Contents
Welcome to Duo Security’s Federal Guide to Duo’s FedRAMP Authorized Federal Editions. All Federal Edition product differences outlined within this guide were completed to ensure product alignment with FedRAMP/NIST 800-53 security controls, NIST’s Digital Identity Guidelines (SP 800-63-3), and FIPS 140-2 compliance requirements for Duo’s US Federal/Public Sector customers. Learn more about Duo’s Federal Editions.
Duo’s FedRAMP Package for Duo’s Federal Editions
If you’re a US Federal Agency and you need to access Duo’s FedRAMP Authorization Package please leverage OMB’s MAX Portal or contact your Duo Federal Account Executive.
Starting a Trial of Duo's Federal Editions
To sign-up for Duo’s federal editions, please fill out the contact form on Duo's Federal Editions page. Once submitted, Duo will reach out to qualify and confirm eligibility to ensure customers are federal agencies, federal contractors, public sector entities, or Cloud Service Providers (CSPs) pursuing FedRAMP.
Connectivity Requirements
Duo’s integrations communicate with Duo's service via HTTPS on TCP port 443, for both commercial and federal editions.
Firewall configurations that restrict outbound access to Duo's service with rules using destination IP addresses or IP address ranges aren't recommended, since these may change over time to maintain our service's high availability. If your organization requires IP-based rules, please contact your Account Team or Support Team for additional information.
Many of Duo’s applications support the use of an HTTP proxy to provide connectivity to Duo. Check the documentation or FAQs for the Duo applications you will be deploying to determine if they support HTTP proxy.
Comparing Duo Federal Editions with Duo's Commercial Editions
Duo's federal and commercial editions use the same core components and are administered in the same way, via the Duo Admin Panel. Most administration and deployment tasks in Duo federal editions use the same published instructions available at /docs.
This document describes how Duo's federal editions differ from Duo’s commercial editions.
Available Editions
Duo offers Federal Essentials and Federal Advantage subscription plans. Duo Network Gateway is not available in the federal editions.
Duo Service Connectivity
Duo's federal editions strictly require TLS 1.2 secured communications. Ensure that your Duo application versions and the operating systems of the hosts where you install Duo applications also support TLS 1.2.
Additionally, the API host domain for federal editions is duofederal.com instead of the duosecurity.com domain used by Duo commercial editions.
FIPS-Validated Secret Generation
Duo randomly generates 40-character application secret keys ("skeys") and client secrets with FIPS-validated Deterministic Random Bit Generators (DRBG) using the Cisco FIPS Object Module.
Token Restrictions
Duo federal editions customers may not purchase Duo-provisioned D-100 tokens from Duo for authentication needs. Your organization must purchase your own third-party tokens and import them into Duo.
FIPS Enforcement in Duo Mobile
Duo Push and Duo Mobile passcode authentication methods on iOS 6 and later and on Android (as of Duo Mobile version 3.25.0) are FIPS 140-2 compliant by default with no configuration required by administrators. Learn more about Duo Mobile FIPS support in Duo’s Knowledge Base.
Excluded Features
Duo Federal plans exclude these Duo features and functionality.
Duo Network Gateway
Duo Network Gateway, a reverse proxy for on-premises web application, RDP, and SSH connectivity with MFA, is not available in federal editions.
Duo Single Sign-On
Duo Single Sign-On, our hosted SAML 2.0 identity provider, is not available in federal editions. You may use Duo Access Gateway, our on-premises SAML identity provider, with your Duo Federal customer account to provide single sign-on for applications.
The end-of-support information and dates published on the Duo Access Gateway documentation pages apply to Duo's commercial editions. Duo Federal customers continue receiving full support for Duo Access Gateway beyond the commercial end-of-support.
Duo Trust Monitor
Duo Trust Monitor, which analyzes and models authentication telemetry in order to highlight potentially suspicious user and device access activity, is not available in federal editions.
Risk-Based Authentication
Risk-Based Authentication detects risk and automatically provides step-up authentication verification, and is not available in federal editions. However, Verified Duo Push as a static authentication methods option is available in Duo Federal.
Duo OIDC Factor for Okta MFA
The Duo custom OIDC factor for Okta, which offers Universal Prompt, is not available with federal editions. You may use the traditional Duo Prompt Okta MFA Factor with a Duo Federal plan.
Available Features with Caveats
These Duo features and software applications have additional requirements (or limitations) for operation or use with Duo Federal plans.
Duo Access Gateway
Duo Access Gateway (DAG) remains fully supported for Duo Federal customers beyond the October 26, 2023 end-of-support date for Duo commercial customers. New feature development for Duo Access Gateway has ended, but we will provide Duo Federal customers with bug fixes and security updates when applicable.
Enabling the Duo Universal Prompt for DAG SAML applications requires upgrading to Duo Access Gateway for Windows 2.0.0 release. After installing the update, you must authenticate once to each individual SAML service provider through the upgraded DAG to unlock the Universal Prompt activation control for each application.
