Unpacking 2020’s Verizon DBIR - Human Error and Greed Collide

Pick up your device, and lean into your screen because the numbers are in for the 2020 Verizon Data Breach Investigations Report (DBIR). This year celebrates the report’s 13th by monitoring security in 81 contributing organizations, four global regions and 16 different industry verticals. The report reviews 32,002 security incidents and analyzes 3,950 confirmed data breaches, and is complete with interactive data points.
At a Glance
86% of breaches driven by financial gain (up 15% from 2019)
70% of breaches are caused by bad actors (with 55% of these in organized crime)
67% of breaches were due to credential theft, errors and social attacks
27% of malware incidents are from ransomware, and that threat is rising
43% of breaches are due to web app attacks (double from 2019)
58% of breaches involve personal data (double from 2019)
17% of breaches are caused by errors (double from 2019)
Financial gain is still the primary motive for attacks
North America leads other regions in the amount of breaches
43% of data attacks are cloud-based (double from 2019)
On-going patching is a successful deterrent with fewer than 1 in 20 breaches exploiting vulnerabilities
Password dumper is the most popular form of malware followed by capture app data and ransomware
Office documents and Windows apps still tend to be the malware file type of choice. Other file types seen as malware delivery mechanisms include shell scripts, Java, PDF, browsers app, Flash, Linux app, OSX app and Android app
Denial-of-Service (DoS) attacks have gone up over the past year, while cyber-espionage campaigns have decreased
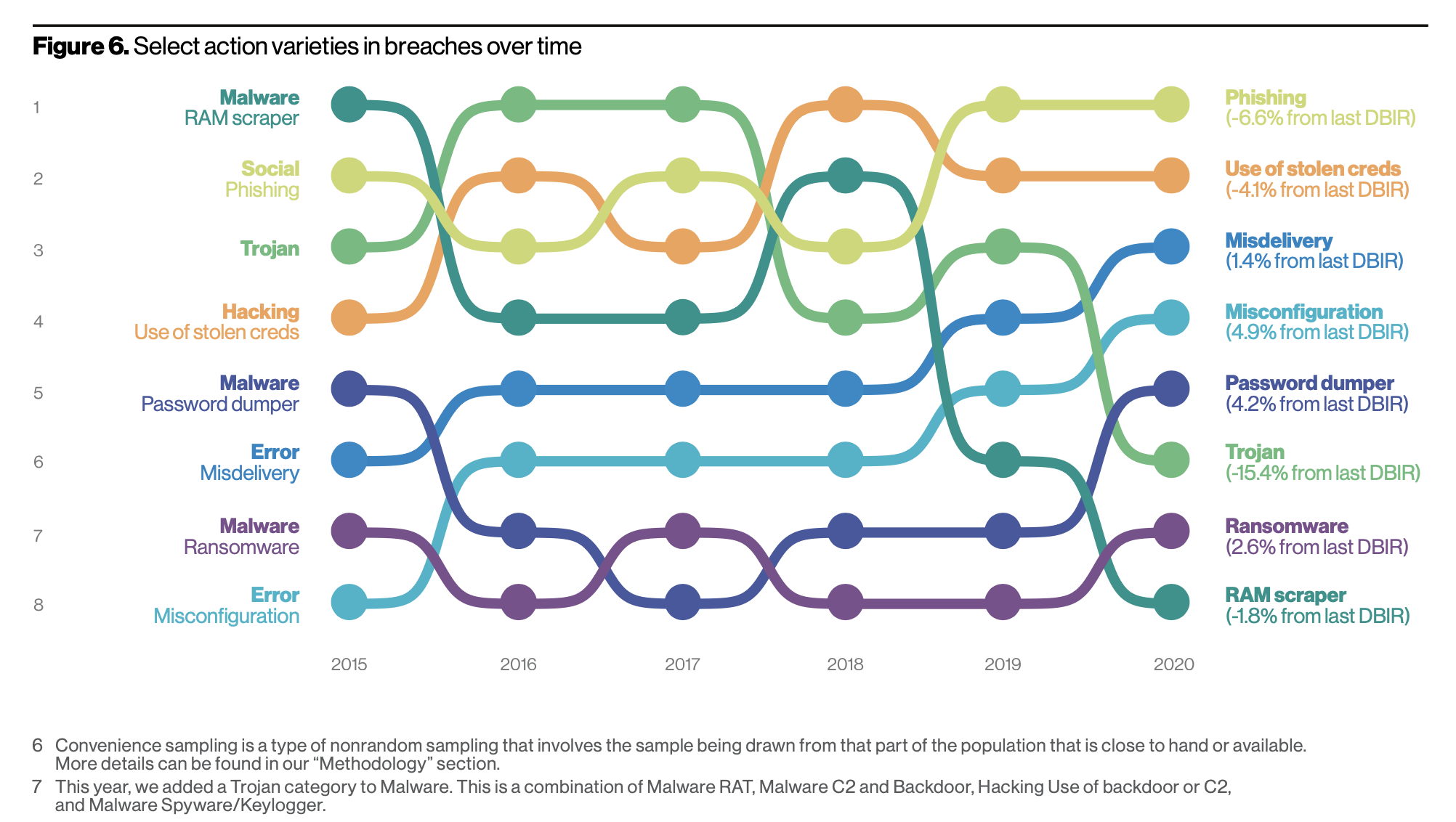
Phishing and Stolen Credentials Still Top Driver of Breaches
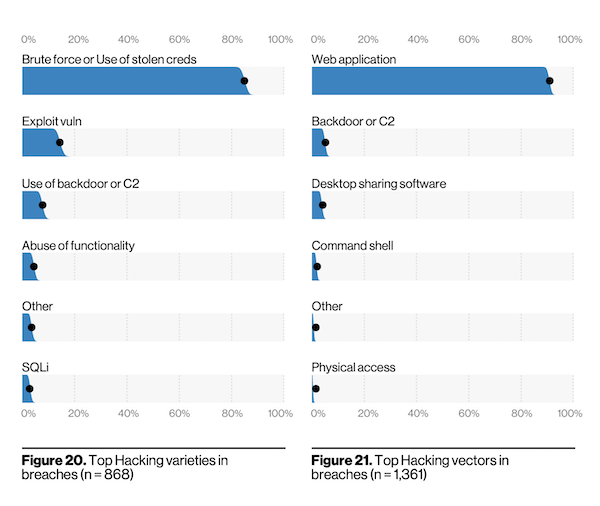
