Contents
Overview
Attackers continually exploit a wide range of techniques to compromise accounts and fraudulently authenticate. Duo’s Risk-Based Authentication automatically detects and mitigates commonly-known attack patterns and high-risk anomalies. By targeting mitigation only to risky authentication attempts, Duo provides a higher level of security without compromising end-user experience.
Risk Based Authentication consists of two key capabilities: Risk-Based Factor Selection and Risk-Based Remembered Devices.
Duo Premier and Duo Advantage customers can deploy Risk-Based Authentication by applying Duo policies to specific applications or groups of users to further enhance security and automatically detect and mitigate threats to access.
Risk-Based Factor Selection
Duo Risk-Based Factor Selection analyzes authentication requests and adaptively enforces the most secure factors in response to risk. It continuously adapts its understanding of normal user behavior and identifies patterns of activity consistent with an attack.
Upon detection of a known attack pattern or anomaly, the user must authenticate using only the most secure factors. This authentication with restricted factors is known as a "step-up authentication".
For example, with Duo Push enabled in the authentication methods policy for a web application, a step-up authentication will only permit access after completing a verified Duo Push in the Universal Prompt.
If step-up authentication fails, or the user marks the attempt as fraudulent in their mobile application, all transactions are recorded and available to administrators and security professionals in the authentication logs.
If the user completes one secure authentication — either via a more secure factor or with a bypass code received from a Duo administrator — they may resume authenticating using any of the factors generally available to them.
How Risk is Assessed for Risk-Based Factor Selection
To assess risk, Duo Risk-Based Factor Selection considers the history of authentication activity from a single user or for a collection of users who have authenticated from an IP address. Depending upon the risk pattern, the algorithm may consider the time of authentication, the application's client ID or integration key, IP geolocation, or Wi-Fi Fingerprint provided by Duo Desktop.
Duo Risk-Based Factor Selection considers the following risk patterns:
- User marked fraud: A user has indicated they weren’t responsible for a login by marking it as suspicious in the Duo Mobile app.
- Push harassment: A pattern of failed authentications is consistent with an adversary performing a targeted push harassment attack against a single user.
- Push spray: A pattern of failed authentications is consistent with an adversary performing a non-targeted push attack against multiple users.
- Unrealistic travel: A user attempts to authenticate from a new location that would be impossible to reach based on the past authentication time and location.
- Country code mismatch: The authentication device and access device appear to be in two different countries.
- Novel ASN: A user attempts to authenticate from an autonomous system number (ASN) not seen in the recent history of successful authentication for the organization.
- Device distance: The authentication device and access device are abnormally far apart.
Risk is assessed both in real time at the initiation of an authentication attempt and retrospectively after an authentication has failed. Once a risky pattern of activity is identified, step-up authentication will be required until the user successfully completes one secure authentication.
Risk-Based Factor Selection Requirements
Duo Risk-Based Factor Selection works with existing authentication methods policy for web-based applications that show the Duo Universal Prompt and for the Duo Auth API application (meaning any client app that uses the named "Duo Auth API" application). Duo Authentication for Windows Logon does not support Risk-Based Factor Selection.