Duo for Microsoft Entra ID External Authentication Methods (EAM)
Duo's commercial and federal editions offer Duo as an Entra ID external authentication method for Microsoft EAM, applied via Entra ID conditional access. Entra ID external access methods are available in Microsoft's Commercial and Government tenants. While Azure Government High (GCC High) does support Entra ID external authentication methods, Duo Federal is not available within FedRAMP High. Therefore, GCC High customers may not use Duo EAM.
Duo Custom Control for Microsoft Entra ID Conditional Access
Duo's commercial and federal editions support Entra ID conditional access via a "Microsoft Azure Active Directory" custom control application, which can be used with Microsoft's commercial tenants. Microsoft’s Government Cloud added support for custom controls for Entra ID conditional access, but the Duo custom control remains unavailable in Entra GCC.
Logging and Reporting
Logs and reports in Duo Federal may not show the same level of detail or full complement of events available in commercial Duo editions. Data is only stored for 180 days.
Duo Universal Prompt
Duo Federal customers may use OIDC-based Auth API applications and enable Duo Universal Prompt for supported applications. Note specific excluded applications or restricted features affecting Universal Prompt availability for federal plans in the Excluded Features section of this document.
Universal Prompt support for Duo Access Gateway is available to Duo Federal customers. Please contact Duo Support or your Duo account team for details.
The other applications not in-scope for Universal Prompt remain the same for both Duo Federal and Duo commercial editions.
Duo Federal's Universal Prompt feature availability matches the feature availability for Duo commercial customers, with the following exceptions:
-
Universal Prompt is not enabled as the default experience for newly-created supported applications in Duo Federal accounts.
-
Self-enrollment: new users performing first-time Duo enrollment from a Duo Federal tenant application with Universal Prompt activated or using an enrollment link emailed to the user will fall back to the traditional prompt experience.
-
Self-service device management: there is no link in the Duo Federal Universal Prompt for previously enrolled users to add a new device or manage existing devices. The recommended workaround for this is to make self-service device management available in an application still using the traditional prompt.
Custom Branding
