The Evolution of Security #6: Local Only
Information security has, by necessity, changed a lot from a strategic perspective. From physical walls to encoded maps to locks and chains, the way we defend against the age-old criminal must evolve to support the ways we interact with data today.
Now, as we enter into an era of Security 3.0 that must grapple with new security challenges introduced by BYOD (Bring Your Own Device) and the cloud, what kind of security solution can we turn to in order to protect our private company data?
Stay tuned: The answer will be revealed April 14!
Duo’s Creative team has taken on the task of depicting security throughout the ages with a series of original illustrations. Here’s the sixth in our Evolution of Security series:
Security 1.0: On-Premises Software, Servers & Employees
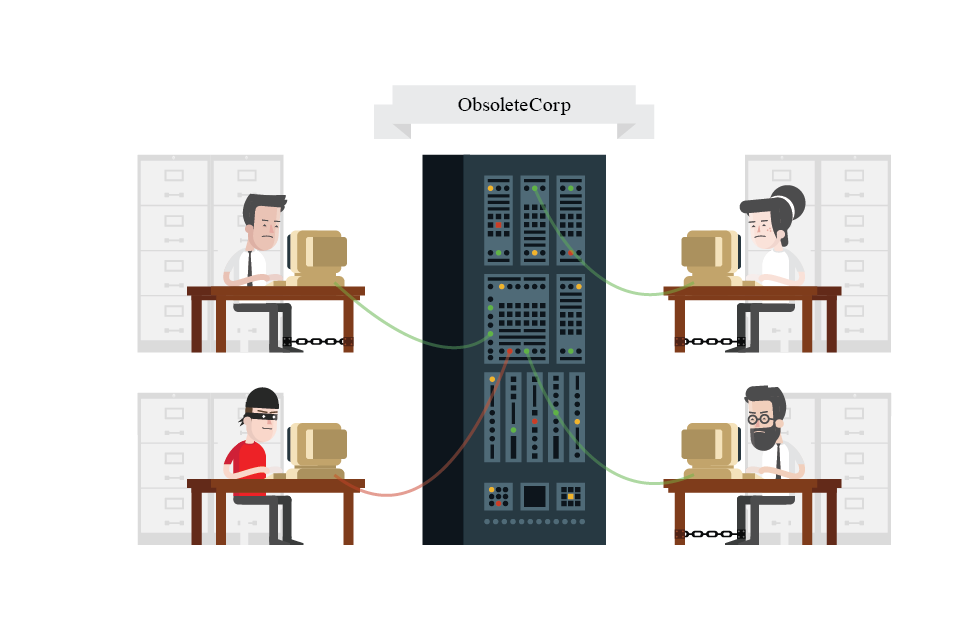
In the advent of Security 1.0, companies kept their data safe behind the gated walls of a corporate network. Employees must be wired into their company networks to access corporate resources, essentially chaining them to their desks.
Enterprise software is also deployed on-premises, installed on PCs and hosted by in-house servers housed in locked server closets. Companies must build and operate underlying computing infrastructure, buy software licenses, and hire in-house tech support personnel to keep their systems running
But malicious hackers can exploit system vulnerabilities in order to gain access and connect remotely to corporate networks, effectively stealing your company secrets.
This environment has called for the typical perimeter-based security solutions, including firewalls, antivirus and intrusion detection solutions. But those alone aren’t enough to stop the power of one stolen password...
Stay tuned to see the next phase of security evolution tomorrow!