Risk-Based Factor Selection Methods
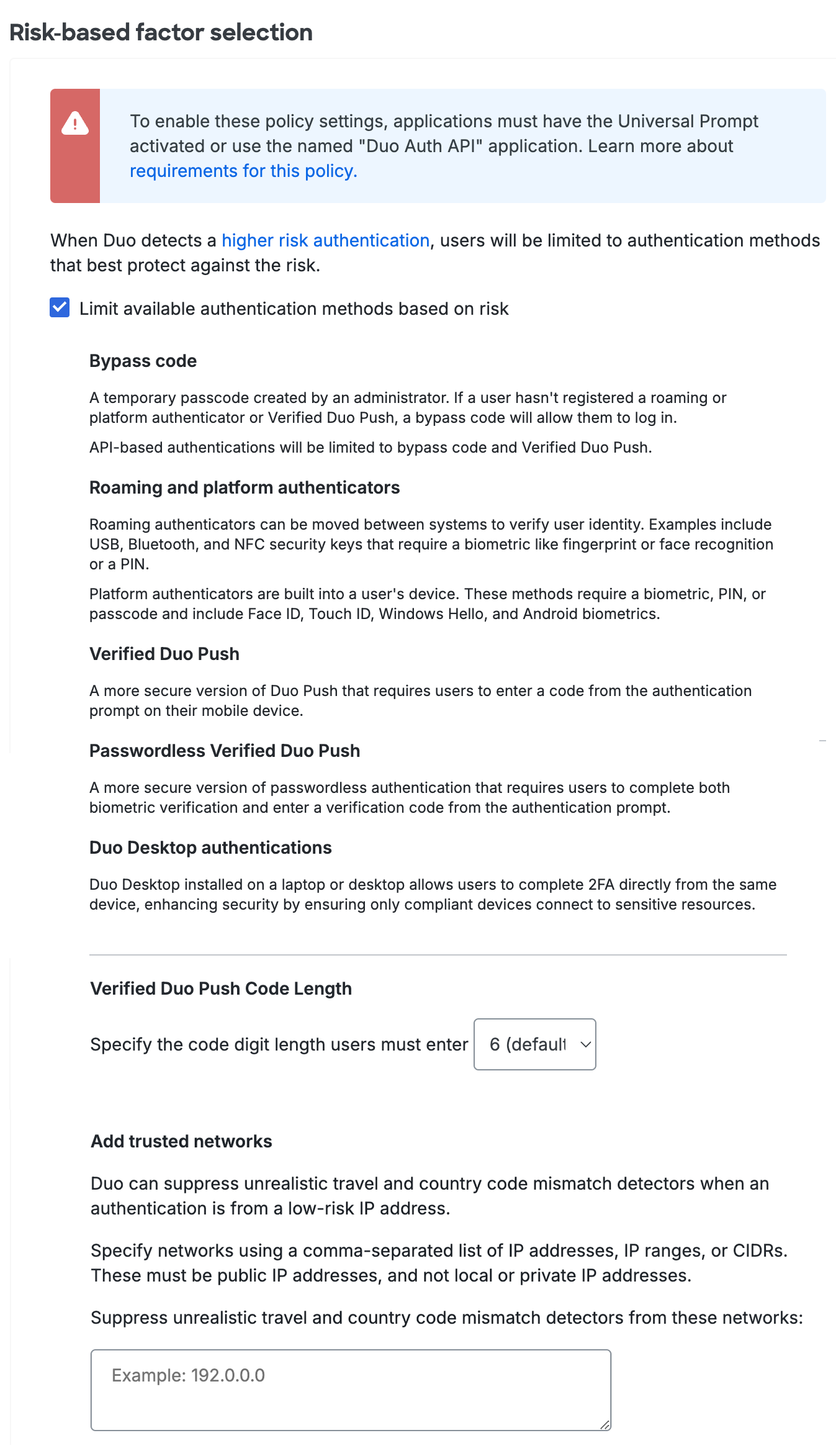
When Duo detects a high-risk authentication attempt from a user for an application with Risk-Based Factor Selection policy settings applied, Duo limits the available authentication methods to those that best protect against the risk. The user will only be allowed to authenticate by selecting from one of these secure methods to validate their authentication.
Authentication factors allowed in higher-risk authentications:
-
Verified Duo Push - A more secure version of Duo Push that requires users to enter a numeric code from the authentication prompt on their mobile device. When enabling this option you may select a verification code length from three to six digits (default: 6). Verified Duo Push automatically adds a separate layer of security on top of push by asking the user to complete an action that requires them to interact with both the access and the authentication devices.
Note: If a user's browser does not meet the requirements for the Universal Prompt and therefore falls back to traditional Duo Prompt, verified Duo Push authentication is not enforced for that user login attempt because verified Duo Push is not supported in the traditional Duo Prompt. Ensure your users have access to supported, up-to-date browsers to avoid this fallback scenario.

-
Passwordless Verified Duo Push – A more secure version of passwordless authentication that requires users to complete both biometric verification and enter a verification code from the authentication prompt.
-
Duo Desktop authentications – Duo Desktop installed on a laptop or desktop allows users to complete 2FA directly from the same device, enhancing security by ensuring only compliant devices connect to sensitive resources.
