Documentation
Duo Authentication for Microsoft AD FS 2.1 on Windows 2012 (Deprecated)
Last Updated: March 31st, 2025Contents
Duo integrates with Microsoft AD FS 2.1 to add two-factor authentication to services using browser-based federated logins, complete with inline self-service enrollment and Duo Prompt.
Microsoft ended support for Windows Server 2012 and 2012 R2 on October 10, 2023, therefore Duo's support for AD FS 2.1 on Windows 2012 also ended on that date.
Duo's last day of support for installation and use of any Duo applications on Windows operating systems corresponds with the Microsoft end of support. We strongly urge you to upgrade to a supported version of Windows Server.
The iframe-based traditional Duo Prompt used by Duo for AD FS 2.1 reached its end of support on March 30, 2024. Migrate to AD FS on Windows Server 2016 or later and install the Duo for AD FS v2.x plugin with Universal Prompt for continued support.
The instructions for this solution were removed on March 31, 2025. Customers who had this configuration deployed before then and need to refer to the original instructions to execute the migration to a supported solution may contact Duo Support.
Duo's AD FS 2.x application will not offer support for the Universal Prompt experience. Duo has no plans to release an application update with Universal Prompt support for AD FS 2.x servers. Microsoft ended extended support for Windows Server 2012 on October 10, 2023. You're encouraged to migrate to AD FS on Windows 2016 or later with pluggable multifactor provider support.
Troubleshooting
Need some help? Take a look at the AD FS Frequently Asked Questions (FAQ) page or try searching our AD FS Knowledge Base articles or Community discussions. For further assistance, contact Support.
Network Diagram
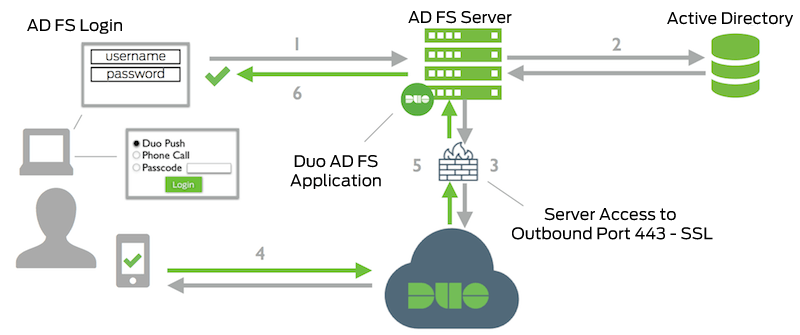
- AD FS connection initiated
- Primary authentication to AD
- AD FS connection established to Duo Security over TCP port 443
- Secondary authentication via Duo Security’s service
- AD FS receives authentication response
- AD FS session logged in