Duo Federal customers may upload a custom logo, turn Duo branding on and off, and set a custom help messsage in Settings. Additional custom branding options for the Universal Prompt, like setting an accent color or background image for the prompt, and the ability to save draft customizations and pilot them with selected users, are not available in Duo's federal editions.
Entra ID Directory Sync
Duo's federal editions include the Entra ID Directory Sync feature as of October 2020. This permits importing users into Duo from Entra ID in Microsoft Cloud commercial and government tenants, but not from Microsoft GCC High tenants.
The Administrator Sync portion of Entra ID Directory Sync is currently excluded from Duo federal editions.
Active Directory/OpenLDAP Directory Sync
The Administrator Sync portion of Active Directory Directory Sync and OpenLDAP Directory Sync is currently excluded from Duo federal editions.
Duo Authentication Proxy
The Duo Authentication Proxy is an application you install on your network. It’s used for Active Directory and OpenLDAP sync of your users into Duo, and for RADIUS and LDAP two-factor authentication for your on-premises VPNs, services, and applications.
The Duo Authentication Proxy is FIPS-compliant when it is installed on a Windows or Linux system with FIPS enabled at the operating system level, and you enable the FIPS option in the Duo proxy configuration file. LDAPS is the only FIPS-compliant authentication method.
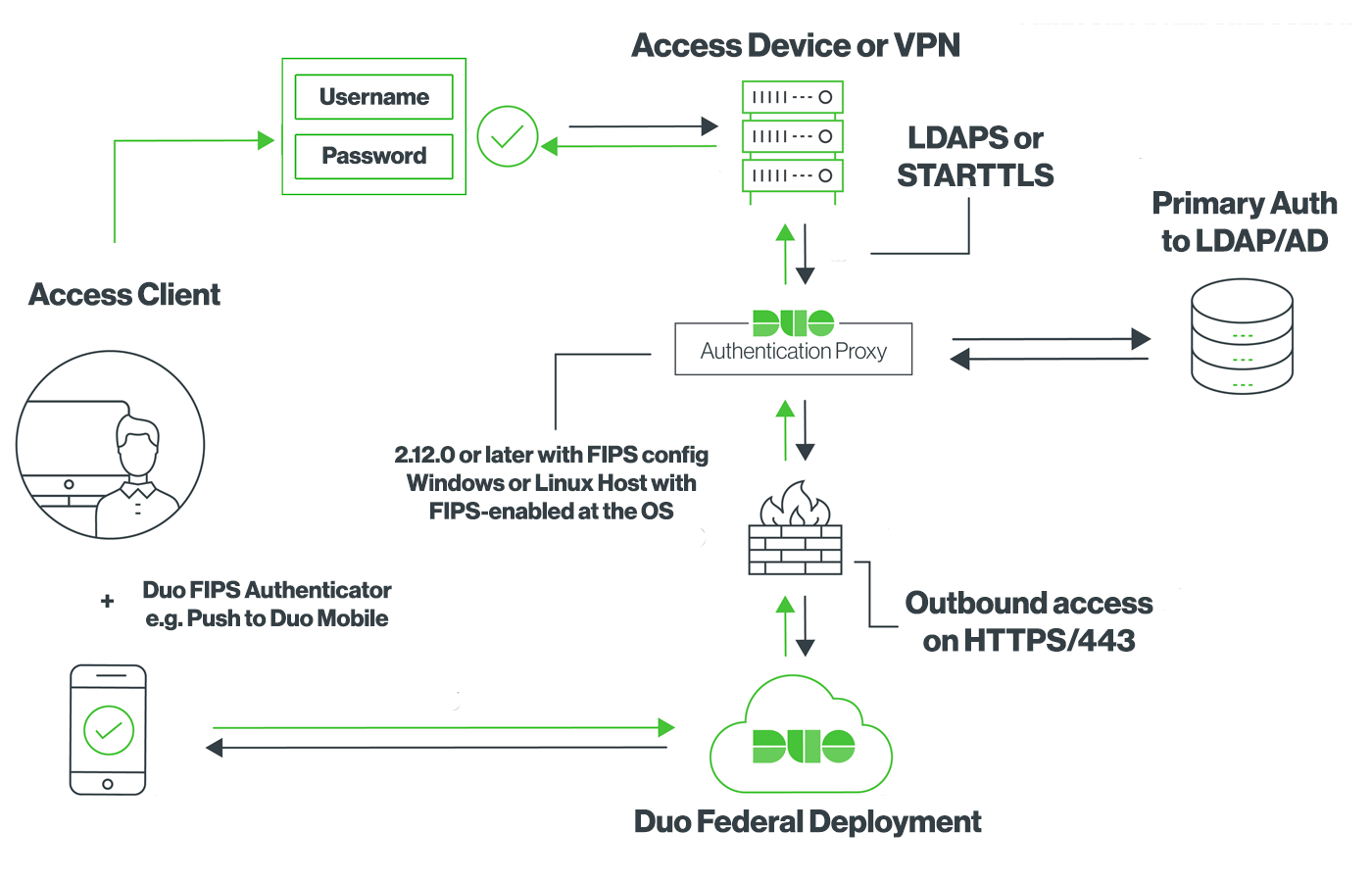
See the documentation to learn more about deploying the Duo Authentication Proxy in FIPS mode.
Duo Unix
Duo Unix is FIPS-compliant when run on a Unix or Linux system with the operating system-wide FIPS mode enabled.
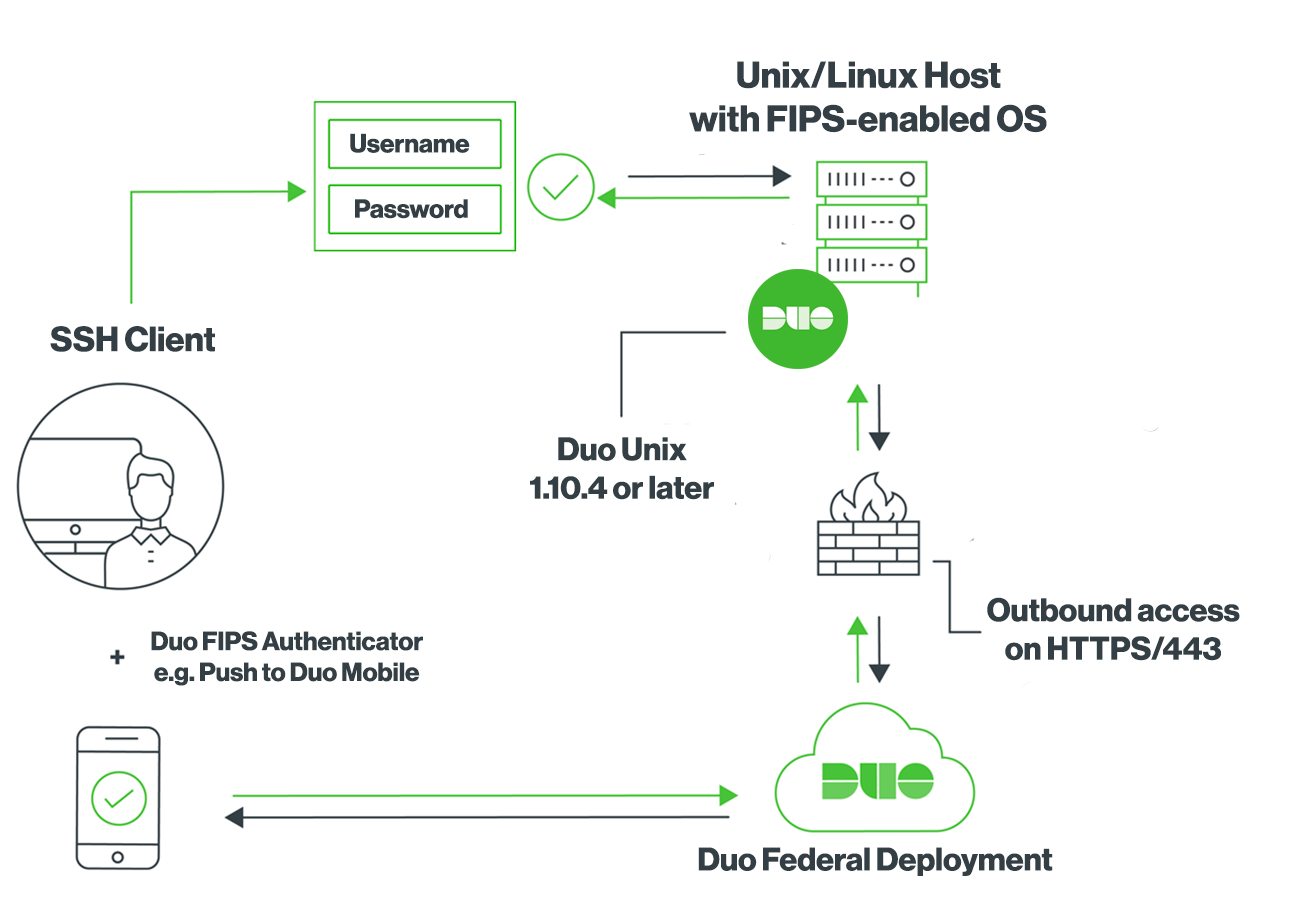
See the documentation to learn more about Duo Unix in FIPS mode.
Duo Authentication for Windows Logon
Duo for Windows Logon application v4.0.7 is the minimum supported version for federal edition customers. For the best results, we recommend installing the latest available version.
Duo for Microsoft AD FS
Duo for AD FS supports AD FS installed on Windows 2016 and later, with version 1.2.0.17 or later of the Duo MFA adapter. You must enable TLS 1.2 for .NET Framework 4.5 by creating the following registry values on your AD FS server before installing Duo MFA:
HKLM\Software\Microsoft\.NETFramework\v4.0.30319]
"SchUseStrongCrypto"=dword:00000001
[HKLM\Software\Wow6432Node\Microsoft\.NETFramework\v4.0.30319]
"SchUseStrongCrypto"=dword:00000001
Learn more about TLS Best Practices for .NET at the Microsoft site.
Duo Splunk Connector
Ensure that you are using version 1.1.6 of the Duo Splunk Connector. Previous versions experience configuration issues against Duo Federal deployments.
Auth API
No telephony options may be used with Duo Auth API applications. This affects the API /auth endpoint as follows:
- Disables use of the "phone" factor value
- Disables use of the "sms" factor value
- The "auto" factor will not choose "phone" or "sms"
Duo Desktop
Duo's commercial and federal editions include Duo Desktop for trusted device verification, app requirement, and secure device registration policy options. Duo Federal Advantage edition also includes Duo Desktop for device health checks. Duo Desktop as an authentication method is not available in Duo's federal editions.
Trusted Endpoints
Duo's Federal customers may use the Manual Enrollment management integration. All other management integrations are not available in Duo's federal editions.
Telephony Restrictions
Duo's federal edition customers may not use any of telephony features in Duo’s commercial service. Duo removed telephony authenticators from our federal editions to provide alignment with NIST 800-63-3b AAL2 requirements by default, as NIST labels telephony authenticators as "RESTRICTED". This restriction affects how federal administrators and end users get created or enrolled in Duo, and how they log in using Duo.
Telephony Restrictions for Admins
- Duo Administrators may only log in using Duo Push or a passcode from a hardware token. SMS passcodes and phone call authentication may not be used.
- When creating a new Duo administrator, the admin must activate Duo Mobile (or be assigned a hardware token) before that new admin may log in.
- Duo admins may only email activation links to users, and cannot send the activation links via SMS.
- The Duo Admin Panel’s global Settings page does not show the Phone Calls and SMS Passcodes options.
- The Duo Admin Panel does not show the Telephony Credits information and Billing page.
- The Duo Admin Panel does not show the Telephony Log.
- The Admin Authentication Methods setting does not include Phone Callback or SMS Passcodes. It is not possible to enable these methods for use by administrators.
Telephony Restrictions for End Users
- The Authentication Methods policy settings (which affect end user logins) do not show the Phone Callback or SMS Passcodes options. It is not possible to enable these methods for use via policy.
- When creating a new end user, or when an end user performs self-enrollment in Duo, a phone number is collected but is only used as an identifier for the user's device and is not used for phone call or SMS authentication purposes.
- End users may only enroll iOS or Android smartphones and tablets for use with Duo Mobile. End users may not enroll generic smartphones, landlines, or Windows Phone devices, and these platforms and device types are not offered during enrollment.
