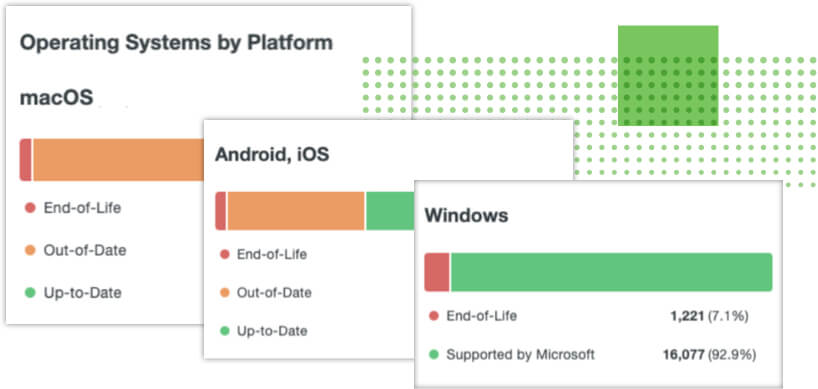
Close Security Gaps
When your users’ devices are out of date, they’re more susceptible to exploits that leverage known flaws in software — and when they log into your applications, that means your data is also at risk.
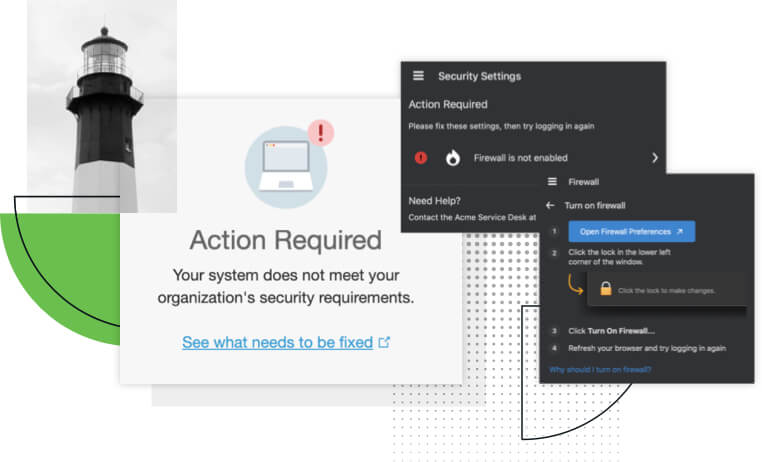
Help Keep Users' Devices Healthy and Secure
Duo’s Endpoint Remediation lets your admins block access to enterprise applications based on outdated software versions, while Self-Remediation warns your users that they're using outdated software and gives them the option to update their own devices.
Notify Users When it’s Time to Update
Warn users they’ll be denied access in a certain number of days unless they update. Or, use Duo’s Endpoint Remediation to automatically block device access to enterprise applications based on outdated software versions. Identifying and remediating risky devices helps prevent the spread of malware and a potential data breach.
.jpg)
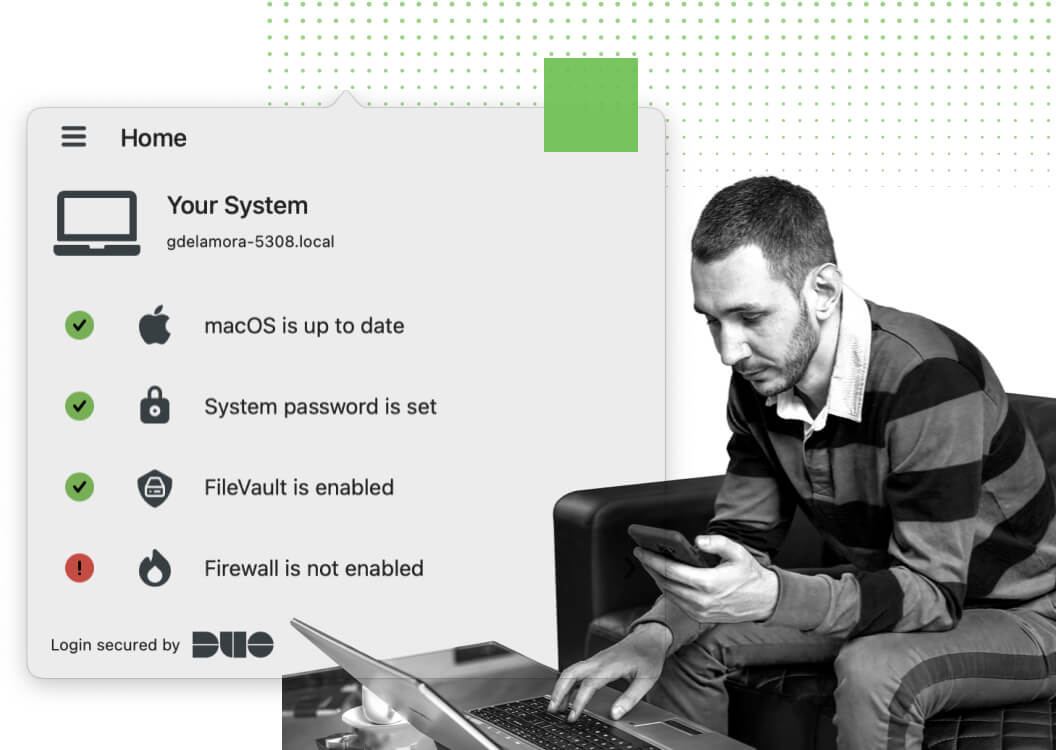
Maintain Healthy Devices
Duo checks every user device at every login to ensure compliance with your unique, situational security parameters. The Duo Mobile app’s Security Checkup feature and the Duo Desktop feature, available for laptops and desktops, pinpoint weak points in a device’s security, allowing users to address the problem quickly, without involving your help desk.
Actionable Insights at Your Fingertips
To give you actionable data, Duo’s Device Insight collects information about your users’ devices as they authenticate into your applications so you can see how many devices are out of date or jailbroken, rooted, encrypted and more.