Understanding Identity Acronyms: What Are ISPM & ITDR?
The challenge: Limited visibility
Not all new software categories are created equal.
Cisco Talos reported in February that three of the top five MITRE ATT@CK techniques used in 2023 were identity-based, so identity needed some focused security attention.
Why? Access and identity sprawl is creating new security challenges for organizations of all sizes:
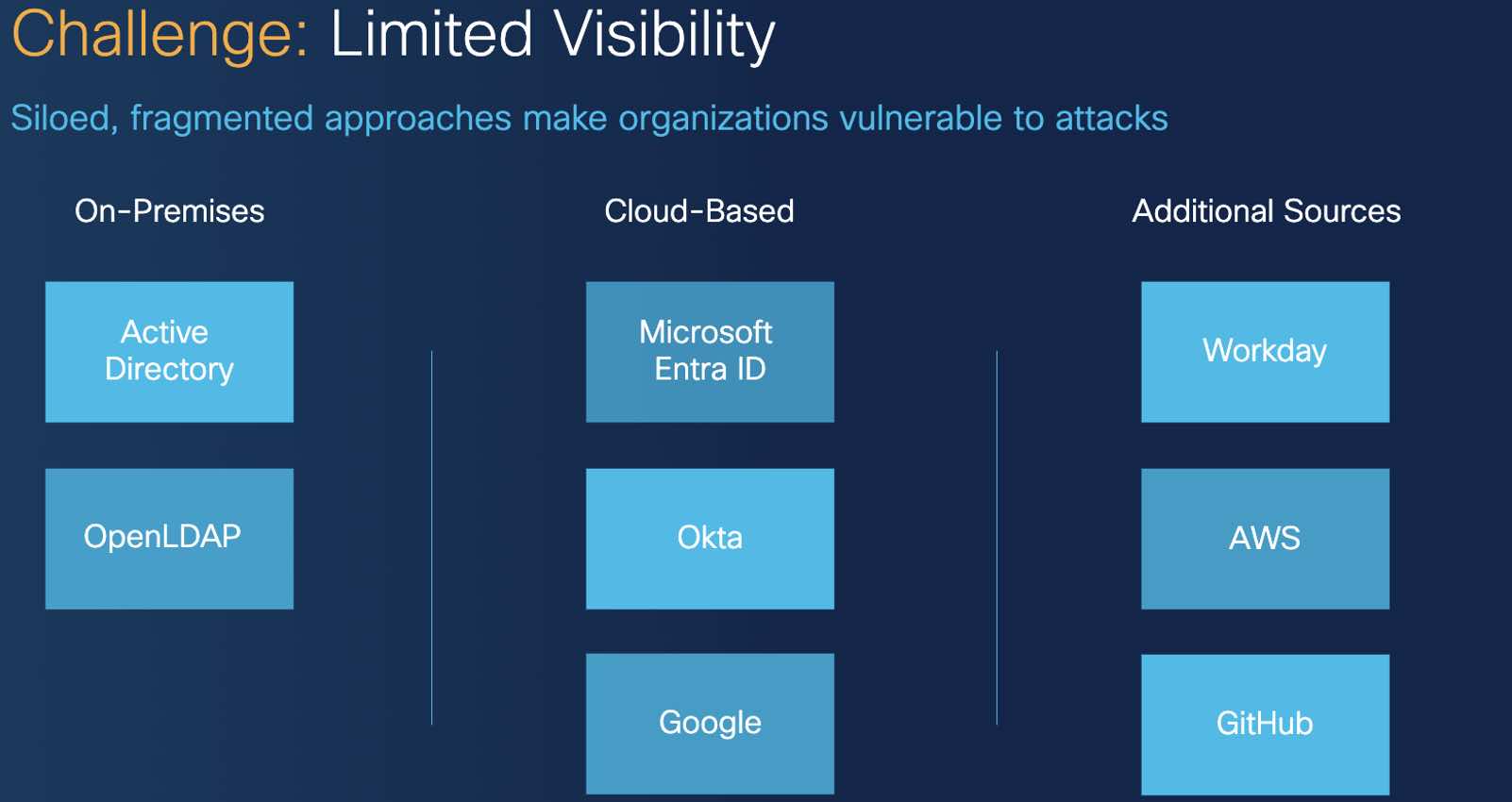
More likely than not, your organization has hundreds of applications across different departments and roles. The applications could be sensitive, privileged access, or not, and may be on-premises, SaaS-based cloud, self-hosted cloud or some combination. The identities (usually people, but sometimes service or machine identities) accessing the apps are likely working from anywhere, at any time, and maybe even from a work or personal device. They could be staff, but maybe there’s also temporary contractors or third parties who need controlled access.