- End users may not approve Duo authentication requests using phone calls or SMS passcodes. End users see no mention of SMS passcodes or phone calls in the Duo Prompt and may not use phone call verification or send passcodes via SMS to themselves to log in from any phone.
- When configuring their default device options, end users may only choose between the "Ask me to choose an authentication method" or "Automatically send this device a Duo Push" options. The "Automatically call this device" option is not presented.
- An end user may not enroll a device in Duo using an existing phone number, as there is no way to verify ownership of the device using phone call or SMS. End users must contact a Duo administrator to activate a shared device.
Duo Administrator Creation
The Duo administrator password default requirement specifies at least twelve (12) characters. The minimum password length may be modified in the Admin Password Policy settings area of the global Settings page.
New passwords will be checked against common passwords, usernames, and other account information to ensure uniqueness. Federal editions do not provide the administrator password complexity options available in commercial editions.
When creating a new Duo administrator, the only option for secondary authentication is to select a hardware token previously imported into Duo. Once you save the new administrator, you may also choose to activate Duo Push or add a passkey. If you do not choose one of these options, then the new administrator can’t log in.
Duo Administrator Logins
All Duo administrators access the Duo Admin Panel to configure their Duo service and users. When logging in to the Duo Admin Panel as a Duo federal edition customer, you’ll note some differences to the documented login process:
