Documentation
Duo Authentication for Windows Logon (RDP) - Active Directory Group Policy
Last Updated: March 12th, 2025Contents
Duo integrates with Microsoft Windows client and server operating systems to add two-factor authentication to Remote Desktop and local logons. Active Directory domain administrators may deploy or configure Duo Authentication for Windows Logon on domain member workstations using Group Policy Software Publishing and Group Policy Administrative Templates.
Duo Authentication for Windows Logon 4.3.16 and later depend on the Microsoft Visual C++ Redistributable. The Visual C++ Redistributable must be installed separately from Duo Authentication for Windows Logon when using Duo MSI installers. Learn more about MSI deployment.
Requirements
- You should be familiar with using Windows Group Policies for software configuration and distribution.
- Your Active Directory domain should be at Windows 2012 or later functional level.
- You should already have a working Central Store for Group Policy templates.
Review the entire Duo Authentication for Windows Logon product documentation before creating and deploying any group policies for distributing Duo software or client settings.
Duo Group Policy Settings
Client-side configuration options for Duo may be configured via Active Directory Group Policy. The Duo Authentication for Windows Logon Group Policy template lets you configure two types of settings:
- Client Settings determine the end-user experience.
- Duo Service Settings configure communications between the Duo Authentication for Windows Logon application and Duo's cloud service.
The Duo_Authentication_for_Windows_Logon_Group_Policy_Settings.xlsx spreadsheet included in the downloaded zip file describes the Duo Authentication for Windows Logon configurable Group Policy settings in detail. Any setting configured by a GPO is stored as a reg value in HKLM\Software\Policies\Duo Security\DuoCredProv, and overrides the original Duo installation settings (stored in the registry at HKLM\Software\Duo Security\DuoCredProv).
Group Policy configuration settings can be applied to Duo for Windows Logon installations regardless of how the application was originally installed, but if multiple GPOs with Duo settings are assigned to a given system in AD (directly or via inheritance) then each GPO will be applied and the settings from the last policy to be applied become the effective settings.
For additional information about using GPOs and administrative templates, please see Microsoft's Group Policy documentation collection.
Creating the Duo Authentication for Windows Logon GPO
To create and apply the Duo Authentication for Windows Logon Group Policy Object (GPO):
-
Download the Duo Authentication for Windows Logon Group Policy MSI installers, template files, and documentation. View checksums for Duo downloads here.
-
Extract the contents of the zip file and copy the two Group Policy template files into your domain's Administrative Templates store. Note that the two files have different destination folders.
\\your.domain.local\sysvol\your.domain.local\Policies\PolicyDefinitions\DuoWindowsLogon.admx \\your.domain.local\sysvol\your.domain.local\Policies\PolicyDefinitions\en-us\DuoWindowsLogon.adml -
On your domain controller or another system with the Windows Remote Server Administration Tools installed, launch the Group Policy Management console (GPMC).
-
Expand your forest and navigate down the tree to Group Policy Objects. Right-click the Group Policy Objects folder and click New. Enter a name for the new GPO (such as "Duo Windows Logon") and click OK.
-
Right-click the new GPO created in step 4 and click Edit. Navigate to Computer Configuration\Policies\Administrative Templates and expand Duo Authentication for Windows Logon.