The trouble with access policies
Access management policies control access to applications are complex and typically unique per organizational role. They must be individually assessed frequently to ensure consistent enforcement of the organization's security strategy (hopefully, a zero trust security strategy). Given the complexity of policy, even the most advanced teams struggle to deploy, maintain and assess a strong access management policy posture standard that helps mitigate threats while also supporting a productive business. In 2022, Gartner saw this as a large enough security issue to create a new security software category called Identity Threat Detection and Response (ITDR).
Later in 2022 CISA bolstered this claim and posted an urgent cybersecurity advisory stating that “Weak Security Controls and Practices Routinely Exploited for Initial Access”, which is CISA’s polite way of saying “your access management policy is weak and will get hacked”. Access policies are inherently complex as human behavior pushes new work boundaries and can be expensive to deploy, support and update securely while maintaining productivity across users and the IT and security teams supporting the infrastructure.
There are likely multiple departments across IT with ownership to compliance and security teams, and identity and other miscellaneous IT teams. In some scenarios, endless products cover parallel and competing use cases as well. This leaves organizations with a scenario where vulnerable access policies are deployed to avoid friction across various stakeholders, teams and leadership.
ITDR & ISPM introduced
Around the time of the CISA advisory, former startups like Oort (acquired by Cisco in 2023, now Cisco Identity Intelligence) and Spera Security (acquired by Okta in 2023) began to gain traction with thought leadership around identity security. Regardless, bad actors were already planning large-scale user identity-based attacks, such as the 2023 casino breaches, or the recent Snowflake breach, which prove social engineering’s getting easier, faster and cheaper with the advancement of artificial intelligence (AI) automated attack toolkits and services.
With the aggressive growth of identity-focused attacks, it's critical that organizations have a resource that ensures they have minimized their identity posture and threat risks so that bad actors cannot capitalize on hidden vulnerabilities across an organization's multi-vendor identity security posture — such as policy misconfiguration, poor security strategy, poor end-user posture/hygiene and more — and as a result, align with the requirements of compliance auditors as well. We’ll do our best to define the emerging categories of Identity Threat Detection and Response (ITDR) and Identity Security Posture Management (ISPM) in the following post below and what you should look for in a solution.
What is ITDR, or Identity Threat Detection & Response?

ITDR, or Identity Threat Detection and Response, is an emerging security software category coined by Gartner. ITDR helps organizations detect and mitigate identity risk by surfacing identity posture and security threats from across your environment. ITDR evaluates risk by analyzing existing identity providers, human resources information systems and other enterprise apps simultaneously while detecting risk with policies, permissions, user authentication logs, security events and additional third-party telemetry. Once gathered, ITDR solutions can correlate data from across all source tools and will typically surface the most critical vulnerabilities first or provide an ability to sort based on severity, compliance frameworks, security architecture guidelines, application source and more. This data is often capable of being sent to an external target, such as an XDR, SIEM, instant messaging applications, admin email distribution lists and more.
ITDR and ISPM solutions should also facilitate access management policies with a stronger, more reliable posture and threat signal for real-time risk assessment at the point of login or during an existing login session with correlation across identity providers, HRIS systems and enterprise apps.
What is ISPM, or Identity Security Posture Management?

ISPM, or Identity Security Posture Management, is a sub-category of ITDR focused on proactive identity posture assessment (not advanced security threat mitigation). This category is still emerging from ITDR, but some ISPM solutions have differentiated themselves by providing deeper posture mitigation than offered by standard ITDR solutions (such as user remediations).
Similar to ITDR solutions, ISPM solutions can correlate gathered data from across all source tools and will typically surface the most critical posture and hygiene risk first or provide an ability to sort based on severity, compliance frameworks, security architecture guidelines, application source and more. This data is often capable of being sent to an external target, such as an XDR, SIEM, instant messaging applications, admin email distribution lists and more. ITDR and ISPM providers should also facilitate access management policies with a stronger, more reliable posture and threat signal for real-time risk assessment at the point of login or during an existing login session with correlation across identity providers, HRIS systems and enterprise apps.
The Cisco Identity Intelligence team has a list of 50+ examples of posture risks and security threats for you to review which can help disambiguate between posture and threat risk.
Why is ITDR & ISPM important?