Log In URL
Use your unique customer admin URL to access the Duo Admin Panel, e.g. https://admin-abcd1234.duofederal.com. Do not use https://admin.duosecurity.com.
Secondary Factor Restrictions
Duo's federal editions may not use telephony-related features. Duo administrators must authenticate using Duo Push on a smartphone with the Duo Mobile app, a passcode from a hardware token, or a passkey. A Duo admin without either of these secondary authenticators may not log into the Duo Admin Panel.
System Use Notification
Duo's federal edition administrators must accept the login warning shown or be denied access.
PIV/CAC SmartCard Compliance
Enable Single Sign-on with SAML for the Duo Admin Panel utilizing an external IdP (AD FS, or Entra ID, for example) for IdP PIV/CAC SmartCard authentication capabilities. Setting “Authentication with SAML” to Required ensures that Duo administrators assigned any role besides “Owner” can't access the Admin Panel without the respective authentication method. Duo administrators with the “Owner” role may choose to sign in with a password, bypassing the external IdP and any PIV/CAC SmartCard authentication enabled therein.
See the documentation to learn more about SAML single sign-on for the Duo Admin Panel.
End User Lockout and User Deletion
Duo federal customers have the following Lockout and Fraud defaults:
- The default lockout threshold is three (3) failed attempts.
- The default lockout expiration time is thirty (30) minutes
Additionally, the default user deletion periods are ninety (90) days for inactivity and seven (7) days trash duration.
Duo End User Enrollment and Logon
The telephony restrictions in Duo's federal editions change the end-user device enrollment and authentication experience. Note that you can achieve similar restrictions via policy settings as a Duo commercial edition customer, but in Duo's federal editions these restrictions may not be removed or reverted.