Phishing and stolen passwords continue to be top ways that cyber criminals are accessing networks and systems. Over 80% of hacking breaches involve brute force or the use of lost or stolen credentials. Hacking coupled with exploitation of a vulnerability is a main way bad actors access web applications (through stolen credentials) and gain entry.
Although down 6.6% from 2019, social phishing remains the top access point for breaches, followed by stolen credentials from hacking, which is down by 4.1% from last year. Social attacks are sent via email 96% of the time, with 3% through the web and slightly over 1% via mobile or SMS.
If the DBIR has taught us nothing else is that we need to accelerate the denouement for the ignoble static password. According to the report, over 80% of the attacks involved brute force or the use of stolen passwords. If we can collectively shift towards utilizing multi-factor authentication, while keeping an eye towards of future with passwordless technology such as WebAuthN and biometrics, we will embrace a safer future.
— Dave Lewis, Duo’s Advisory CISO
It is worth noting the click-through rate in phishing simulations has gone down from an average of 25% to 3.4% in the past 7 years as more users are educated on security best practices. This shows despite human error we can be trained to do better. Reporting the results of phishing test campaigns is also increasing. Passwords that are easily detectable or reused often are vulnerable to phishing attacks. With security education and multi-factor authentication (MFA) the trail of breaches due to stolen passwords can be prevented 99.9% of the time.
Attackers targeted credentials, personal data, medical records, payment information, internal secrets and other internal business-related data.