Identity and access management (IAM) policies are complex, unique per organization and are frequently poorly configured. ITDR (Identity Threat Detection and Response) and ISPM (Identity Security Posture Management) solutions are important because they provide visibility and control over your organization's identity posture (ISPM) issues and security threats (ITDR) in a single, comprehensive interface with correlation from across your identity stack — including identity providers (IdP), enterprise applications and human resource information systems (HRIS) — so your administrators can put in place stronger access management policies and strengthen access requirements. In the future, ITDR and ISPM will continue to be developed into a risk signal for identity and access management (IAM) policy for a stronger, proactive security response.
What should I look for in an ITDR & ISPM solution?
An ITDR, or Identity Threat Detection and Response solution, and ISPM, or Identity Security Posture Management should:
Connect and protect a multi-source list of connected target identity providers, human resources information systems (HRIS) and critical enterprise applications.
Control and visualize with a robust list of security and posture alerts that are based on a strong multi-source collection of security threat and posture hygiene signals and support advanced report filtering such as compliance frameworks, regulatory standards, and more.
Alert and remediate with live or retro event data to IAM solutions, ITSM solutions, SIEM solutions, email or chat/messaging notification solutions or mitigation remediation solutions.
Connect & Protect
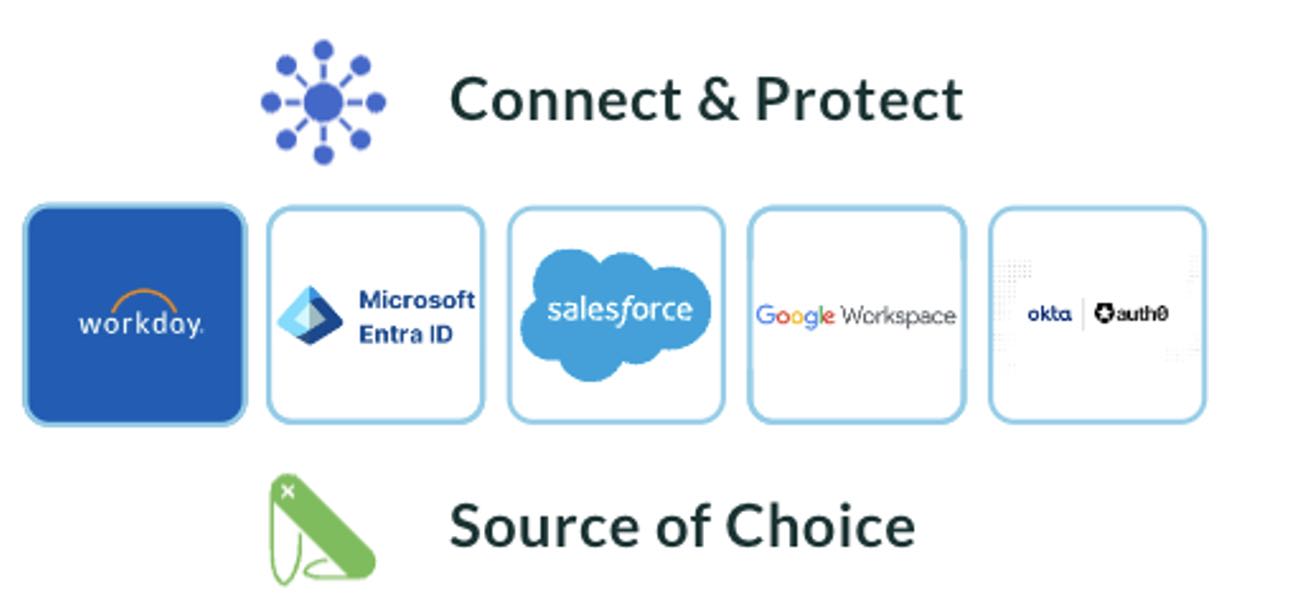
ITDR and ISPM should support the ability to connect and protect a multi-source list of connected target identity providers, human resources information systems (HRIS) and critical enterprise applications with the same level of integration and focus, or have roadmap plans to support in the future. This may include identity providers such as Microsoft, Okta, Google, Auth0, or Ping, HRIS systems such as WorkDay or SAP, and enterprise applications such as Salesforce.
Control & Visualize
ITDR and ISPM should allow the ability to control and visualize with a robust list of security and posture alerts based on a strong multi-source collection of security threat and posture hygiene signals. The collection of signals should come from reliable sources including the target identity providers, human resources, enterprise applications, access devices, access telemetry, threat feeds, security solution integrations and more to understand the full impact of each posture or risk alert.
