Define Device Trust Your Way
Establishing user trust is essential, but it’s no longer enough. You also need to have trust in the devices accessing applications on your network. Duo Trusted Endpoints lets you define trust for every endpoint, whether managed or unmanaged, company-issued, contractor-owned, or personal.

Allow or Block. You’re in Control
Because unknown devices pose a security risk, some organizations allow their workforce to only use managed endpoints they’ve provided when accessing network applications and resources. With Duo Trusted Endpoints, you have control over which devices are granted access, and which are blocked based on the policy you create.
Embrace BYOD Securely
Unmanaged doesn’t have to mean untrusted. Duo enables you to extend your Bring Your Own Device (BYOD) security policy and manage access to Duo-protected applications from endpoints that are not enrolled in a device management solution by adding them to your inventory of trusted devices.
Extend Trust to Mobile Devices
Not everyone does their work on a desktop or laptop - increasingly, it’s from a mobile phone or tablet. The Duo Mobile app verifies trust for iOS and Android devices, enabling users to securely access Duo-protected apps like email wherever they are.
Build Your Trusted Device Inventory
Create and maintain an inventory of your organization’s trusted devices, their health, and their access activities. You can add and remove devices, include a description, set a trust expiration date, and more. Register company-issued managed endpoints and unmanaged contractor-owned, partner, and employee personal devices.

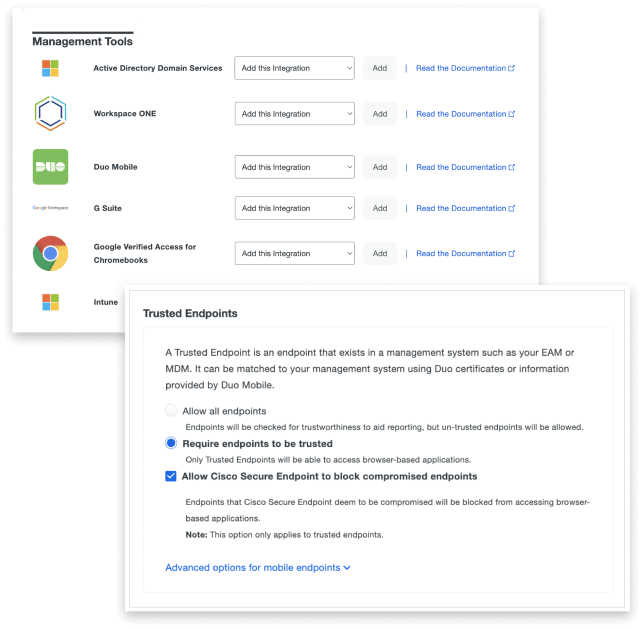
Leverage Your Existing Device Management Solution
For organizations that choose to allow access only from managed devices, Duo supports native integrations with a broad range of leading mobile device management (MDM) solutions. At authentication, the Trusted Endpoints policy checks to see if the endpoint is enrolled in a supported MDM or UEM, or registered with Duo. If it’s not, the device is considered untrusted and can be blocked from accessing browser-based applications.
Automatically Block Malware-infected Devices
Having limited IT resources shouldn’t make it difficult to respond effectively to endpoint security events, especially when those devices are outside the network. By integrating Cisco Secure Endpoint with Duo, organizations can set a policy to automatically block malware-infected devices from accessing applications. Duo blocks only the endpoint, so your users can log in from any other device that is policy-compliant to stay productive.
The level of detail Duo provided into what devices were connecting to our networks, managed or unmanaged, was helpful. We could see things we could never see before -- like the number of attempts on a credential on M365 or the number of lockouts that have happened." Read the customer story
— Craig Vincent, Director of IT Infrastructure and Operations, La-Z-Boy