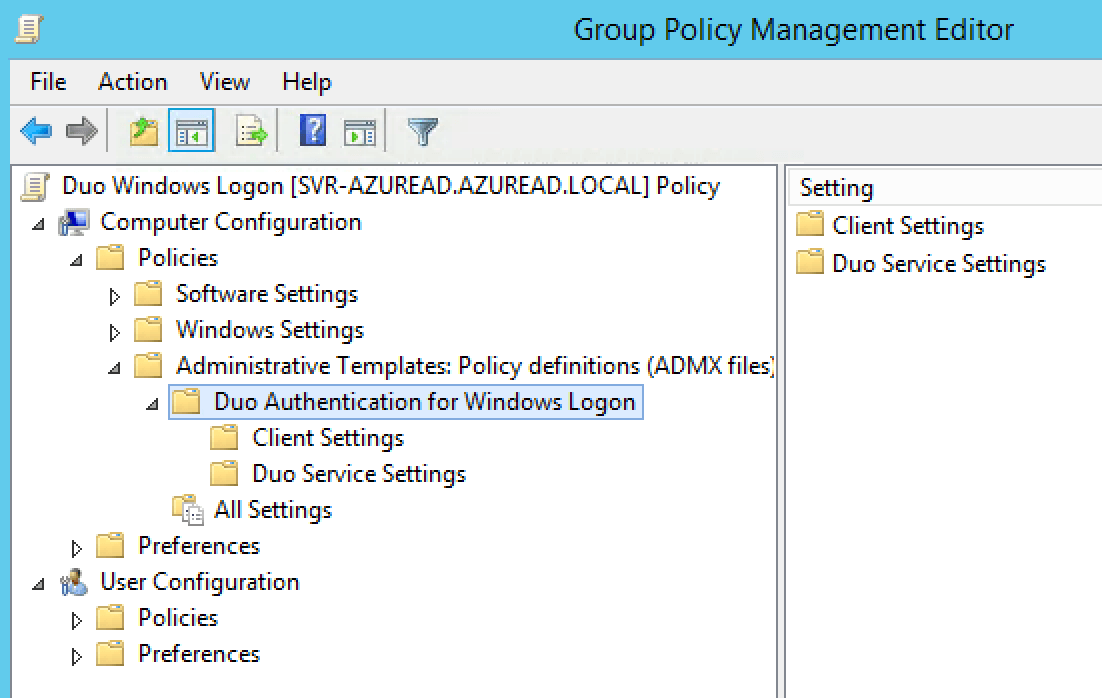
-
Double-click a setting to configure it. When you've finished configuring settings, close the policy editor.
-
Once returned to the Group Policy Management window, click on the Delegation tab for your new Duo GPO and then click the Advanced button. Click on the Authenticated Users group in the list and then click Remove.
Then, click Add... and type in Domain Computers, and then click OK. Check the permissions boxes in the "Allow" column to grant the "Domain Computers" group both Read and Apply group policy permissions. Click OK to apply the new delegated permissions.
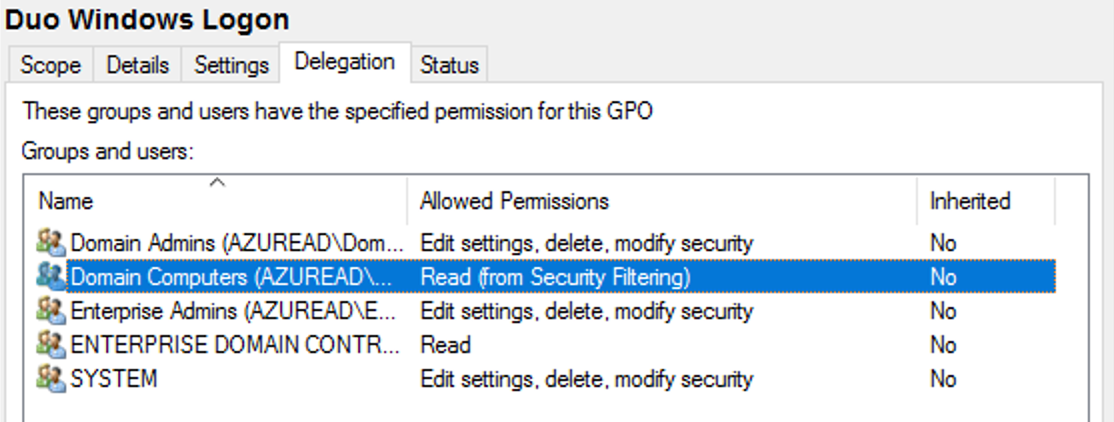
-
Apply the new GPO for Windows Logon to domain member workstations by linking the policy to the desired OU.
For additional information about using GPOs and administrative templates, please see Microsoft's Group Policy documentation collection.
