Understanding & Defending Against Adversary-in-the-Middle (AiTM) Attacks
Adversary-in-the-Middle (AiTM) is a sophisticated attack vector that has made headlines for sensitive breaches. While understanding these types of attacks can seem intimidating, it is important to know what an AiTM attack is and how it works to safeguard your users and your organization.
What is an AiTM attack?
A typical AiTM attack might start out with a phishing email that includes a malicious link. All the attacker needs to do is get the user to click the link. The user might not even need to give up their password. Clicking the link routes the user to a proxy server which is typically identical to the authentic web page, except the URL. Oftentimes, these proxy sites will use HTTPS, so they will still show the lock icon in most browsers. The proxy page allows the attacker to steal the user's valid session cookies, bypassing the traditional authentication process.
How does the proxy work?
To learn how an AiTM attack works, it is important to first understand the following browsing concepts:
Cookies: Cookies enable a website to remember you, so you don’t have to re-login with every click. This is how you can navigate between emails without having to log back in or add different items to your shopping cart and the website remembers them.
HTTPS: HTTPS, or Hypertext Transfer Protocol Secure, is a secure version of HTTP. The protocol enables you and the website to speak securely using encryption, making it difficult for outsiders to monitor your communications or traffic.
AiTM can start by using the phishing link to initiate an HTTPS connection with the attack server and an HTTPS connection to the website you’re trying to access. HTTPS is never broken. There really is a secure connection between you and the attacker's server. From this point on, all traffic sent between the user and the login webpage – including credentials, MFA passcodes, and cookies – will be proxied through the attack server. This is key, because the attacker controls the HTTPS session, they can see everything that is sent.
Even an out-of-band method of authentication (a request sent through a different channel other than the website), such as a Push, is technically susceptible to an AiTM attack. This is because once a user completes the push request, the website sends the session cookie to the attack server. Once the attack server has the cookies to be authenticated with the website, it will sever connection with the user.
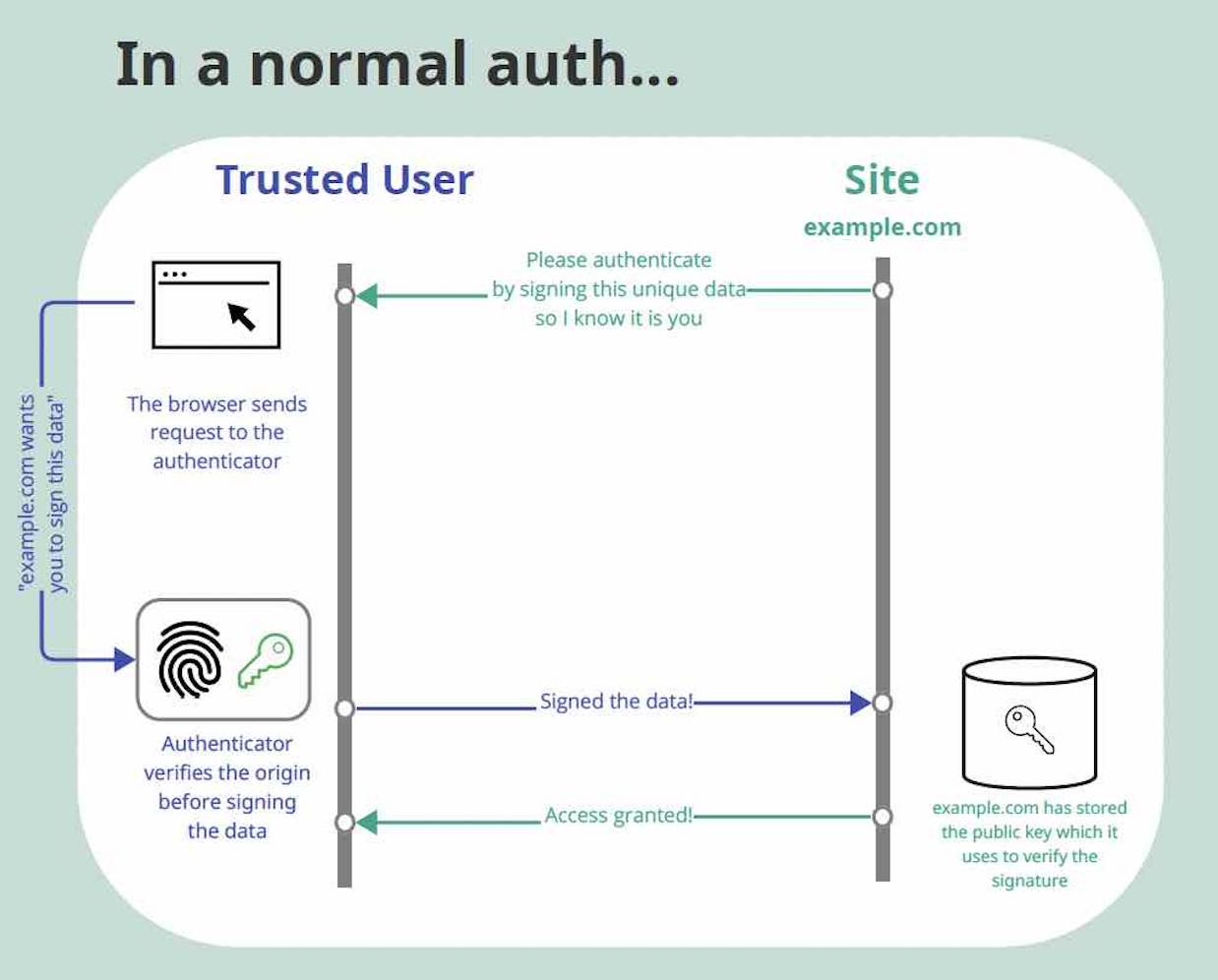
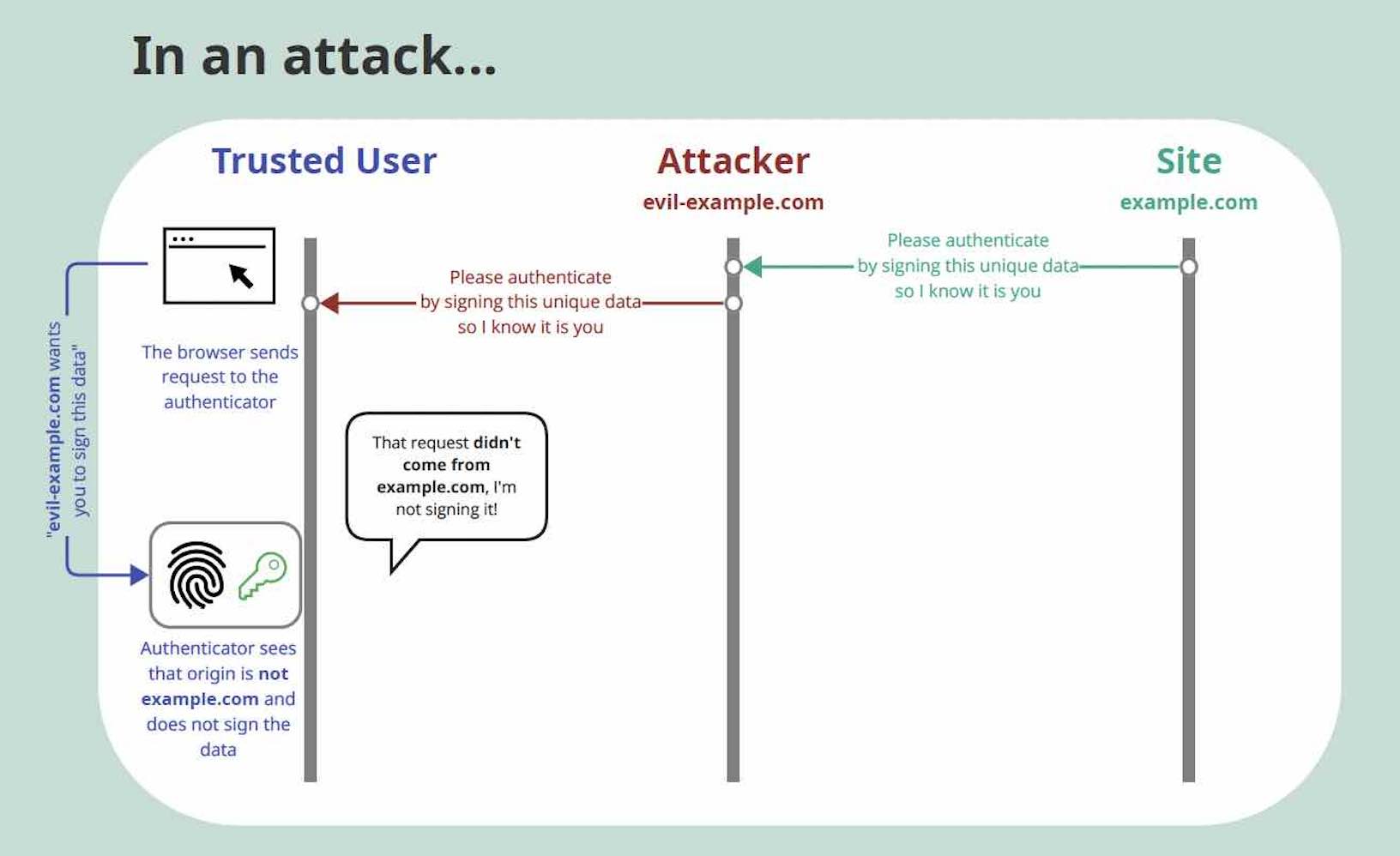
Phishing-Resistant Authentication