-
Roaming and platform authenticators - WebAuthn FIDO2 security keys with biometric or PIN verification, and authenticators or biometric sensors built into the device like Touch ID or Windows Hello.
-
Bypass codes - Bypass codes provided to users by a Duo administrator.
-
YubiKey passcodes - Yubico OTP/AES passcodes generated by a YubiKey token.
Note: YubiKey 6 or 8 digit OATH-HOTP passcodes do not satisfy the secure method requirement.
With Risk-based Factor Selection methods enabled via policy, ensure that you have added a secure factor that users can log into if these factors are limited. If you check the authentication log, and a warning appears indicating "No secure factors registered", this is because that user hasn't added one of the allowed methods above.
These authentication methods will be blocked for use in a higher-risk scenario:
-
Duo Push without a verification code.
-
Duo Mobile passcodes
-
SMS passcodes
-
Phone callback
-
Hardware tokens for any OTP token type other than Yubico OTP/AES.
Enable Risk-Based Factor Selection
To apply a new Risk-based Factor Selection policy to an application:
-
Log into the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to the details page of the application to which you want to apply the Risk-based Factor Selection policy. This must be an application that uses the Universal Prompt or the named Auth API application.
-
Click Apply a policy to all users if you want every user accessing this application subject to Risk-based Factor Selection, or click Apply a policy to groups of users to assign the new Risk-based Factor Selection policy to a group of users.
-
Click the Or, create a new Policy link instead of selecting a policy to apply from the drop-down list.
-
The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name at the top of the left column, and then click the Risk-based Factor Selection policy item on the left.
-
The Limit available authentication methods based on risk setting is enabled in the editor by default. You can click Show available authentication methods to view more details about which secure authentication methods will be allowed by Risk-Based Factor Selection.
-
Adjust the "Verified Duo Push Code Length" from 6 (default) to a lower number of digits if you wish.
-
Click the Create Policy button to save the settings and return to the "Apply a Policy" prompt, with the new Risk-based Factor Selection policy selected.
-
If you opted to apply Risk-based Factor Selection as a group policy, start typing in the target group's name in the Groups field and select it from the suggested names.
-
Click the Apply Policy button. The application page shows the new application or group Risk-based Factor Selection policy assignment.
You can also edit an existing custom policy or your Global Policy to add the Risk-Based Factor Selection option if you prefer.
For more information about creating and applying custom policies, see the Policy documentation.
Low-Risk IP configuration for Risk-Based Factor Selection
Duo Risk-Based Factor Selection can suppress Unrealistic Travel or Country Code Mismatch detections on authentications where its IP address is from a specified list of known low-risk IPs. To define your low-risk IP addresses, edit the policy where you enabled the Risk-based factor selection options and specify a list of IP addresses, IP ranges or CIDRs in Add Trusted Networks.
Authentication Scenarios
If a Risk-based Factor Selection policy applied to an application or user group and a user is not enrolled in a more-secure method or has no approved methods available:
- The user will be allowed to authenticate with a bypass code issued by a Duo administrator or your organization's Help Desk in order to enroll a more-secure method.
If an approved method for Risk-Based Factor Selection is disabled via an authentication methods policy:
- That method will be disabled for Risk-Based Factor Selection. If Duo Push is disabled, verified Duo Push will not be available.
Risk-Based Factor Selection and the Auth API
When a Risk-based Factor Selection policy is applied to an Auth API type application Duo responds to detected risk by limiting the factors available for the user.
Risk-based Factor Selection policy is effective only for the named "Duo Auth API" application. You can identify an Auth API application when you view it in the Duo Admin Panel by scrolling down to the "Settings" section of the application's details page and looking for a "Type" of "Auth API".
Application types other than "Auth API", even those built using Duo's Auth API methods, cannot apply effective Risk-based Factor Selection policies.
Risk-Based Factor Selection restriction has the following effects on the Auth API preauth response:
-
Duo Auth API v2 (Current): removes
auto(automatic factor selection),push(Duo Push), andphone(phone callback) from thecapabilitiesinformation for a phone device.- Verified Duo Push authentication is permitted if your Auth API client specified
client_supports_verified_push=1in the /preauth request.
