions and access, allowing you to reduce the risk involved should their credentials get stolen.
Developers can also implement multi-factor authentication on any cloud accounts, which can stop remote attackers from accessing cloud resources. Using a mobile authentication app is the easiest and most effective way to secure cloud access - logging in requires one-tap approval via push notification, faster than typing in a passcode.
Another easy method is the use of U2F tokens, which allows developers to tap a small USB device on their machine and log in immediately.
Find out how modern two-factor authentication solutions can help you deal with new risks introduced by the cloud, BYOD, mobile and more in our Two-Factor Authentication Evaluation Guide.