37% of credential theft breaches use stolen or weak credentials
25% involve phishing
16% from password dumps
Human error accounts for 22% of breaches
20% of attacks are against web applications using stolen credentials
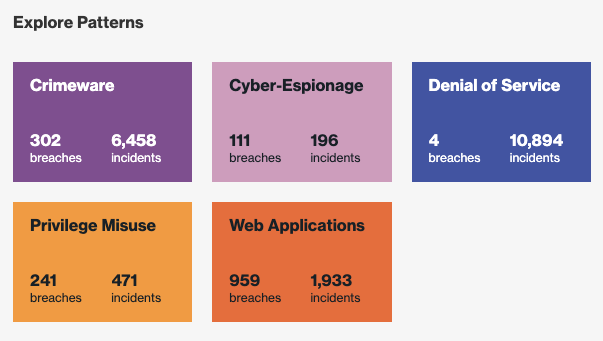
Cyber-Breach Pathways Lead to a Defender Advantage
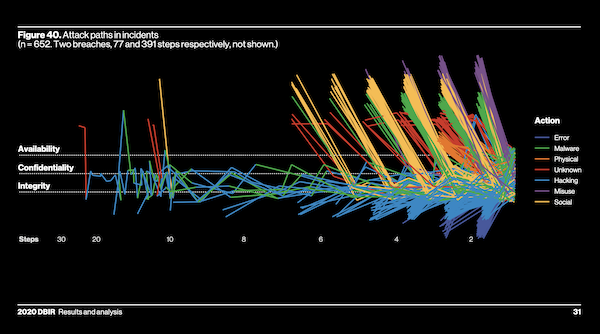
The 2020 DBIR introduced cyber-breach attack pathways that document the steps (typically under 10 steps) used in a breach or incident, or a holistic view of the attackers’ “journey to a breach.” By documenting the steps an attacker takes to systematically work their way through the network and expand their persistence, it sheds light on the areas of vulnerability and provides a “defender advantage” on where you choose to intercept them. If you want to stop them before they start, two-factor authentication (2FA) is the most effective solution.
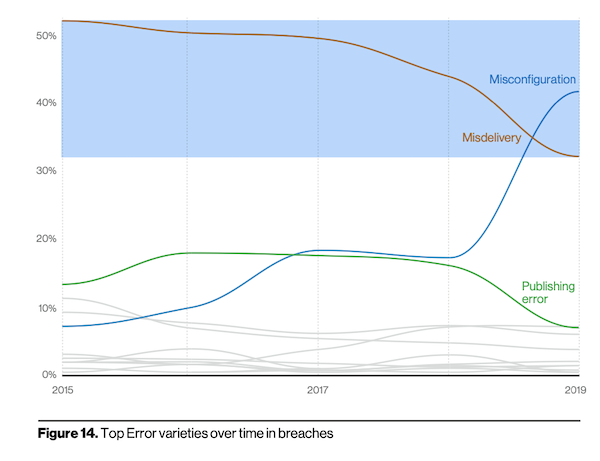
Errors Double
The report shows a significant increase in internal errors-related breaches, which increased by 2x, although that might be due to stricter reporting. Misconfiguration errors also doubled, and successful social engineered attacks are up 18%. Errors are most often discovered by a security researcher or third-party. Of breach origins, 17% are created by errors.
Breaches from malware stealing passwords and password dumps have gone up 4.2% from 2019. Breaches from errors and misdelivery are up 1.4%, while errors from misconfiguration are up 4.9% from last year. Financially Motivated Social Engineering (FMSE) impersonating or targeting CEOs (without malicious links but with the goal of a money wire) continues to increase significantly year over year.
“It’s not personal, it’s business.” —The Godfather
Security breaches are big business, with 70% driven by external actors and 55% of those carried out by organized crime; followed by nation-states, system admins and end users, which all sit at under 20%. Physical breaches have leveled, but hacking, malware, social and misuse have decreased since 2019. Hacking with stolen credentials and social phishing are down from 2019, but remain consistent and the top threats. Malware breaches have gone down, primarily because the accessible pool of stolen credentials makes malware no longer necessary. Take this news with a grain of salt, however, as ransomware is higher than last year, up 2.6%, and while it is considered malware, it is difficult to confirm as a breach without credentials, but easier to track as an incident.
DoS attacks made up 40% of security incidents reported, more than crimeware and web applications. DoS attacks can send junk network traffic via bots to overwhelm and crash systems.
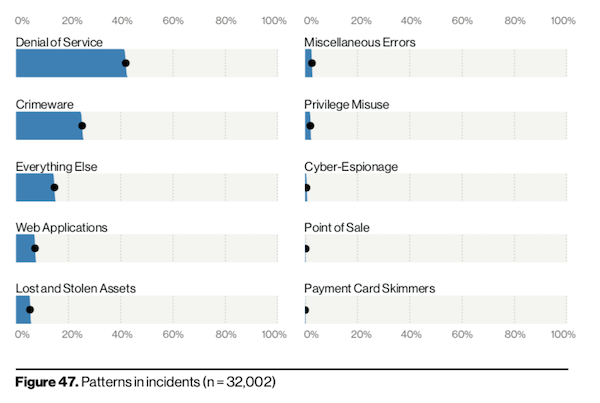
When we look at criminal forums and underground data, 5% refer to a “service.” That service could be any number of things including hacking, ransomware, Distributed Denial of Service (DDoS), spam, proxy, credit card crime-related or other illicit activities. Worse still, that “service” may just be hosted on your hardware. The simple fact is this: If you leave your internet-facing assets so unsecured that taking them over can be automated, the attackers will transform your infrastructure into a multi-tenant environment.
