The Evolution of Security #4: Two-Man Rule
Information security has, by necessity, changed a lot from a strategic perspective. From physical walls to encoded maps to locks and chains, the way we defend against the age-old criminal must evolve to support the ways we interact with data today.
Now, as we enter into an era of Security 3.0 that must grapple with new security challenges introduced by BYOD (Bring Your Own Device) and the cloud, what kind of security solution can we turn to in order to protect our private company data?
Stay tuned: The answer will be revealed April 14!
Duo’s Creative team has taken on the task of depicting security throughout the ages with a series of original illustrations. Here’s the fourth in our Evolution of Security series:
How to Launch a Nuclear Missile
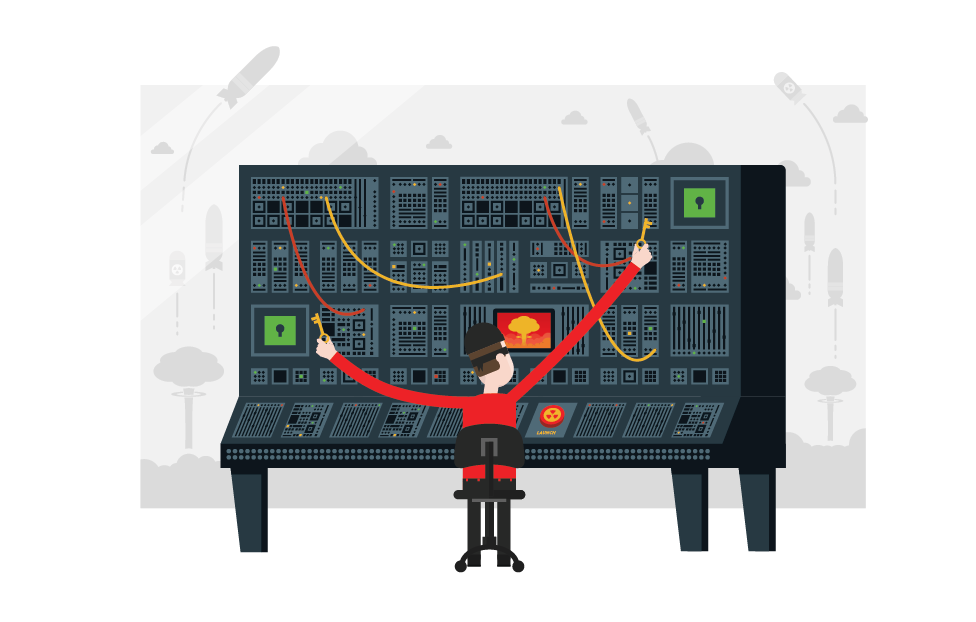
What’s better than one key? Two keys, held by two different people. This was the reasoning behind the two-man rule, developed by the U.S. Air Force to protect initializing launch of nuclear weapons.
Once a launch order is confirmed, two operators must validate the order by comparing an authorization code, found in a special sealed envelope - stored in a metal safe and locked with two separate locks.
Each operator has the key to open only one lock - meaning no one individual can open the safe and initiate launch alone. Plus, the keys must be engaged simultaneously. And, the keyholes are positioned too far apart to be initiated by a single person - circumvented only by a human Stretch Armstrong.
Stay tuned to see the next phase of security evolution tomorrow!