An ITDR and ISPM should also support advanced report filtering such as:
Identity hygiene view/filter that identifies posture-based risk such as identity hygiene, no/weak MFA, dormant accounts, over-privileged users and more
Identity threats view/filter that identifies active identity-based threats to your organization based on signals provided from geo-location, device telemetry, external identity or security sources, anomaly detections, impossible travel and more
A compliance, regulatory and security framework monitoring view/filter that identifies alignment across CIS, CMMC, MITRE, NIST, PCI and SOX standards
· An Idle license insight view/filter that allows the ability to review identity licensing usage across connected target identities, human resources and enterprise applications
Alert & Remediate
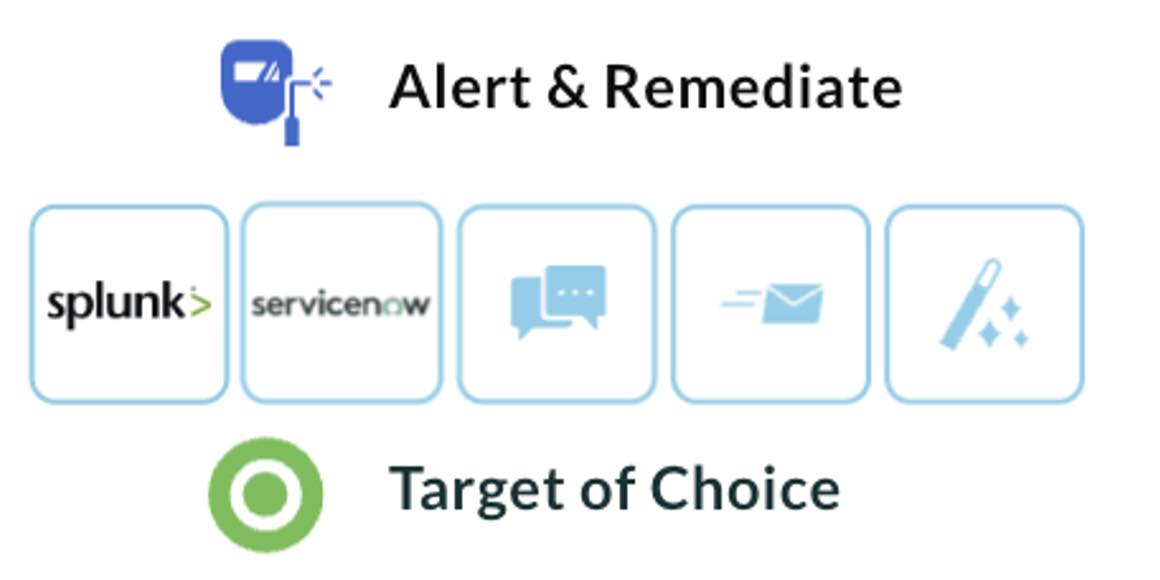
The ITDR and ISPM solution should make it simple to act with alert and remediation options natively, or to your external target of choice including Identity and Access Management solutions (such as Microsoft and Duo) to influence access policy, SIEM (such as Splunk) or XDR (such as Cisco XDR) to correlate with other threat events, ITSM (such as Service Now or Jira) to submit new requests or tickets, and urgent email notifications or instant messaging notifications to your platforms of choice such as Google, Microsoft 365, Cisco Webex, Slack and Microsoft Teams. The event stream should support the format of the preferred target solution and provide clear, actionable logs with correlated data points.
The ITDR & ISPM Solution Checklist
Based on Duo research, we put together a simple three-step ITDR and ISPM: Solution Checklist that may help your journey:
Can you connect and protect a multi-source list of your target identity providers, human resources information systems (HRIS) and critical enterprise applications?
Can you control and visualize a robust list of security and posture alerts based on a strong multi-source collection of security threat and posture hygiene signals? Can you support your advanced report filtering needs such as compliance frameworks, regulatory standards and more?
Can you alert and remediate with live or retro event data to your target IAM solutions, SIEM solutions, ITSM solutions, email or chat/messaging notification system or additional remediation solutions?
We hope this helps you on your identity security journey.
Does Cisco Duo have an ITDR or ISPM?
