Duo’s Data-Driven Defense: Combatting Cyber Threats in Higher Education
Duo has a long history of protecting students across universities and higher education institutions. From personally identifiable information to federal grants and loans, students and schools are a regular target for attackers. Because Duo has such a large presence in the world of education, we can also spot trends in attack tactics and learn how to better secure your organization.
One threat pattern Duo has seen targeting higher education within the last year includes a mixture of MFA-targeted attacks including passcode phishing and MFA fatigue. If successful, the bad actor register malicious devices on the student’s account for continued access to the student’s account and the university’s VPN. Duo Data Scientist, Becca Lynch, wrote about these attacks in the blog, Identity Threat Trends for Higher Education.
Duo has continued monitoring and responding to these attacks, while working with many of the higher education targets to secure their environments. But Duo hasn’t stopped there, as we have a unique ability to respond and establish scalable, structured product enhancements to our threat detection and response capabilities.
How Duo can help
When users set up Duo mobile, Duo takes a device fingerprint of that phone that is stored securely in our database. A typical device might be linked to a small number of Duo accounts. For example, a user might use their personal cell phone to protect their school account and when they graduate, they use it at their new job to protect their corporate account.
However, it is extremely rare for one device to be paired with hundreds of accounts, and that’s what the attackers are doing. They’re pairing the same device to all user accounts they’ve breached. One device being used to authenticate the account of 27 students across 5 schools? That’s phishy.
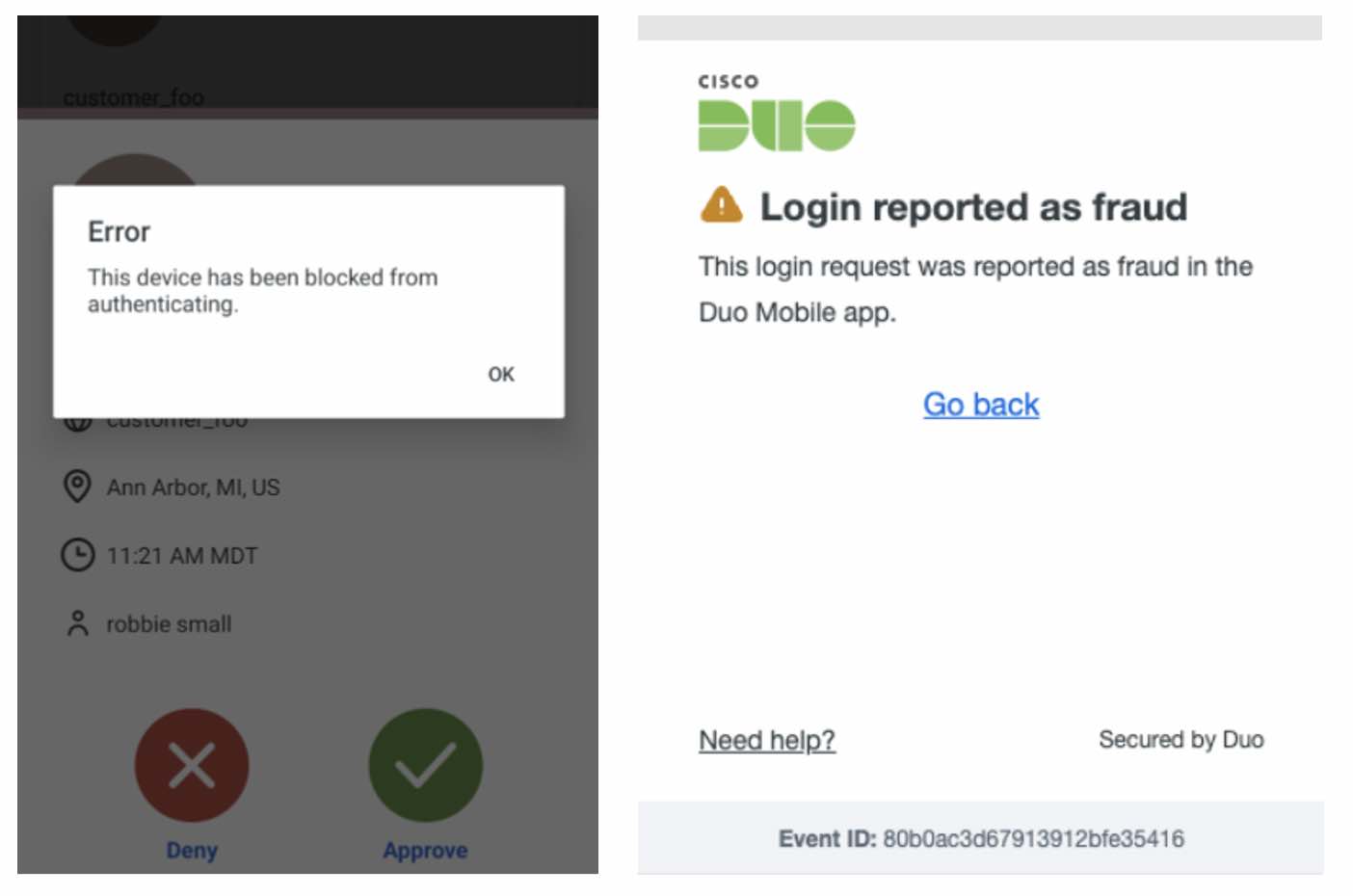
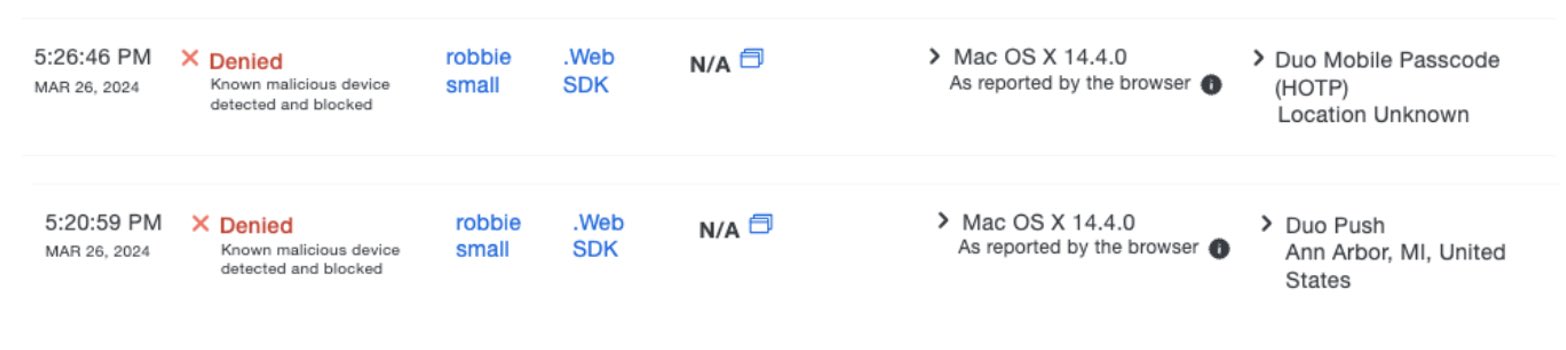
With Duo’s new feature, we can now block those malicious devices from continuing to access Duo-protected applications and the Duo admin panel. In the Duo admin panel, the logs now present when a device is blocked and why. This can also trigger an email to any configured administrator to provide immediate and up-to-date alerts on what is going on in their environment.
Duo can help protect every organization, not just universities, from these threats through improved threat detection and response capabilities. But the importance of secure policies should not be ignored.
We encourage all Duo customers, especially schools and other educational institutions, to ensure that they set up their policies to better protect their users, students and faculty alike. That means using secure authentication factors, implementing risk-based authentication to respond to change in user context, and pairing authentication with device trust policies through Duo’s Trusted Endpoints. It also means using an observability tool, like Duo Trust Monitor, to provide a view of all user events, including registrations and authentications, across your environment.
If you are not a current Duo customer but are interested in learning more, sign-up for a free trial today.