The best way to protect users from AiTM attacks is to require phishing-resistant authentication. The FIDO Alliance has developed standards based on public key cryptography, including the Web Authentication API, or WebAuthn. WebAuthn works using several different secure design principles, including:
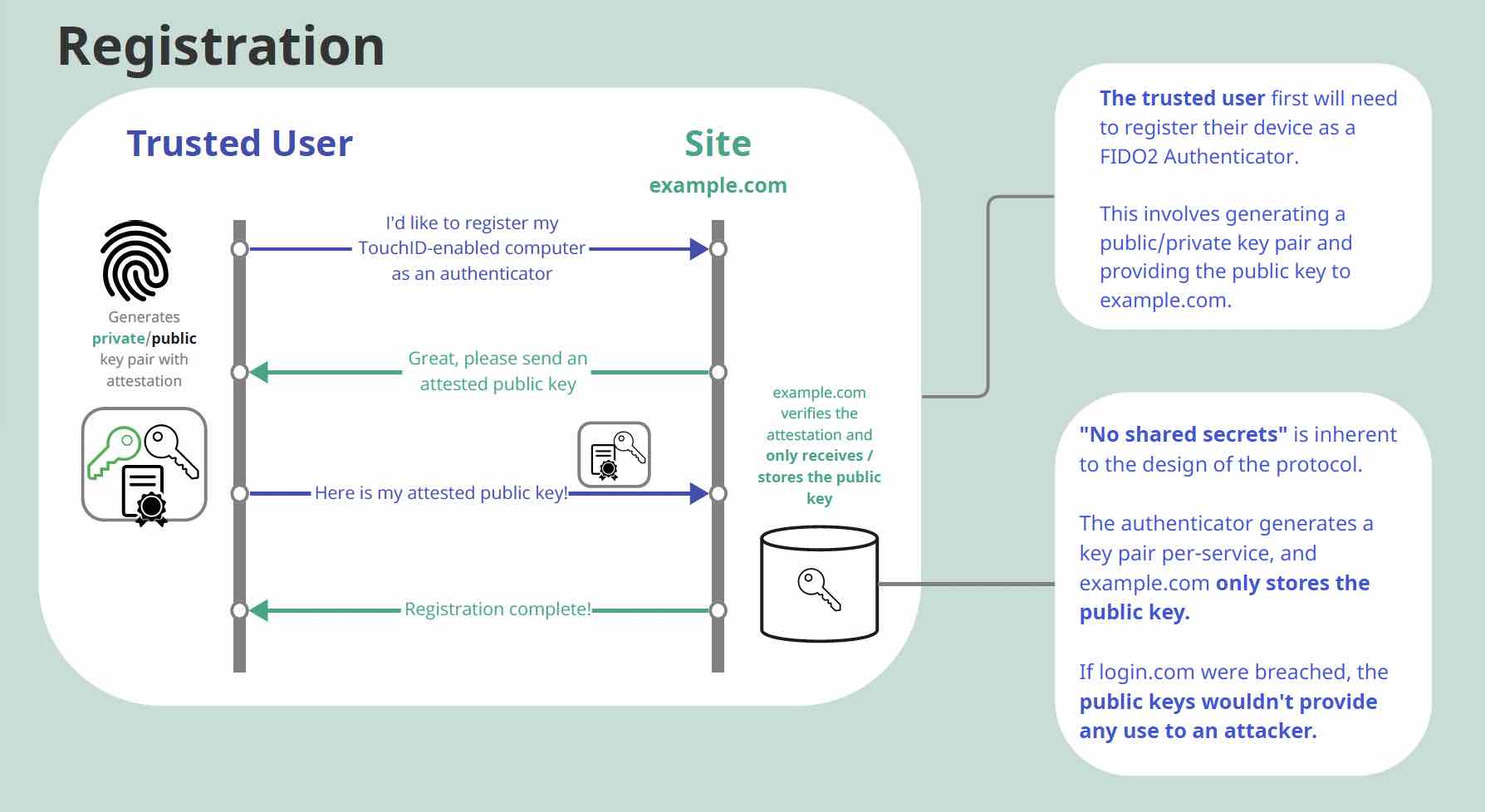
No Shared Secrets:
In this method of authentication, a user’s device creates a pair of keys. The private key is stored securely in tamper-resistant hardware on a device and a public key is registered with the application. When the user authenticates with the private key, it remains on the device so even if an AiTM attacker tries to intercept the communication, it is impossible to steal the private key.
Origin Checking:
When performing the authentication, the browser sends the origin information to the FIDO2 authenticator (like a security key or phone). The authenticator uses this information to ensure that the request is coming from the correct website, not a malicious one. This way, users don't have to worry about spotting small differences in the URL (like the difference between an upper-case 'O' and the number '0' in a URL); their authenticator does it for them.
Token Binding:
FIDO2 authentication also supports a method called token binding. When a user logs into a site or app, it gives the device a "token" which works like a temporary pass that proves the device's identity for a certain period. So even if an AiTM attacker intercepts the communication, they can't use it because it's bound to the original, secure session.
How Duo can help
Duo’s Passwordless solution employs FIDO2 standards to provide a phishing-resistant authentication option. This enables users to use a biometric, like a fingerprint or face ID, or a security key, to confirm their identity on their device. Doing so removes the need for passwords and enables users to complete multi-factor authentication in unified experience. In addition, Duo supports the use of passkeys, or WebAuthn credentials, to enable users to synchronize private keys between devices.
Organizations can also combine device trust policies with strong authentication to provide an extra layer of defense. Duo Desktop powers the Trusted Endpoints solution to evaluate the device’s health and management status when the user authenticates. With new features like Automatic Registration, Payload Signing, and Device ID Pinning, Trusted Endpoints can enhance protection against bad actors.
Duo makes it easy for organizations to protect their users regardless of the application or device. To learn more, sign up for a free trial of Duo to see the product in action today.