If you choose to remove the "Authenticated Users" group from the GPO's "Security Filtering" properties then be sure to replace it with a group that contains the computers to which you want this GPO to apply. Consider preventing read by user accounts to prevent exposure of the Duo secret key.
Securing the Group Policy Registry Key
When Duo Authentication for Windows Logon is installed interactively, the default Duo settings registry key HKLM\Software\Duo Security\DuoCredProv permissions are restricted by the installer so that unprivileged users may not read the Duo application secret key (SKey) and other application information from the registry. These updated permissions take effect on the DuoCredProv key after the first user authentication on that system after Duo installation.
Configuring Duo Authentication for Windows Logon via Group Policy after installation creates an additional registry key at HKLM\Software\Policies\Duo Security\DuoCredProv with the GPO settings.
Duo Authentication for Windows Logon secures both HKLM\Software\Duo Security\DuoCredProv and HKLM\Software\Policies\Duo Security\DuoCredProv registry keys when Duo's credential provider is invoked.
When creating a GPO with Duo Authentication for Windows settings, you can further restrict permissions on the policy's registry key to ensure that unprivileged users may not view the application information when the GPO refreshes. You can add the registry restriction to the same GPO where you configured the Windows Logon client and service settings.
-
Open the Duo Authentication for Windows Logon GPO you created earlier, or create a new Group Policy object in your domain just to secure the policy registry key.
-
Navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Registry. Right-click Registry and select Add Key...
-
In the "Select Registry Key" window, expand MACHINE, click on SOFTWARE and append \Policies\Duo Security\DuoCredProv in the Selected key: box, so the full selected key text reads MACHINE\SOFTWARE\Policies\Duo Security\DuoCredProv. Click OK.
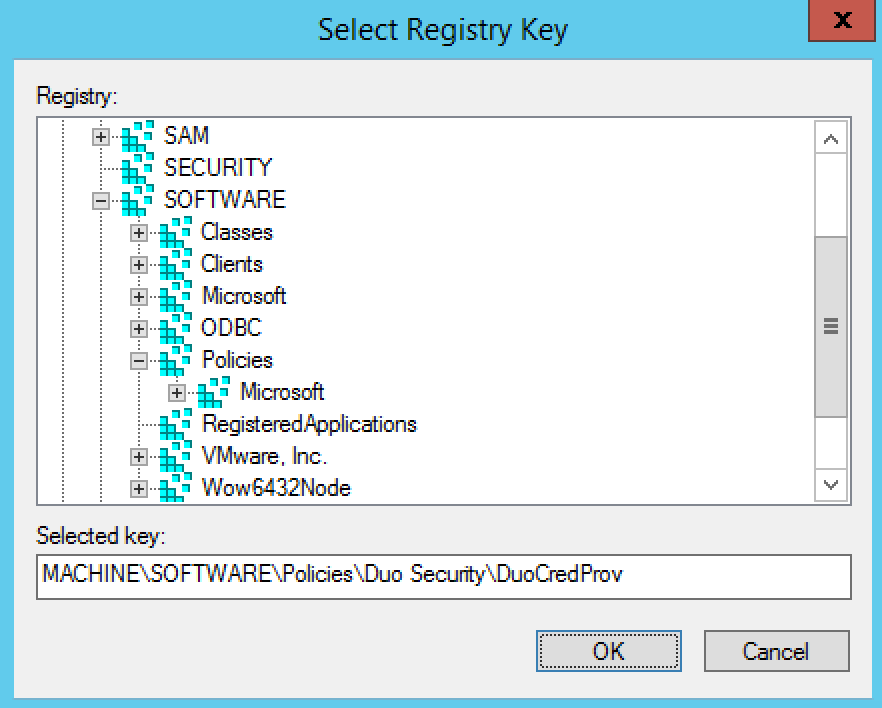
-
On the "Database Security for MACHINE\SOFTWARE\Policies\Duo Security\DuoCredProv" window, select the ALL APPLICATION PACKAGES object and click the Remove button. Repeat the removal step for the Users object. Click OK when done.