- Verified Duo Push authentication is permitted if your Auth API client specified
-
Duo Auth API v1 (Legacy): removes
pushN(Duo Push) andphoneN(phone callback) from thefactorsinformation.
Unlike Universal Prompt applications, users may authenticate with a Duo Mobile passcode, a hardware token passcode, a passcode previously received via SMS, or a bypass code provided by your organization's Help Desk or Duo administrator. Roaming and platform authenticators can't be used with Auth API.
See the Auth API documentation for example API responses.
Risk-Based Remembered Devices
Duo Risk-Based Remembered Devices adds additional security to Duo's Remembered Devices feature by adapting the duration of remembered device sessions in response to risk. It looks for authentications from anomalous network locations, which may indicate theft of the remembered device token or access attempts from a lost or stolen device. When an anomalous authentication attempt is detected, the remembered device session terminates and users are required to reauthenticate.
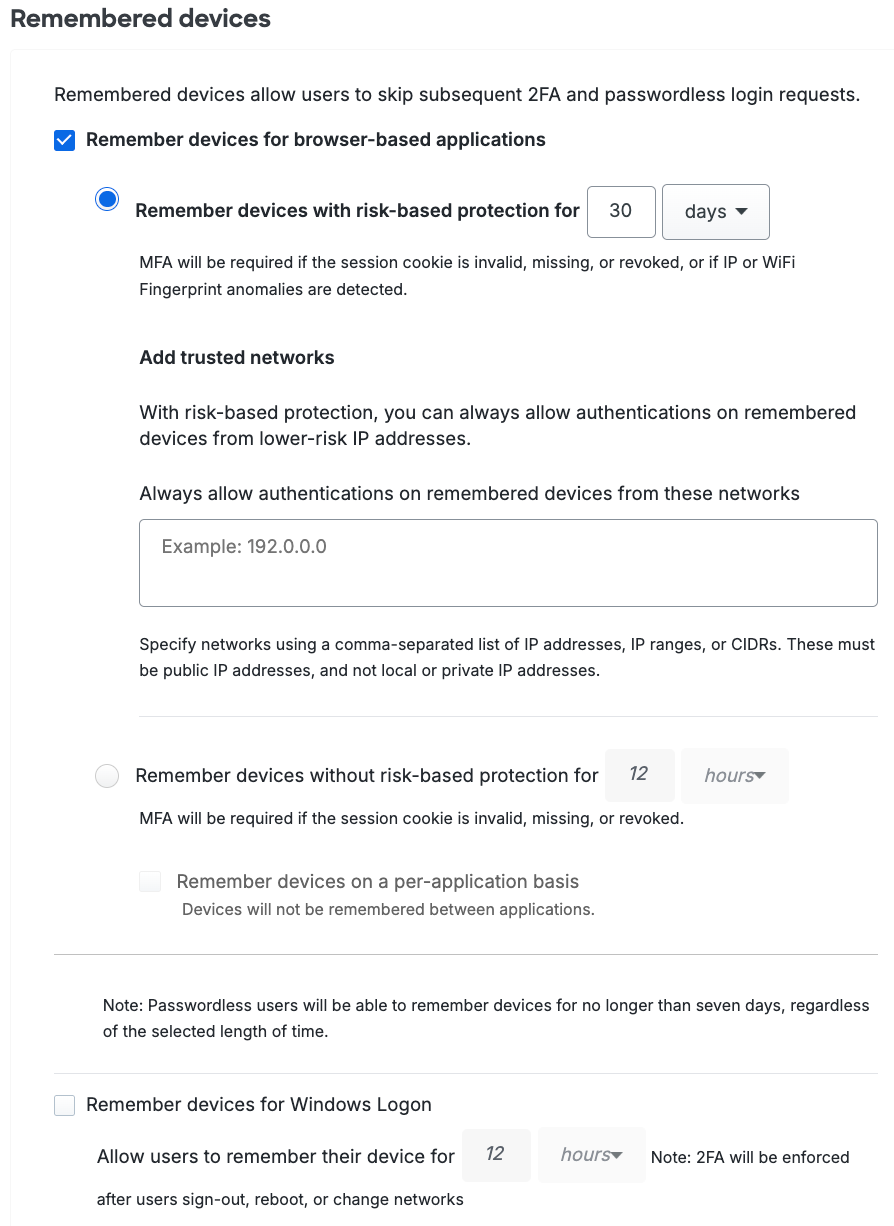
In Duo’s traditional remembered devices policy, administrators set a fixed duration for how long a device is remembered. During login, the user opts into remembering the access device by checking the "Remember me..." option in the traditional Duo Prompt or choosing "Trust browser" in the Universal Prompt. When the remembered device session expires, the user is asked to reauthenticate.