— 2020 Verizon DBIR
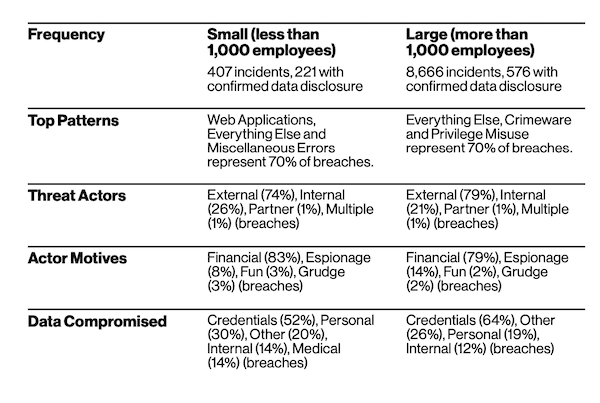
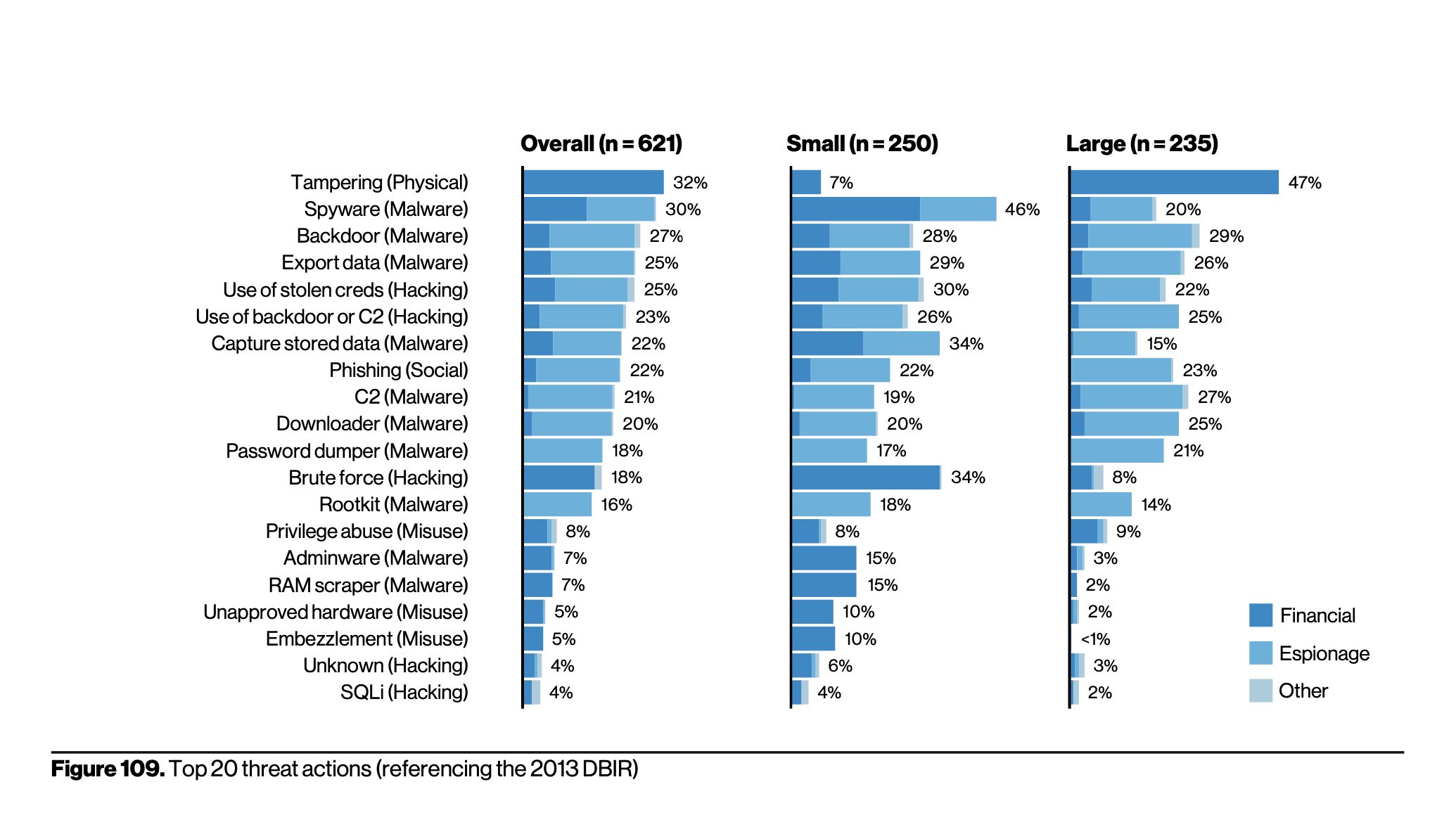
Small Versus Large Business
Bad actors target businesses using cloud-based tools. Misconfiguration errors and human errors have made this area lucrative for hackers. Small businesses need to get smarter about phishing, as they fell victim to 30% phishing-related breaches, 27% were stolen credentials and 16% password dumpers. These were the main vulnerabilities for large companies as well in 2020. Point-of-sale (POS) attacks decreased this year as user devices, mail servers and people were the main targets for attacks.