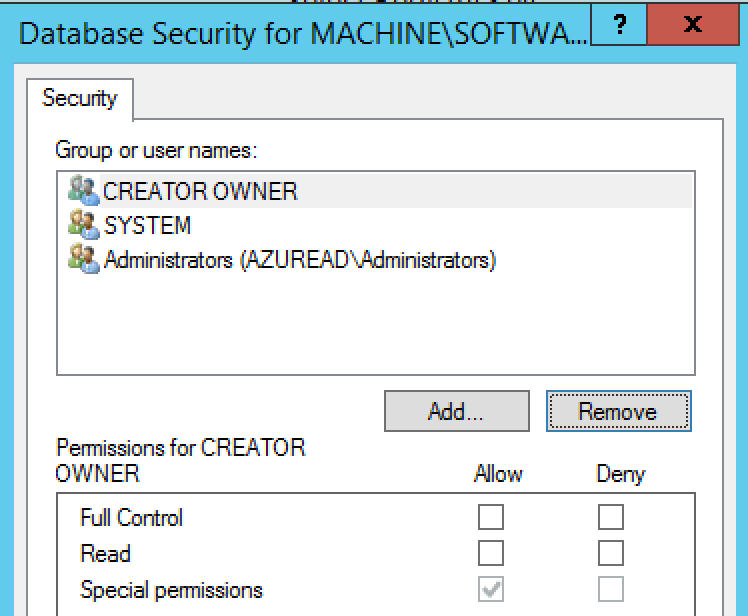
-
Click OK on the "Add Object" window to propagate inheritable permissions to subkeys.
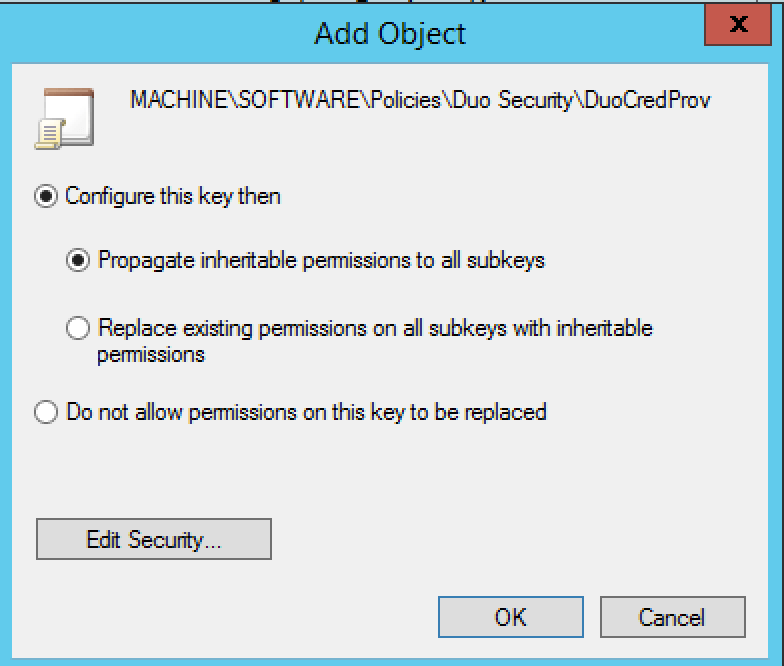
-
Close the Group Policy editor to save the change.
