Identity Threat Detection and Response: What is ITDR?
Identity Threat Detection and Response (ITDR) is at the forefront of modern cybersecurity, addressing the critical challenge of protecting user identities from increasingly sophisticated cyber threats.
As identity becomes the core of digital access, particularly in remote and hybrid work environments, ITDR plays a vital role in identifying, mitigating, and preventing identity-related attacks. From phishing schemes to credential abuse, ITDR ensures that businesses maintain secure operations while protecting sensitive data.
How Identity Threat Detection and Response works: The ITDR basics
Identity threat detection and response includes tools, solutions, and processes. These are used to find, assess, and stop threats. These threats mainly target user identities and IAM (identity and access management) systems.
Unlike traditional cybersecurity methods that focus on securing endpoints and network perimeters, ITDR focuses on identity and access credentials. This shift is important in cloud-first and hybrid work environments.
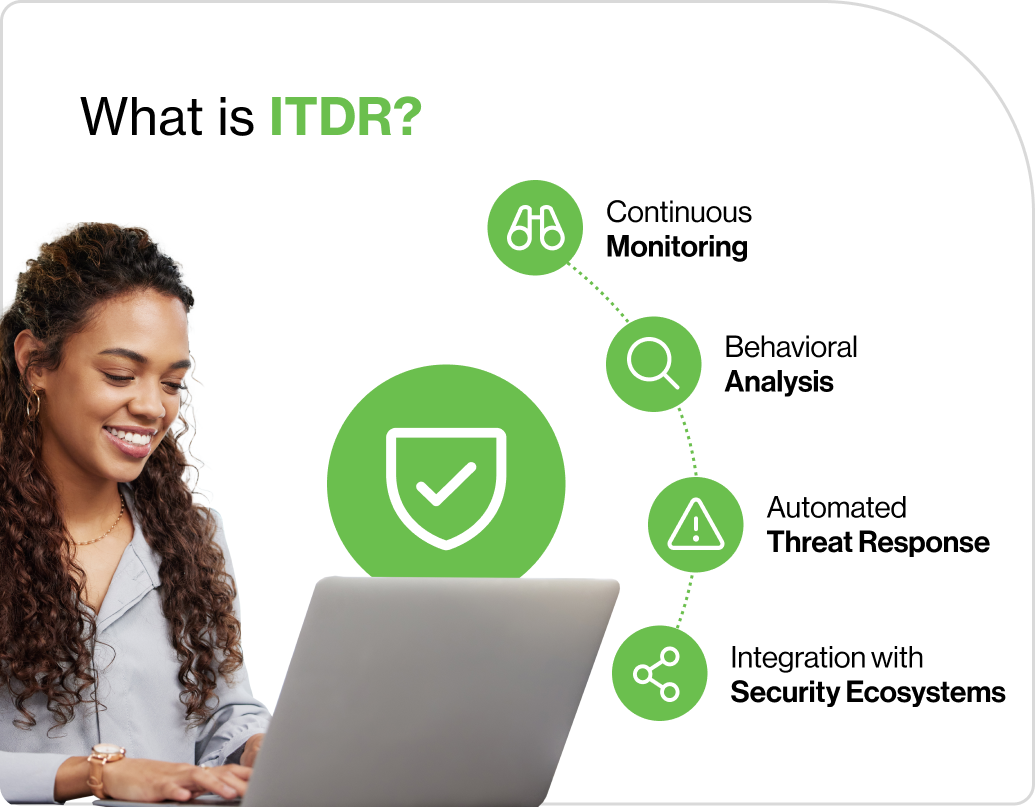
Core functions of ITDR include:
Continuous monitoring: ITDR solutions check identity and access management (IAM) systems in real-time.
ITDR can look for problems like:
Repeated failed login attempts on user accounts
Unexpected access from different locations
Unauthorized privilege increases and network traffic
Behavioral analysis: ITDR systems can spot unusual user behavior. This helps find compromised accounts or insider threats. By setting a baseline of normal activity, they can detect these changes.
Example: A sudden surge in file access at unusual hours might signal malicious activity.Automated threat response: ITDR tools can automate responses to threats. They can lock compromised accounts, notify administrators, and start incident response protocols. Automation reduces response times, minimizing potential damage.
Integration with security ecosystems: ITDR often works with threat intelligence feeds and tools like Security Information and Event Management (SIEM). It also connects with endpoint detection and Security Orchestration, Automation, and Response (SOAR) platforms.
By focusing on these key functions, ITDR helps organizations find identity-based weaknesses. This allows them to respond quickly before these issues turn into serious system problems or data breaches.
Why is ITDR important to businesses right now?
Cyberattacks on identity and access systems have increased in recent years1. Attackers are using more advanced methods to take advantage of weak points in identities and credentials.
In response, ITDR has become an important layer of defense. It fills gaps left by traditional cybersecurity measures. ITDR gives businesses key identity-based detection and response abilities in this changing threat environment.
The growing threat to identities
With the move to cloud-based apps and remote work, employees can now access important systems from many devices and places. This decentralized access increases the attack surface, making credentials and access privileges attractive targets for cybercriminals.
Methods like phishing, credential stuffing, and session hijacking take advantage of human and system weaknesses. They allow attackers to get unauthorized access to sensitive information.
The cost of failing to protect identities
A single compromised identity can serve as a gateway to any business’ most critical assets.
For example, attackers can use stolen credentials to escalate privileges, move laterally within networks, and exfiltrate data.