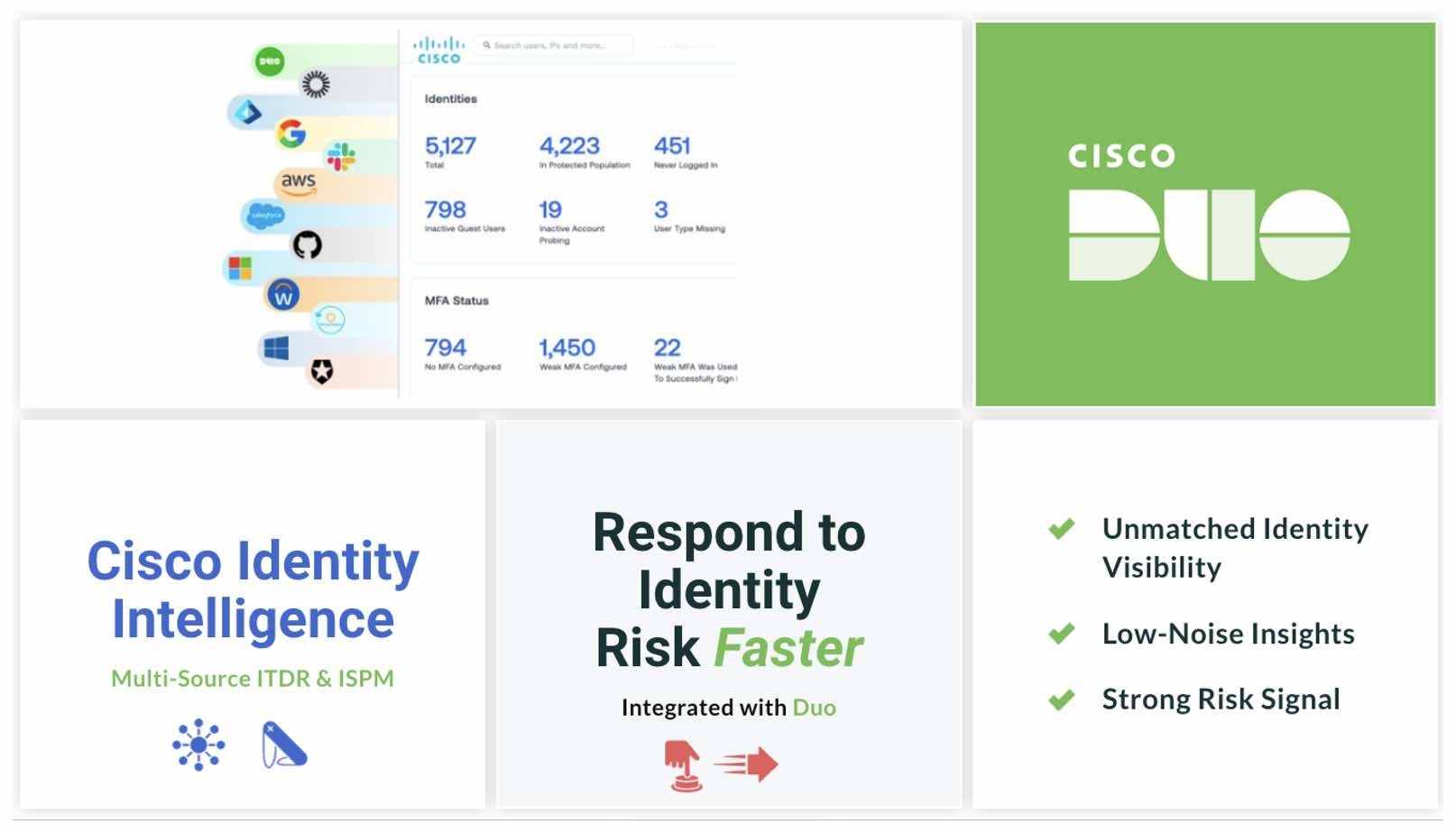
Yes, Cisco Identity Intelligence is Cisco's ITDR and ISPM solution. Cisco Identity Intelligence is available now to all Duo Advantage and Premier customers at no additional cost. Existing solutions in the market today are either too noisy with false positives, hyper-focused on legacy infrastructure or tailored for one specific identity solution. Current solutions lack the immediate, cross-platform enhanced visibility and value that customers seek. Cisco Identity Intelligence provides customers with unmatched visibility across their identity ecosystem in a single, comprehensive interface with low-noise insights based on a strong risk signal.
To learn more about creating a strong identity security strategy, be sure to watch our on-demand webinar Identity Under Siege: Strategies for Enhancing Security in a Zero Trust World.
Curious about your identity security hygiene? Schedule a Cisco Identity Security Assessment today!