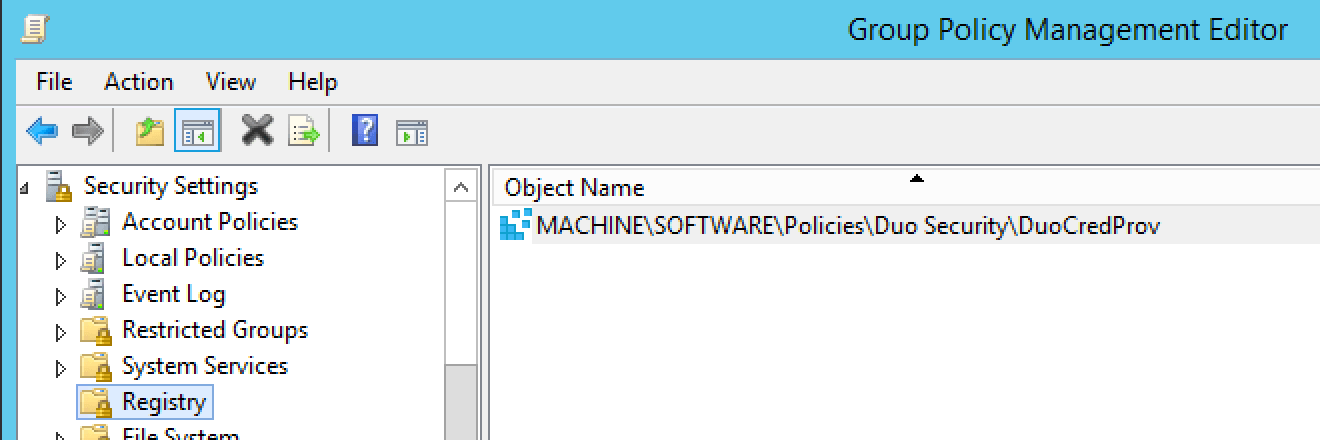
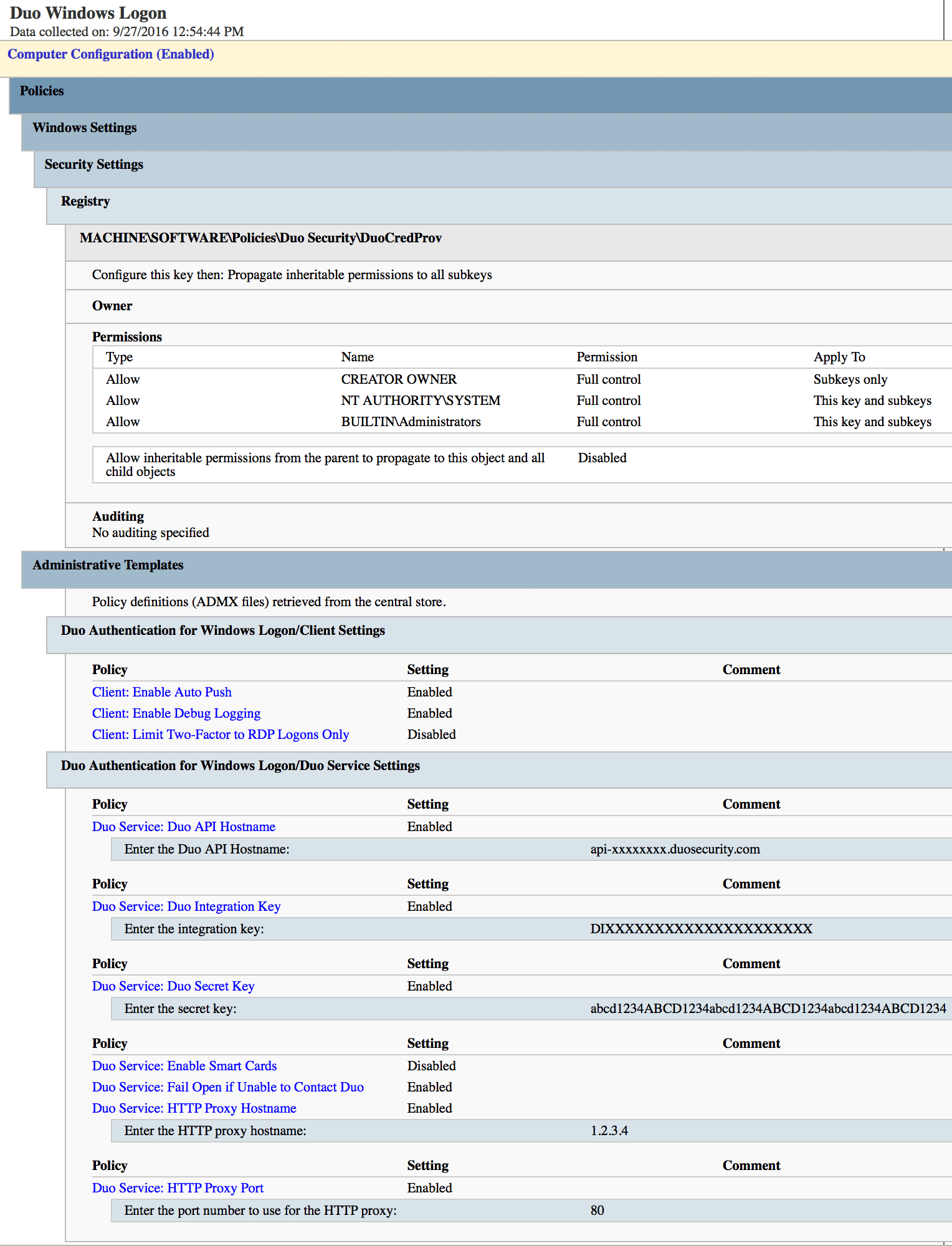
Here's an example of a Duo Authentication for Windows GPO containing both client and service settings and with the registry key permissions secured by the GPO:
Contents of ZIP file
The following files are included in the Duo Authentication for Windows Logon GPO ZIP file:
Duo_Authentication_for_Windows_Logon_Group_Policy_Settings_vN.N.N.xlsx: An Excel file describing all the GPO options available. vN.N.N will reflect the actual release version.DuoWindowsLogon32.msi: The 32-bit MSI installer.DuoWindowsLogon64.msi: The 64-bit MSI installer.DuoWindowsLogon.admx: The group policy template.DuoWindowsLogon.adml: The group policy language file.
Deploying Duo Authentication for Windows Logon to clients using Active Directory
Installing Duo Authentication for Windows Logon immediately requires users to log on with Duo two-factor authentication. You must either enroll your users in Duo before installing the application, or adjust the policy settings for the application to allow access without 2FA.
Please see the Duo Authentication for Windows Logon application documentation for more information.
Duo Authentication for Windows Logon may be deployed via a Group Policy software installation package, with or without accompanying client-side Duo settings specified in the same GPO.
Use the MSI installers included in the zip file you downloaded earlier. We provide both 32-bit and 64-bit MSI files. Do not rename the MSI install files! Changing the names of the MSI files can cause installation or later upgrades to fail.