With Risk-Based Remembered Devices, the user will need to opt-in by clicking in the checkbox from the prompt if they want to be remembered. The remembered device session may terminate after a new session if it observes a change from historical baselines. By targeting session termination to anomalous authentications, it enables administrators to set longer default remembered device session durations without sacrificing security.
How Risk is Assessed for Risk-Based Remembered Devices
Duo Risk-Based Remembered Devices evaluates each authentication based on its relation to the user's IP address history. Authentications from previously unseen network locations are identified as higher-risk and require reauthentication. 30 days of successful authentications in user activity are considered.
In addition to IP history, Duo also considers an optional Wi-Fi Fingerprint provided by Duo Desktop to ensure that IP address changes reflect actual changes in location and not normal usage scenarios like a user establishing an organizational VPN session.
Risk-Based Remembered Device Requirements
Risk-Based Remembered Devices currently works for Duo’s browser-based integrations featuring either the Universal Prompt or the traditional Duo prompt. These browser-based Duo Prompt user experiences collect IP address information for access devices and makes it available in the authentication log.
In addition, Wi-Fi Fingerprint analysis requires installation of Duo Desktop on Windows and macOS access devices. Note that you do not need to configure Duo Desktop policies to make Wi-Fi Fingerprint information available to Risk-Based Remembered Device evaluation.
Enable Risk-Based Remembered Devices
To apply a new Enable Risk-Based Remembered Devices policy to an application:
-
Log into the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to the details page of the application to which you want to apply the Risk-Based Remembered Devices policy. This must be an browser-application that uses the Universal Prompt or traditional Duo Prompt.
-
Click Apply a policy to all users if you want every user accessing this application subject to Risk-Based Remembered Devices, or click Apply a policy to groups of users to assign the new Risk-Based Remembered Devices policy to a group of users.
-
Click the Or, create a new Policy link instead of selecting a policy to apply from the drop-down list.
-
The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name at the top of the left column, and then click the Remembered devices policy item on the left.
-
Select the checkbox next to Remember devices for browser-based applications and then select the Remember devices with risk-based protection for nn days option. Enter the maximum number of days you want a remembered device session to last. Passwordless remembered devices sessions last for a maximum of seven days (168 hours), even if you specify a longer duration.
-
Click the Create Policy button to save the settings and return to the "Apply a Policy" prompt, with the new Risk-Based Remembered Devices policy selected.
-
If you opted to apply Risk-Based Remembered Devices as a group policy, start typing in the target group's name in the Groups field and select it from the suggested names.
-
Click the Apply Policy button. The application page shows the new application or group Risk-Based Remembered Devices policy assignment.
You can also edit an existing custom policy or your Global Policy to add the Risk-Based Remembered Devices option if you prefer.
For more information about creating and applying custom policies, see the Policy documentation.
Transitioning to Risk-based Protection for Remembered Devices
Remembered device sessions can transition into risk-based protected sessions, meaning users will not need to perform 2FA due to a policy update. However, this transition is one-way; if the policy changes from risk-based protection to a non-risk-based one, the remembered session will not carry over.
Low-Risk IP configuration for Risk-Based Remembered Devices
Risk-Based Remembered Devices can suppress detections of a novel IP address or novel WiFi Fingerprint if the user is authenticating from a specified list of known low-risk IPs. To configure, navigate to the policy and specify a list of IP addresses, IP ranges or CIDRs in Add Trusted Networks.