Industry-Specific Findings
Since 2019, web application attacks have increased significantly, both in terms of percentage and in raw number of breaches. Ransomware is on the rise at 27%, and phishing still works.
Public Administration: 346 confirmed data disclosures. Miscellaneous errors, web applications and everything else represent 73% of breaches, with 59% of threats from external actors, 51% of personal data was compromised and 61% of incidents due to ransomware.
Professional Services: 326 confirmed data disclosures. Web applications led with 75% of threats from external sources, and 75% of breaches stole personal data and 45% stole credentials.
Manufacturing: 381 confirmed incidents, 75% are external actors and 29% use password dumpers, app data captures and downloaders to obtain proprietary data. Crimeware, web applications and privilege misuse account for 64% of breaches. And 23% of malware incidents are from ransomware.
Financial and Insurance: Misuse dropped from 21.8% in 2019 down to 8%. Over 30% of breaches were caused by web application attacks using stolen credentials to get data stored in the cloud. But also troubling is that miscellaneous errors attributed to employee errors resulted in just as many breaches.
Educational Services: Ransomware attacks continue to plague education with 80% malware attacks vs. 45% in 2019, and social engineering accounted for 27% of incidents.
Healthcare: Human error created 31% of breaches from misdelivery and misuse, with external breaches at 51% (a 10% increase from 2019). Almost half of the bad actors come from the inside at 48%, making this vertical is susceptible to credential theft.
Retail: 99% of incidents were financially-motivated, with payment data and personal credentials continuing to be prized. Web applications, rather than POS devices, are now the main cause of retail breaches.
As remote working surges in the face of the global pandemic, end-to-end security from the cloud to employee laptop becomes paramount. In addition to protecting their systems from attack, we urge all businesses to continue employee education as phishing schemes become increasingly sophisticated and malicious.
—Tami Erwin, CEO, Verizon Business.
Regional Findings
Northern America: Stolen credentials were used in over 79% of hacking breaches; 91% of cases were financially-motivated; 33% of breaches were associated with either phishing or pretexting.
Europe, Middle East and Africa: DoS attacks made up for more than 80% of malware incidents; 70% were financially-motivated; 40% of breaches used a combo of hacking that leverage either stolen credentials or known vulnerabilities to target web applications and 14% of breaches were from cyber-espionage.
Asia Pacific: Only 63% of breaches were financially-motivated, and 28% were the result of phishing attacks.
When greed (bad actors) meets human error (phishing and stolen credentials) — vulnerabilities and exploits happen. Duo helps companies by taking the guesswork out of many of the human errors that lead to stolen credentials through multi-factor authentication combined with Duo's zero trust controls that allow administrators to make effective policies. Duo's device trust helps organizations get clear visibility into devices accessing the network and provides additional layers of protection with prompts for users to keep their devices up-to-date, and barriers to access if their device poses a risk. Duo offers powerful security that is easy to deploy and easy to use. We help your users stay secure with minimal friction.
Try Duo For Free
With our free 30-day trial and see how easy it is to get started with Duo and secure your workforce, from anywhere and on any device.


