#Winning: Securing FinServ Hybrid Clouds with MFA
The No. 1 driver for financial services organizations to update and maintain cyber security is compliance.
Staying in compliance costs financial institutions $70 billion annually, a price tag fueled by the need for cyber security and data protection. With 65% more persistent threats than other industries, financial services organizations keep cyber security top of mind. International, federal, and many state and local governments are adopting compliance standards that require financial institutions to implement multi-factor authentication (MFA) security protection into their systems as quickly as possible.
Financial Firms Slow to Adopt Cloud
The FinServ vertical has been slow to adopt to cloud compared to other industries, relying on traditional data centers more so than other industries. The Wall Street Journal reports that although European banks plan to make over $77 billion in aggregate technology investments to compete with America’s $105 billion investment in a tech overhaul, most of Europe’s spend will go to patching old legacy systems, with less than a quarter being spent on new tech. Five years ago the U.S. was in the same boat, but now at least half the budget goes in to innovation and modernization of legacy systems.
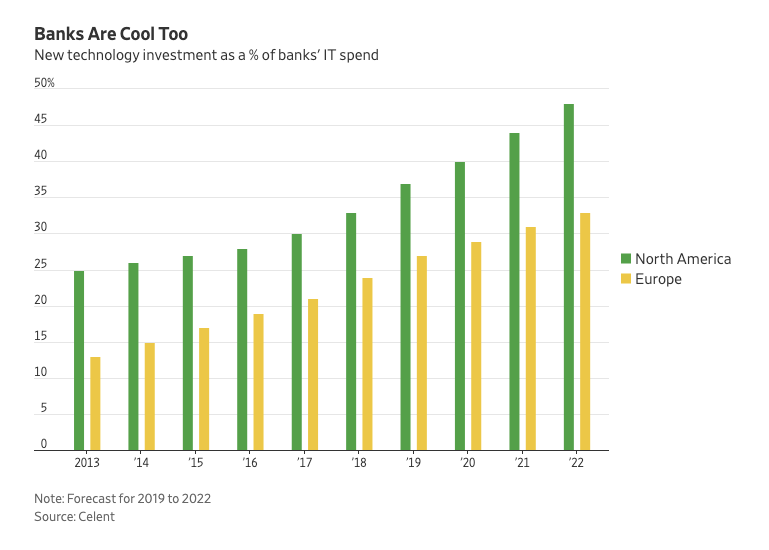
The sales cycle to upgrade or introduce a new infrastructure for financial services is at least five years and extremely expensive. Legacy systems work with necessary applications but are too costly to stop using while also too costly to maintain – it’s a true catch 22. The challenges for financial institutions to update systems includes securing massive amounts of data, finding skilled hybrid cloud talent to help modernize legacy systems, finding companies that integrate with all of their apps and staying competitive with modern solutions customized for their customers.
The Pros Outweigh the Cons for Cloud Adoption
There are six transformative cloud attributes for the financial services sector: cost flexibility, market adaptability, masked complexity, contextual variability and ecosystem connectivity. Cloud-first financial institutions have an advantage over their rivals. They can keep the customer experience personalized, develop and release more prolific tools and applications and incorporate new technologies, like artificial intelligence, to get smarter, while getting to market faster. There are many advantages for the financial services sector to move to a hybrid cloud.
Many FinServ companies skipped the first generation of public cloud services, but are opting into second generation with microservices and containers. The ability to access or delineate the massive amounts of stored data that is often inaccessible is one of the major advantages of the hybrid cloud. Companies can use the large public cloud resources for heavyweight tasks that use non-sensitive data. While keeping sensitive data stored in local environments, data analysis can be done with advanced application development in the cloud. The silos of information can become integrated. After maintaining compliance, security is a top concern of the industry.
Securing the Cloud Can Be Broken Into Three Key Areas
The Three Pillars to Cloud Security
Network & Infrastructure Security: This protects virtual infrastructure and network traffic, while hardening endpoints (API gateways) and protecting services.
Identity & Access Management: This protects various cloud requirements for authorization and authentication through multi-factor authentication, access and policy governance and accountability management.
Data Protection: This controls for data, at rest, in transition and in use with encryption, key and certificate management.
Getting to Perimeter-less Security Through Zero Trust
As identity IP can change moment to moment—such as when someone accesses WiFi in a hotel first with a laptop and then with a smartphone—access can pivot and change. The attack surface has changed and more companies are moving into an offensive position versus a defensive one.
The perimeter pushed toward “mobile first” and “bring your own device (BYOD)” and continues to expand to include cloud applications. This has changed the definition of what trusted users, trusted devices and safe traffic looks like. Organizations need to expand the perimeter across on-premises, cloud and hybrid environments.
One Solution for All Applications
According to Cisco’s top security trends, the first step is securing the perimeter and getting to perimeter-less. By incorporating a zero-trust approach with multi-factor authentication managing credential and application access regardless of location, companies can rapidly adopt perimeter-less security, without a rip and replace, making it extremely cost effective while expanding protection across surfaces.
Know What Is Happening on Your Network Right Now
With identity and access management technologies, organizations can define policies based on specific users and applications, limiting worker access to only the information they need to do their jobs. Some device visibility solutions only give you limited insight into certain platforms and operating systems. Duo uses a single centralized dashboard that gives admins oversight across the network, hardware and software.
Duo empowers you to limited access and flag risks before they become problems
Stay compliant. Duo provides end-to-end visibility, reporting and logs of assets. Duo's endpoint visibility gives a detailed overview of users' devices (managed or unmanaged, mobile and laptops/desktops) with compliance-friendly reporting and logs
Get granular control with continuous reporting and monitoring of systems. Streamline data reporting and policies. Duo continuously monitors and reports on the health of your infrastructure. Identify mobile devices with certain security features enabled or disabled, as well as their security posture. BYOD, no problem
Duo centralizes access policies across platforms with zero-trust security. Admins can consolidate dashboards and get a single view of overall security status. Duo's Admin Panel flags risky devices allowing policy controls that limit access based on device and user trust (adaptive authentication)
Support several authentication methods based on user choice: Duo Push, phone calls, U2F, etc. for all applications and services
Limit or restrict access based on location or IP ranges. Grant or deny access to applications based on where the user/device is coming from and what they are accessing with an easy to use interface
Stop unauthorized authentications. Block authentication attempts from anonymous networks like Tor and proxies
Duo is software agnostic, accessible and open to everyone — democratizing security. Duo supports all users, types of devices, and integrates with on-premises and cloud applications.
Customer story:
Want to learn more? Start a free trial today, and learn how Duo can help your organization.
.jpg)
Zero Trust: Going Beyond the Perimeter
A zero-trust approach shifts the secure perimeter to any place where you make an access control decision and prompts you to question your assumptions of trust every time there’s an access event.
In this guide, Zero Trust: Going Beyond the Perimeter, we examine the genesis of the zero-trust approach and introduce the three pillars of zero-trust security: Zero Trust for the Workforce, Zero Trust for the Workload, Zero Trust for the Workplace.
Get the free guide
