Extend Your BYOD Security Policy and Start Trusting Unmanaged Devices with Duo Device Trust
Determining the trustworthiness of company-owned devices is usually straightforward: We install a mobile device management (MDM) tool, then implement security policies that allow IT and SecOps teams to protect the device or remotely wipe the endpoint if it’s been compromised. But for organizations with a bring-your-own-device (BYOD) policy, improving security by establishing device trust is more challenging. What if it belongs to a contractor or seasonal worker we’ve hired? Or a partner we’re collaborating with on a project? On top of that, how do we handle our own employees’ personal devices?
In each case, the device needing access is not corporate owned and managed so we may not be allowed to, or the owner may not want us to, install the company’s management software on their device. While the contractor/employee needs access to apps and data on the network, we want that device to be in a healthy and trusted state before it’s granted access to our network. How do we balance providing unmanaged BYOD access with ensuring these endpoints are in a secure, healthy and trusted state?
Health as a component of device trust
For years it was assumed that once the user’s identity was verified, they were considered to be on the “inside.” Anyone on the inside was trusted and had access to everything the network had to offer. Little attention was given to the access device and its health status, however.
Eventually, cybercriminals figured out that if they could install malware on an endpoint there was a chance the infected device would pass undetected once the user’s identity was validated. It was like the early days of airport security where the passenger simply had to show a ticket and ID to pass through security. Once their identity was confirmed, it was assumed any luggage they had wasn’t carrying something illegal.
This “castle-and-moat” model led to some high-profile data breaches that cost the affected companies millions in financial and reputational damage. We now understand that trust in the user is no longer enough. Regardless of whether you’re securing unmanaged BYOD endpoints or company-issued managed devices, it’s essential to account for trust in the device used to access network applications. And a key component of that trust is the health of the device.
Duo device health as trusted
So what makes a device “healthy?” In an earlier blog I outlined a series of recommended checks to consider when creating your access security policy. For Duo customers, information on the status of these checks is collected at the time of authentication by the Duo Device Health application (DHA) running on the endpoint.
In addition to verifying the device’s health posture, the DHA also gathers data on the device’s management status. Is it enrolled in a supported enterprise management system like Jamf, Intune or Cisco Meraki? If it is, then we know it’s one of ours.
How does device trust help with BYOD security and trust?
Let’s go back for a minute to our contractors, seasonal workers, partners and employees with devices not under our management. While they may balk at installing management software, the Device Health app is a lightweight client app that is much less intrusive and controlling. Users can install the app quickly and easily without needing assistance from IT.
Once installed, the Device Health app collects unique device identifiers during authentication and compares them against a list of known devices stored by Duo. If those device identifiers are recognized, it means we trust that device. It’s part of the Duo Trusted Endpoints feature, which secures your sensitive applications by ensuring that only registered or managed devices can access Duo-protected services.
But here’s where it gets interesting for those non-managed devices. Organizations can use the DHA to extend trust to them as well.
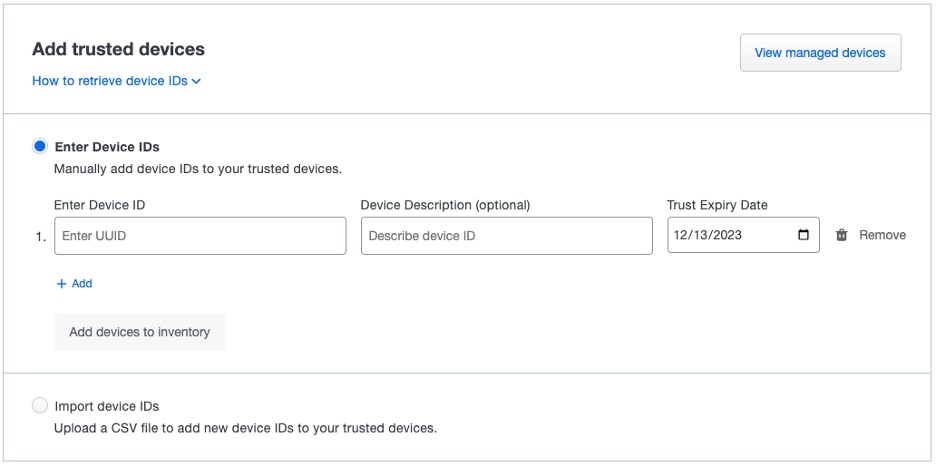
In her blog, Shilpa Viswambharan discusses how a manual integration feature based on the Device Health app enables IT administrators to manage macOS, Windows and Linux endpoints that are not enrolled in a management system by adding them to their list of trusted devices. This includes contractor-owned, partner and employee personal devices. Once an unmanaged device is added to the list, it’s considered trusted just like devices enrolled in an MDM.
The feature offers other benefits that enable you to trust these devices beyond checking their health posture. For example, administrators can set a trust expiration date, perfect for short-term and seasonal hires. They can add devices individually or in groups using a CSV file. Information can be edited, descriptions can be added and devices can be removed altogether through the Duo Admin panel. Ultimately, administrators can use the Device Health app as a solution to accommodate BYOD in security policies instead of overruling or ignoring users’ aversion to conventional endpoint management software.
Is it time to trust unmanaged devices?
Device trust is a tricky concept. We know our full-time employees, contractors and partners need access to network resources using their devices. We’ve also seen firsthand the importance of establishing the health posture of any device before access is granted. But is it necessary for the device to have an MDM installed to be considered trusted?
Not too long ago we would have said yes. But now with Duo’s Manual Integration feature for Trusted Endpoints there’s an alternative. You can proclaim any unmanaged device to be trusted by adding it to your organization’s customized list of trusted devices. It’s all up to you.
To learn more about how Duo can help your organization establish trust in unmanaged devices, read “The Essential Guide to Device Trust in the Enterprise.”