Restricted Device Types and Platforms
Users may not enroll or authenticate with the following device types and platforms:
- Landlines
- Windows Phone mobile phones
- Other cell phones and feature phones
Users may enroll and authenticate with:
- iOS and Android mobile phones
- iOS and Android tablets
- Security keys (in supported browsers)
- Touch ID (on supported Mac hardware)
Changes to the User Interface
The Duo enrollment and authentication interface hides the disallowed platforms and device types from end users.
| Federal Editions | Commercial Editions |
|---|---|
Enrollment Device Options:No Landline Option 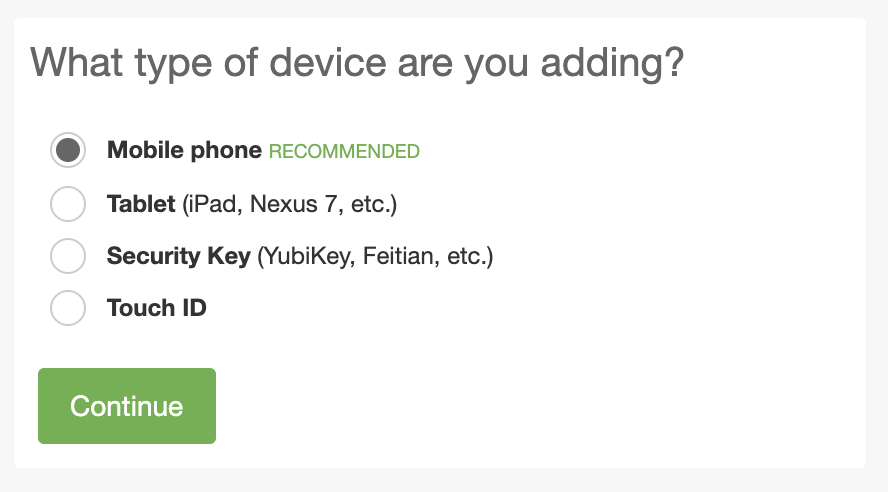 |
Enrollment Device Options:Has Landline Option 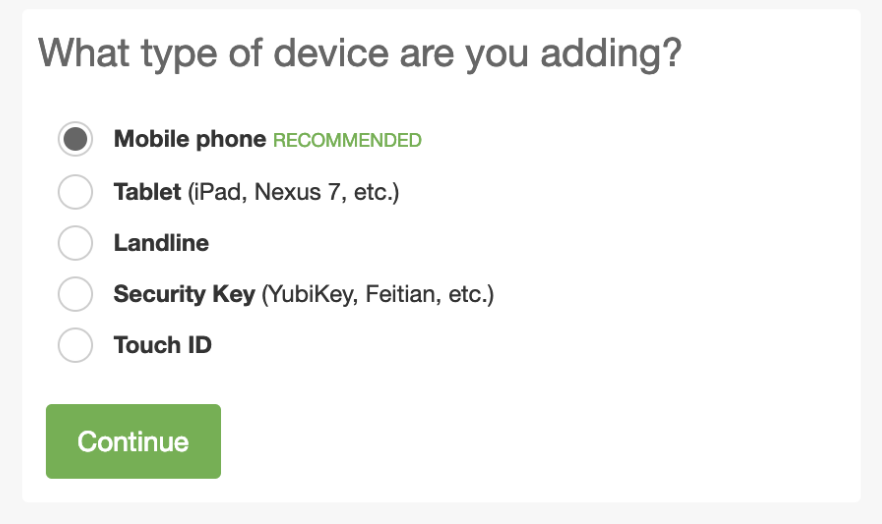 |
Enrollment of Existing Device:Cannot Enroll with an Existing Phone Device 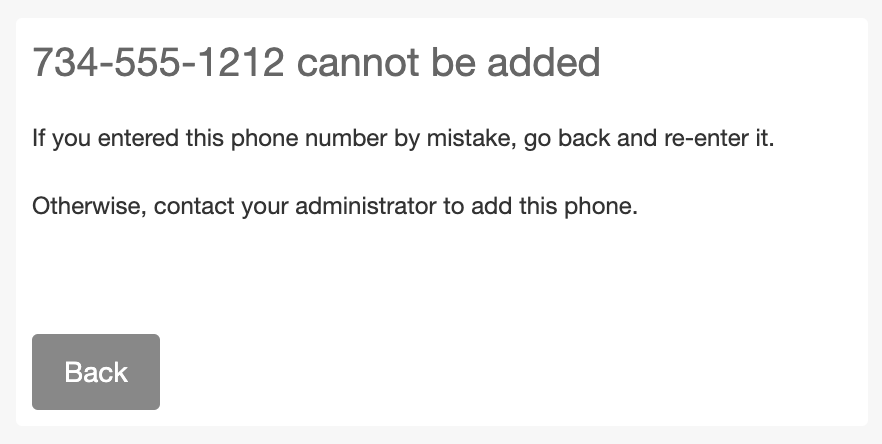 |
Enrollment of Existing Device:Verify an Existing Phone Device During Enrollment 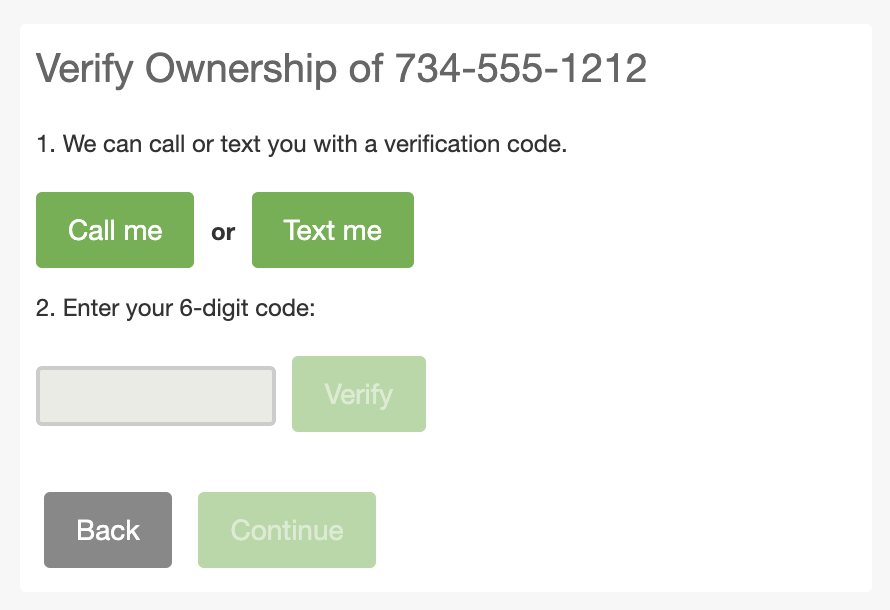 |
Enrollment Phone OS Options:iPhone and Android Only 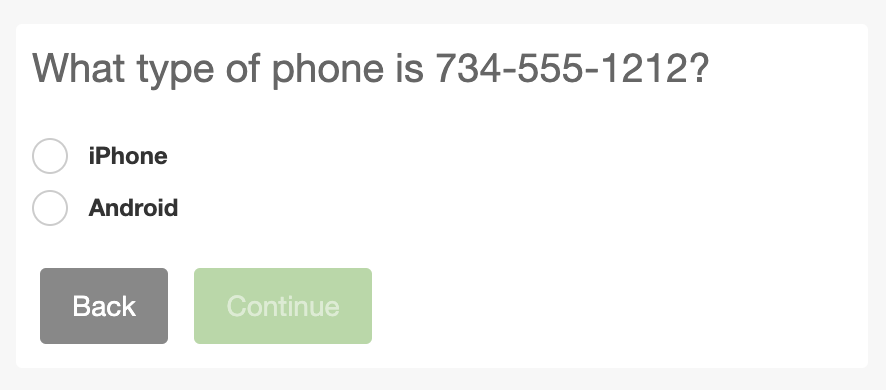 |
Enrollment Phone OS Options:iPhone, Android, Windows Phone, or Other 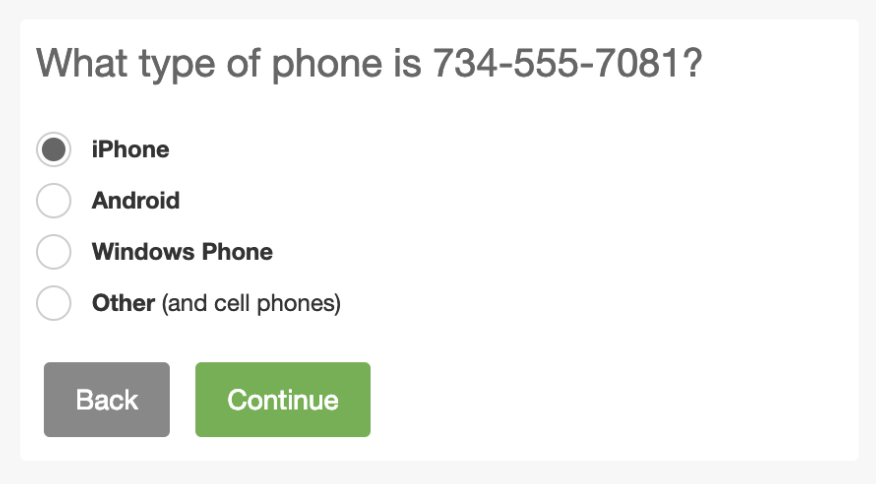 |
Automatic Authentication Actions:No Automatic Call 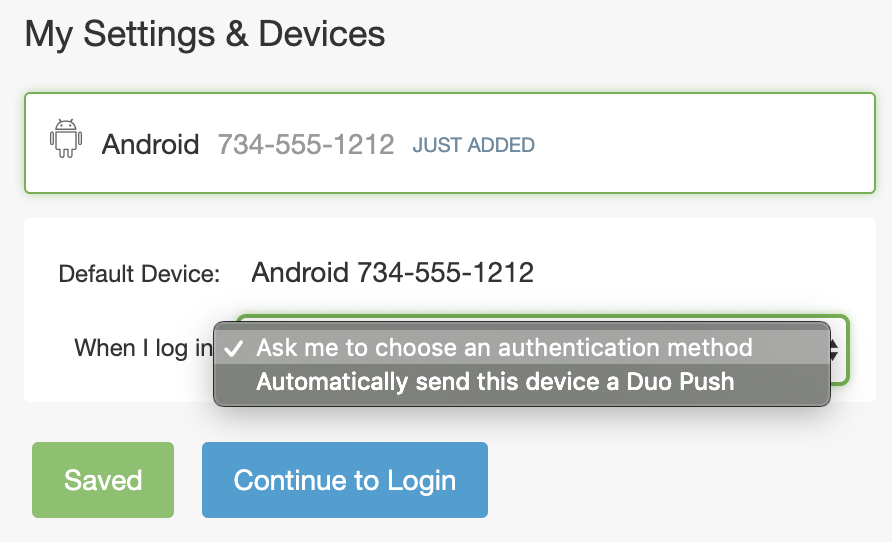 |
Automatic Authentication Actions:May Choose Automatic Call 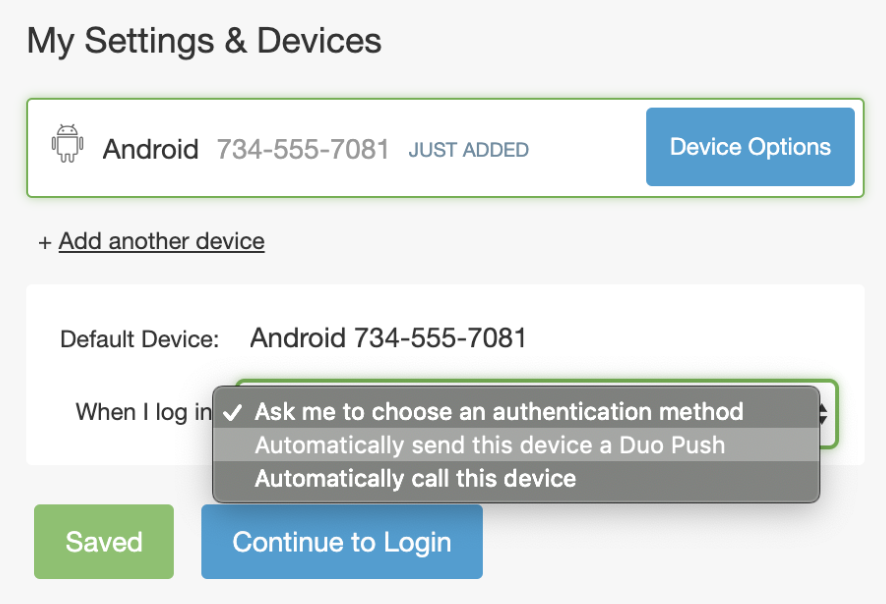 |
Authentication Factor Options:No Phone Call Option 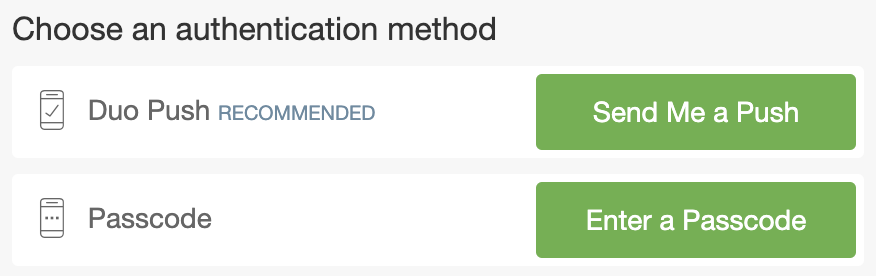 |
Authentication Factor Options:Phone Call Option 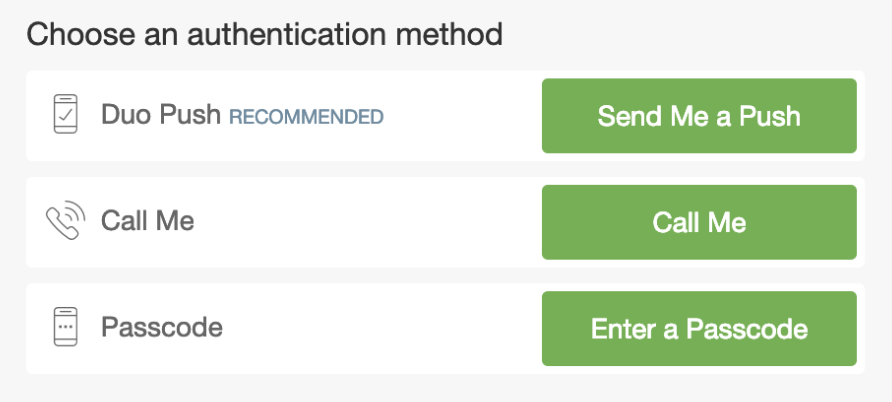 |
Authentication with SMS Passcode:No option to send SMS Passcodes  |