To avoid overwriting these MSI install files with the installers for a different version we recommend you keep the MSI files for each Duo Windows Logon release in a unique, per-version subdirectory.
Visual C++ Redistributable Requirement
Duo Authentication for Windows Logon 4.3.16 and later depend on the Microsoft Visual C++ Redistributable.
Duo MSI installers (DuoWindowsLogon32.msi or DuoWindowsLogon64.msi) used for software deployment via GPO do not install the Visual C++ prerequisite package, nor do they prevent installation of Duo if the Visual C++ Redistributable is not present on the target system. The Visual C++ Redistributable must be installed separately from Duo Authentication for Windows Logon when using the Duo MSI installers.
If you use an endpoint management tool to distribute Duo for Windows Logon to your organization's Windows systems you should also distribute the Visual C++ package to your managed clients as well prior to pushing out the Duo install.
Microsoft only provides the Visual C++ Redistributable installer for download as an EXE. Most endpoint management systems support packaged deployment of EXE installers to target system. However, Microsoft Group Policy software publishing only permits publishing of MSI packages.
To use a GPO to deploy the Visual C++ package to domain-joined clients, you may need to obtain the MSI from a system where you have already installed the Visual C++ package. Please see this external guide for a method of extracting the MSIs from an existing installation: Extract MSI from Visual C++ 2012 Redistributable.