They also give employees confidence that their accounts and activities are safe. Data breaches can have a huge financial impact. Costs can include legal fines, damage to reputation, and lost revenue. Moreover, non-compliance with regulations like GDPR, CCPA, HIPAA, and PCI DSS can lead to significant penalties.
Want to dive deeper?
How to evaluate the true cost of MFA
Building trust through ITDR
Robust ITDR measures enhance customer and partner trust by demonstrating a commitment to protecting sensitive data. They also give employees confidence that their accounts and activities are safe. This helps create a culture of security awareness.
Identity theft resource center 2023 annual data breach report
Best practices to follow in ITDR
To implement effective ITDR, your business is going to have to rethink traditional security methods.
Here are some steps that can help you with a successful ITDR implementation:
Step #1: Conducting a comprehensive risk assessment
Identify identity-related weaknesses in your company’s current systems and workflows. Evaluate potential threats and prioritize areas requiring immediate attention.Step #2: Defining clear objectives and success and metrics
Establish requirements, scope, and specific goals for ITDR, such as reducing response times or detecting anomalous behavior. Develop key performance indicators (KPIs) to measure the effectiveness of your ITDR implementation.Step #3: Choose the appropriate ITDR tools
Select ITDR solutions that integrate well with existing identity and access management (IAM) and security infrastructure.Connect ITDR with SIEM, SOAR, endpoint protection, and other cybersecurity tools. This creates a unified security framework.
Use APIs and connectors to make data sharing between systems easier. Ensure the tools offer advanced features such as behavioral analytics, AI-driven threat detection, and automated responses.
Step #4: Adopt Multi-Factor Authentication (MFA) and Zero-Trust approaches
Enforce continuous verification of all users, devices, and access requests. Enhance identity verification by requiring users to provide multiple authentication factors.Step #5: Fine-tune detection parameters
Customize detection rules to align with your business’ unique risk profile and operational needs. Never stop monitoring and adjusting these parameters to reduce false positives and improve threat identification.Step #6: Leverage automated threat responses
Configure automated workflows for common scenarios, such as locking compromised accounts or escalating incidents to the security team. Test automated actions regularly to ensure they function as intended.Step #7: Take advantage of available threat intelligence
Use external threat intelligence feeds to stay updated on emerging identity-related attack methods. Incorporate this intelligence into the ITDR system to enhance detection capabilities.
Common challenges with ITDR adoption
The organizations that fare the best in ITDR adoption are those that address some common hurdles early in the process.
Some of these challenges include:
Integration complexity and lack of visibility: Many organizations struggle to connect ITDR solutions with their current IT and identity systems. This is especially true when they do not have the data to find identity-based threats. This includes things like authentication logs and network activity.
Choosing solutions that support old systems and focus on complete logging and monitoring can help ITDR tools. This ensures they get the data needed to protect the business.The balance of security and usability: Users may resist additional security measures if they feel cumbersome. Implementing adaptive authentication, which adjusts security requirements based on risk levels, can address this concern.
Alert fatigue: False positives can overwhelm security teams and reduce their effectiveness. Fine-tuning detection parameters and prioritizing high-risk alerts can alleviate this issue. Use of strong authentication methods like Multi-Factor Authentication (MFA) can get ahead of alerts and blocked access.
Lack of team skills and response plans: Even the best ITDR platforms require skilled analysts to investigate high-impact incidents and initiate appropriate response protocols. SOAR, which stands for security orchestration, automation, and response, can be very helpful. The services of an MSSP, or managed security services provider, can also assist.
The relentless pace of new threats: The cybersecurity landscape evolves rapidly, requiring ITDR systems to adapt non-stop. Regular updates and threat intelligence integration can help ensure solutions remain effective.
What’s next for ITDR?
As technology evolves, ITDR solutions will need to adapt to address emerging threats and opportunities. Several trends are shaping the future of identity threat detection and response.
AI and automation
AI's role in ITDR is expected to grow. It will help ITDR tools analyze large datasets. These tools can identify anomalies and predict attacks more accurately.
Automation will play a bigger role. It will help ITDR systems respond to incidents faster. This will require less human help.
Decentralized identity systems
Decentralized identity models, where users own and control their credentials, are gaining traction. ITDR solutions will need to incorporate these systems, focusing on securing decentralized identities and ensuring their integrity.
Focus on cloud security
As businesses use more cloud applications, ITDR tools must offer real-time visibility and protection in multi-cloud environments. Solutions tailored to cloud-native applications and infrastructure will become essential.
Identity threat intelligence sharing
Collaboration among organizations to share identity-centric threat intelligence is likely to increase. Governments and industry groups are expected to create stricter rules. These laws focus on data privacy and identity security.
Stricter regulatory requirements
Governments and industry groups are expected to create stricter rules. These rules will support laws like GDPR, CCPA, HIPAA, and PCI DSS. ITDR systems will need to align with these requirements, offering features that ensure compliance while protecting against penalties.
Conclusion: Leveraging the value of ITDR
Identity Threat Detection and Response has become a cornerstone of modern cybersecurity, addressing the critical weaknesses associated with user identities and access credentials. By focusing on continuous monitoring, behavioral analysis, and automated response, ITDR protects organizations from identity-based attacks that traditional security measures may overlook.
In a world where identity is the new security perimeter, ITDR ensures businesses can operate securely, maintain regulatory compliance, and protect sensitive information. Adopting best practices, addressing implementation challenges, and preparing for future trends are key to maximizing the benefits of ITDR.
As threats change and work environments shift, ITDR will stay a key part of any strong cybersecurity plan. Organizations that prioritize identity security today will be better equipped to navigate the challenges of tomorrow, safeguarding their people, data, and reputation.
