Spot the Difference Between Legitimate & Suspicious Logins with Duo Trust Monitor
If you’re a cybersecurity analyst, suspicious logins aren’t anything new. You see them all the time. Identifying suspicious logins probably feels something like playing Spot the Difference. For the uninitiated, Spot the Difference is a puzzle game that presents you with two similar images, one of which has been altered slightly, and challenges you to pick out the differences between the two. Finding the differences can be a real test of one’s patience and ability to concentrate on details.
This can be fun if you’re taking a brain break. It’s less fun if there’s a real security threat you need to find. Why? Because searching through mountains of log data to find something different that could be a potential threat to your organization can be tedious and time-consuming. To illustrate the point, we’ll focus on a particular type of event that generates logs: user authentications (aka “logins”). Every time one of your employees logs into the network or an application, an auth log is created. Depending on the size of your organization this could result in thousands of new logs each day. There goes your break time.
If you prefer to spend your time on other pursuits, Duo Trust Monitor can help. Trust Monitor gives you back your break time by surfacing suspicious logins. And, we’re continuing to add new features like "Email Alerting" which proactively sends an email whenever a new security event surfaces.
Read on to learn more about this new feature, and about how Duo Trust Monitor can help you identify suspicious logins.
Identifying “different” authentications
Searching through auth logs to identify a login that looks suspicious is one thing. But how do you know if it’s truly different and poses a threat? To understand that, you need visibility into both normal and anomalous authentications. If you don’t know what a normal, or “expected,” login looks like, it’s hard to spot the difference between them. This requires creating a baseline authentication profile against which other logins are compared. Doing so will help you spot the difference(s) between the two and identify suspicious auths that could spell trouble.
But what happens if you don’t have the time to search through log data for atypical access attempts? Well, bad things possibly. One is account takeover using compromised credentials where the cybercriminal has stolen someone’s username and password. Based on responses in the IBM Security Cost of a Data Breach Report 2022, stolen or compromised credentials are the most common vector for a data breach, responsible for 19% of breaches with an average cost of US $4.5M. Once the account has been compromised, the attacker can use persistence techniques to maintain their presence without alerting the victim by interrupting their access. One technique used is to register a new authentication device in order to bypass multi-factor authentication (MFA). this fraudulent device registration typically goes undetected, leaving the threat actor free to gain access to critical applications and data on the network.
Another is insider access abuse, or privilege misuse. Findings from the Verizon 2022 Data Breach Investigations Report indicate the attacker is typically an employee who uses their legitimate credentials to access a privileged account to steal data, often for financial gain. While this doesn’t paint a pretty picture, the signs for identifying anomalous logins that could lead to a data breach are there. You just need the right tool to surface them.
See the signs with Duo Trust Monitor
So, what are the signs to look for? Here are a few along with some questions to consider:
The User – Is the person a current employee? Are they part of a group with privileged access?
The Auth Location – Do we have employees working in this country?
The Auth Time – Do we expect people to be accessing data or applications at 3:00am?
The Device – Is the authentication from a Windows device but our employees use Macs?
The Application – Does the user need access to this app to do their job?
Duo provides a tool to help you see the signs and “spot the difference” between authentication attempts. Duo Trust Monitor is an advanced anomaly detection feature that does all the work of searching for risky authentications for you. It ingests all the authentication logs in your environment and runs them through proprietary machine learning algorithms.
The algorithms set a baseline of normal user and device activity. Using this baseline, Trust Monitor compares future authentication attempts against it and highlights anomalous or risky login attempts in the form of a security event. With just a few clicks, administrators can create a Risk Profile for the organization that prioritizes and surfaces security events that match profile elements. For example, you may want to keep a closer eye on authentications related to certain Duo-protected apps, specific user groups or countries. Security events that deviate from the Risk Profile are given more weight and appear at the top of the Security Events board with a yellow shield designation that provides an explanation of the connection between the event and the Risk Profile.