The GUIDs for the latest Visual C++ Redistributable release components (14.42.34438 as of March 7, 2025) are:
{2E15F519-4FDA-4834-B4EE-7EFCE7D8D4EE} Microsoft Visual C++ 2022 X64 Minimum Runtime - 14.42.34438
{E528AD94-12D7-42C4-91A3-908BE28E9BD2} Microsoft Visual C++ 2022 X64 Additional Runtime - 14.42.34438You may also try a scripted installation of the Visual C++ EXE. Here is an example of a batch file that checks the system architecture then installs the 64-bit or 32-bit package as required from the EXE installer located in the same directory as the script: Stack Overflow: how to automatically install Visual C++ Redistributable for Visual Studio 2015.
Deploy Duo Authentication for Windows using Group Policy Software Deployment
-
Download the Duo Authentication for Windows Logon Group Policy MSI installers, template files, and documentation. View checksums for Duo downloads here.
-
Extract the contents of the zip file and copy the subdirectory containing the DuoWindowsLogon32.msi and DuoWindowsLogon64.msi files to your centralized software deployment share. Your software share and the Duo MSI files should be readable by "Domain Computers", as Duo for Windows Logon gets installed during the pre-logon group policy processing phase of the boot process and not under the context of any named user.
Remember, do not rename these MSI files.
-
Create a transform for the installer file by using a table editor tool like Orca (distributed as part of the Windows SDK) to deploy the Duo Windows Logon client with initial configuration.
-
If you are using Orca, open the Duo Windows Logon MSI 32-bit or 64-bit file in the editor, and go to Transform → New Transform.
-
Click on the Property table, and add these new rows using your Duo RDP application's information from the Duo Admin Panel:
Property Value IKEY Your Duo integration key SKEY Your Duo secret key HOST Your Duo API hostname 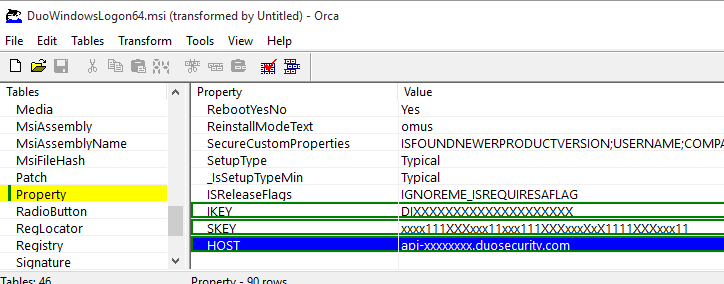
-
Go to Transform → Generate Transform... to create the MST file with your changes.
-
Close Orca after generating the transform MST file, and do not save any changes to the MSI file itself.
-
Copy the new transform file to your central application deployment share alongside the Duo Windows Logon MSI installers. The share with the MST file should not be readable by unprivileged user accounts to prevent exposure of the Duo secret key.
-
-
In the Group Policy Management console, create a new GPO for Duo Authentication for Windows publishing. Navigate to Computer Configuration\Policies\Software Settings\Software installation then right-click and select New > Package. This pops up a file browser window.
-
Use the file browser to navigate to the software deployment share where you put the Duo MSI installer and the MST transform files. Select the network accessible DuoWindowsLogon32.msi or DuoWindowsLogon64.msi installer package from your software deployment share and choose Advanced as the deployment method.
-
Go to the Modifications tab in the properties window. Click the Add button and select the MST transform you created earlier in step 3.
-
Click OK to finish, and the Duo Authentication for Windows Logon software package is created. When you've finished, close the policy editor.
-
Apply the new software publishing GPO for Windows Logon to domain member workstations by linking the policy to the desired OU. The target client workstations need a reboot to apply the new GPO settings and install Duo.
Here's a sample software publishing policy for Duo Authentication for Windows Logon v2.0.0.71 64-bit, showing use of a transform file (AcmeDuoWinLogon.mst).
