The Evolution of Security #8: Cloud & BYOD (Bring Your Own Device)
Information security has, by necessity, changed a lot from a strategic perspective. From physical walls to encoded maps to locks and chains, the way we defend against the age-old criminal must evolve to support the ways we interact with data today.
Now, as we enter into an era of Security 3.0 that must grapple with new security challenges introduced by BYOD (Bring Your Own Device) and the cloud, what kind of security solution can we turn to in order to protect our private company data?
Stay tuned: The answer will be revealed April 14!
Duo’s Creative team has taken on the task of depicting security throughout the ages with a series of original illustrations. Here’s the eighth in our Evolution of Security series:
Security 3.0: A Time of Complete and Utter Chaos
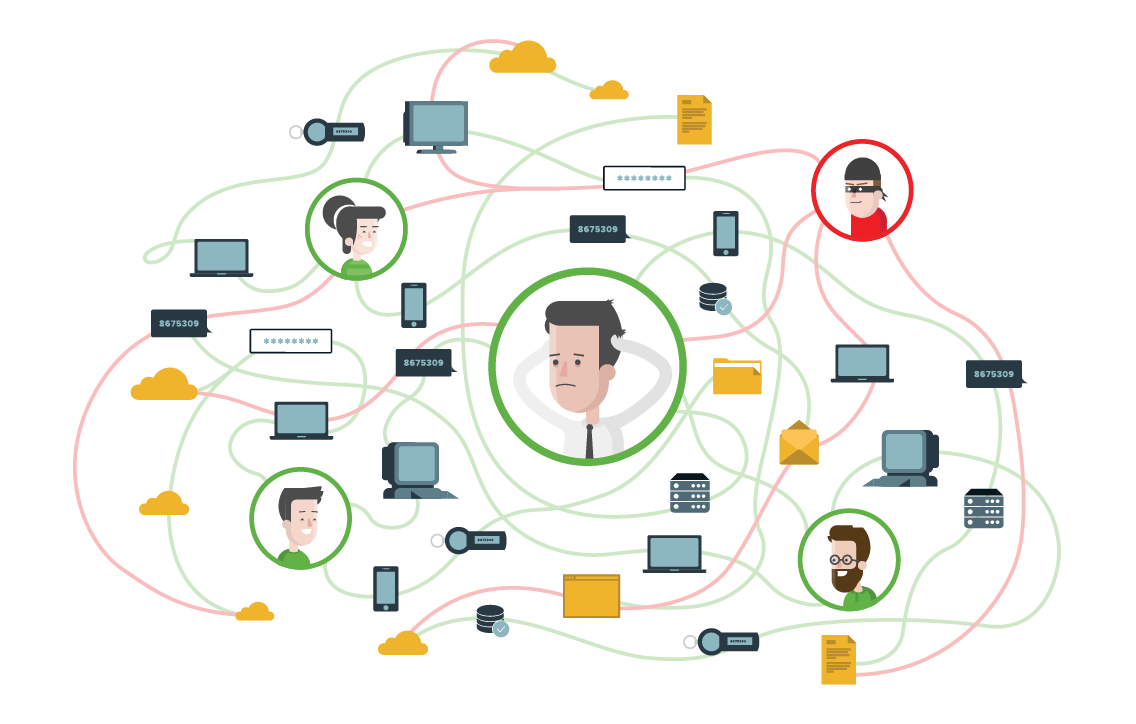
Security 3.0 must grapple with the chaos of the cloud and an ever-growing number of personal devices, applications, networks and users that comprise the modern IT environment.
Cloud, or web-based applications serve up email, business and productivity services without wires. Scalability, flexibility and affordability means more businesses are transferring their operations to the cloud.
But, though the cloud eliminates the need for on-premises software, hardware, and in-house computing infrastructure, it’s still vulnerable to age-old access risks. When combined with BYOD (Bring Your Own Device), there’s plenty to manage when you’re trying to keep valuable business data secure.
To get access to that valuable data, attackers are targeting end users directly, stealing passwords and breaching critical business systems.
Learn about our Security 3.0 solution - to be announced tomorrow!