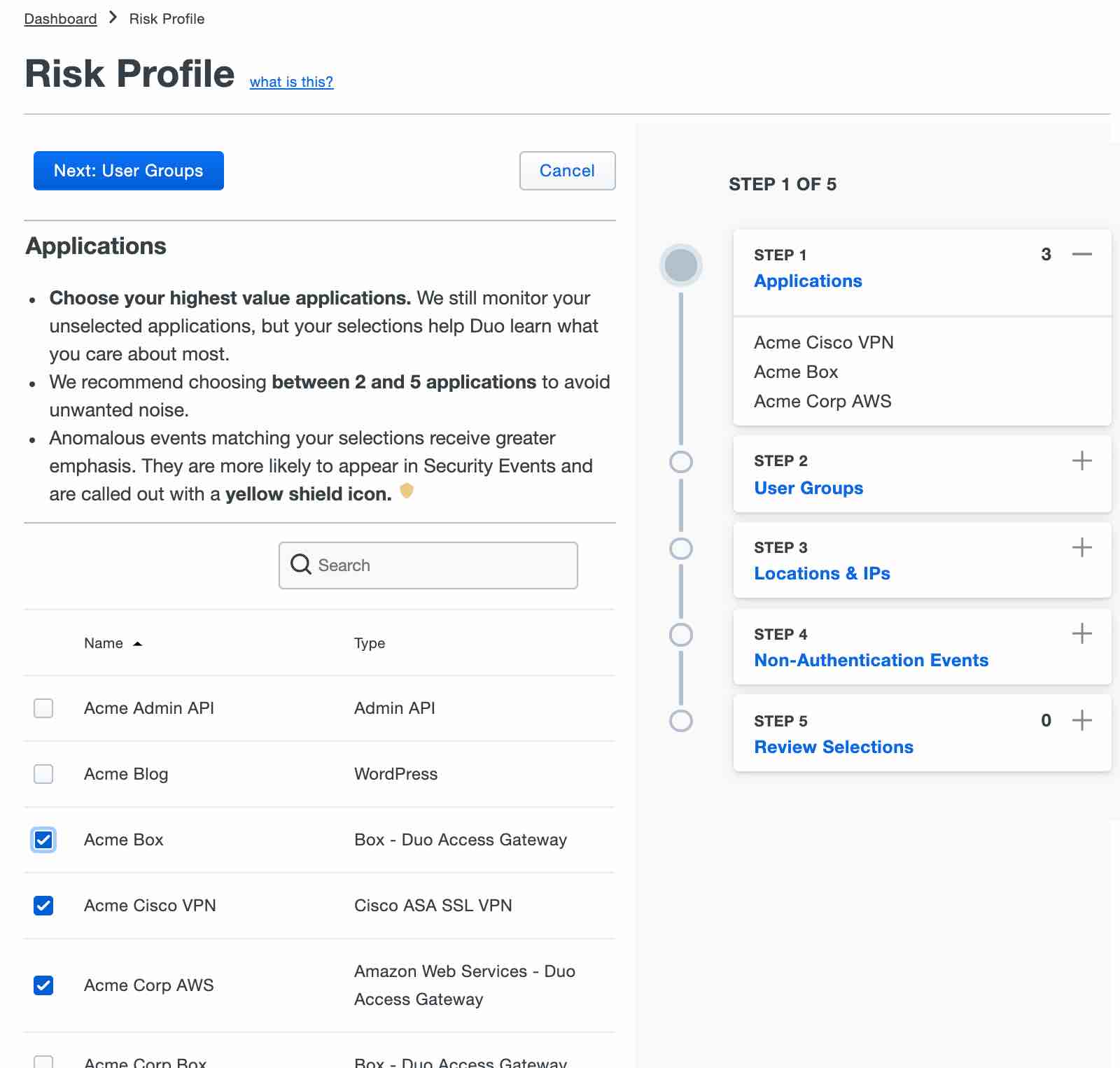
Can I get some context here please?
I’ve touched a bit on the “What” and “How” of Trust Monitor and its ability to surface atypical logins, but let’s take a closer look at the “Why.” Why is a particular authentication considered anomalous? The answer has to do with context. While there are other risk analytics tools on the market, many focus on a single model like novelty which looks for a variable that’s new such as a new device or application that’s being accessed for the first time. This approach is simplistic and doesn’t offer much context into the access attempt. Basing a decision on just one model alone can lead to an increase in false positives.
Trust Monitor on the other hand takes a more holistic view of each authentication using contextual analysis. By analyzing historical login data across multiple models and variables, Trust Monitor provides a much richer picture of the access attempt, enabling administrators to make a more informed decision as to whether it is legitimate or suspicious and requires action. Let’s look at some examples:
Security Event: The VP of Sales is accessing the company’s CRM app at 4:00 a.m.
Analysis: In this case Trust Monitor analyzes the application being accessed and the timestamp. Is it unusual for the VP of Sales to access customer information? No. Is the timing unexpected? Hopefully. A solution focused on Rarity would flag this event as risky.
Security Event: Someone is requesting access to a sensitive app from a Windows device using an unusual multifactor authentication method (SMS).
Analysis: Here we have three variables flagged. The organization uses macOS devices, not Windows. Also, the user has not accessed the app for six months and a push notification is their preferred authentication method, not an SMS text. These three together are a strong indication that this is a fraudulent authentication attempt.
Security Event: A Marketing manager is traveling to an event in another country and needs to access email.
Analysis: Without the right context, this access attempt could be marked as suspicious based on location, timestamp and a new device IP. However, we know there is a big event happening overseas so it’s not unusual to see these three variables associated with this user and therefore we can dismiss the event.