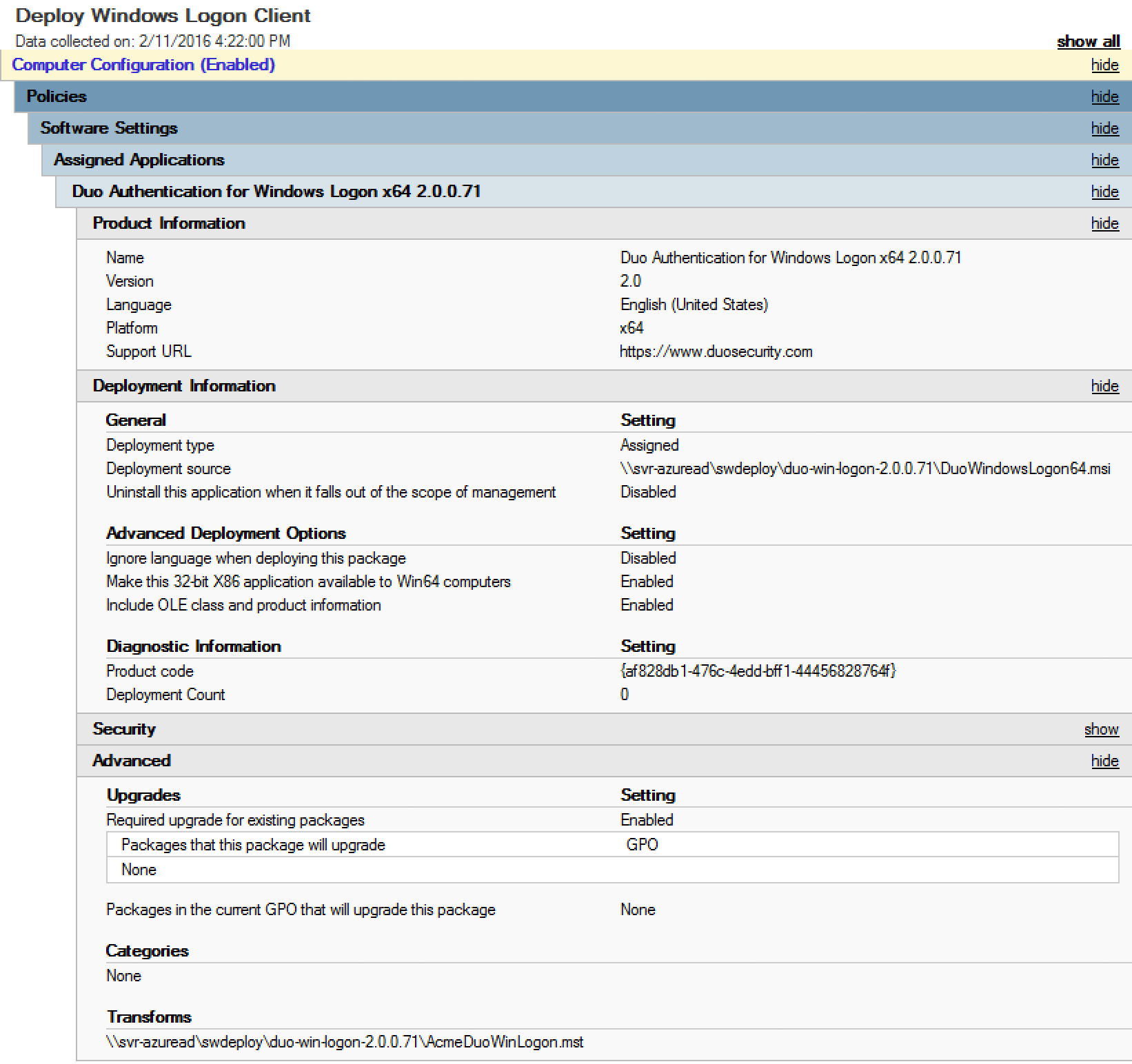
Learn more about installing software using Group Policy at Microsoft Support.
Troubleshooting
Need some help? Take a look at the Windows Logon Frequently Asked Questions (FAQ) page or try searching our Windows Logon GPO Knowledge Base articles or Community discussions. For further assistance, contact Support.