Authentication with SMS Passcode:Option to send SMS Passcodes Present  |
Changes to Auto Push and Append Applications
With some Duo applications do not show the interactive Duo Prompt. These are typically applications that use RADIUS auto or LDAP authentication through the Duo Authentication Proxy or Duo for Microsoft Remote Desktop Gateway. Instead of allowing the end user to interactively choose which authentication method to use, these integrations perform an automatic push (if Duo Mobile was activated for the end user) or phone callback (if the user has an attached phone without Duo Mobile activation).
In Duo federal editions, these configurations will not perform an automatic phone call for authentication. If a user has a device activated for Duo Push, they receive an automatic push request. If the user has no device activated for Duo Push, then the login attempt fails.
In some auto push configurations the end user may append the name of a factor or a passcode generated by a hardware token, received via SMS, or generated by Duo Mobile.
In Duo federal editions, the "phone" and "sms" factor options do not work for authentication. Users may continue to append "push" to receive a Duo Push request to Duo Mobile, or append a passcode.
Duo Universal Prompt User Experience
The Universal Prompt experience in Duo Federal plans is subject to the same limitations as the traditional Duo Prompt experience for federal customers, such as no telephony-based authentication options.
See more details about Universal Prompt and Duo Federal plans and familiarize yourself with the Universal Prompt experience for users by reviewing the Duo Universal Prompt User Guide.
Try Duo Federal Editions
Fill out the contact form on the Duo Federal editions pricing page to get started with Duo today!