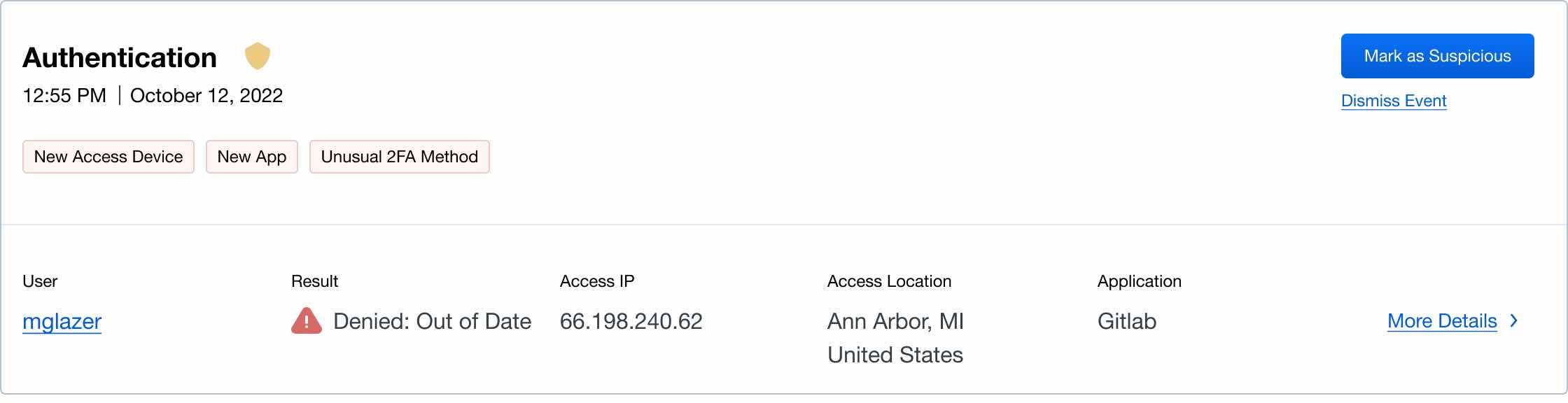
The goal of any risk analytics tool is to surface potential threats so that organizations can step up or step down their security policies to shore up any gaps. By providing contextual analysis, Duo Trust Monitor helps you spot the difference between legitimate and fraudulent access attempts while limiting false positives. Trust Monitor is included in our Advantage and Premier edition subscriptions. It’s also integrated into the Cisco SecureX ecosystem so that you can access Trust Monitor telemetry data from the SecureX dashboard for enhanced threat intelligence. And, if you already have a SIEM (Security Information and Event Management) solution, you can export Trust Monitor security event data directly to your favorite SIEM via API.
What's new with Duo Trust Monitor?
Security events are very useful for highlighting suspicious logins that may pose a threat. Adding context around why an access attempt was denied (or allowed) makes Trust Monitor even more powerful.
But even powerful tools need to adapt as the cyberthreat landscape changes, which is why we continue to build new capabilities into Trust Monitor. One of those is "Email Notifications," which sends email notifications when new security events populate in your environment. The notifications help you maintain an awareness of your organization's security posture using popular communications channels like email without having to log into the Duo Admin Panel. They include much of the same information you would see for the security event in the Security Events dashboard within the Duo Admin Panel.
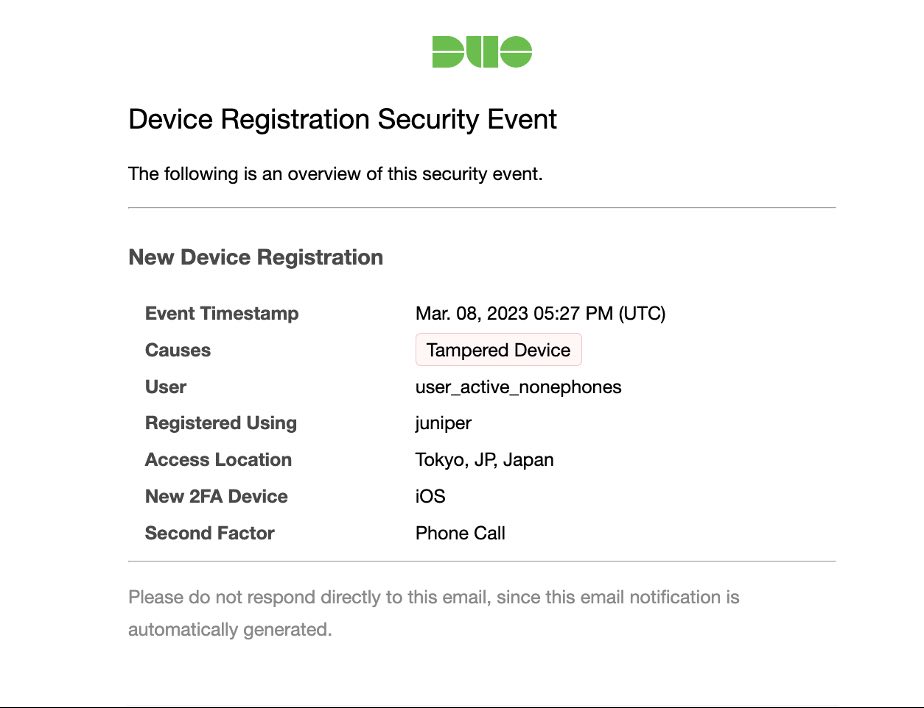
Email Alerting is available to all Duo Advantage and Premier customers at no additional cost.
Start flagging suspicious logins
If you’d like to try Trust Monitor and experience how Duo can help you spot the difference between legitimate and suspicious logins that could be potential threats, sign up for a free 30-day trial.
*This content has been updated after its original publication date in November 2022.