Monitoring and Triage
All risk-based policies offer comprehensive logging and monitoring capabilities in the authentication logs. In addition, any authentications flagged by users are part of the existing fraud reports.
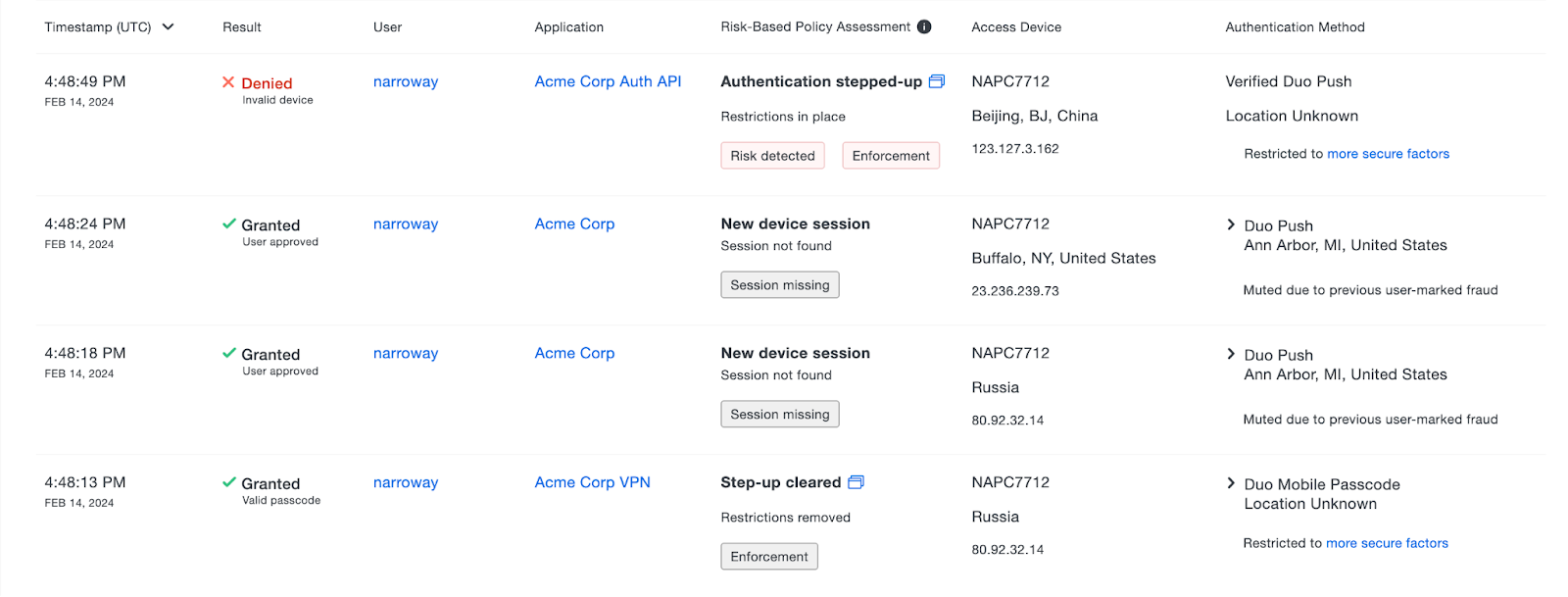
Navigate to Reports → Authentication Logs in the Duo Admin Panel. Applying risk-based policies introduces a new "Risk-Based Policy Assessment" column in the authentication logs. That information along with the additional context information in the "Result" and "Authentication Method" columns shows when and why a step-up decision occurred.
Hover your cursor over the "Risk-Based Policy Assessment" column to see more information.
Preview Mode
Duo's algorithm is adaptive and uses both historical and live data, so it can be difficult to understand what the impact of the Risk-Based Factor Selection policy will be on your users. Preview mode, the default view, allows you to see which authentications would have triggered a step-up authentication by highlighting detection information in the authentication logs.
You will see the "Risk-Based Policy Assessment" column and a banner on authentications that would have required a step-up authentication. Click on the Preview Insights button next to an authentication to learn more about what Duo detected, what would happen to the user if the policy were configured, and how many step-ups would have occurred within the past month across all your users.
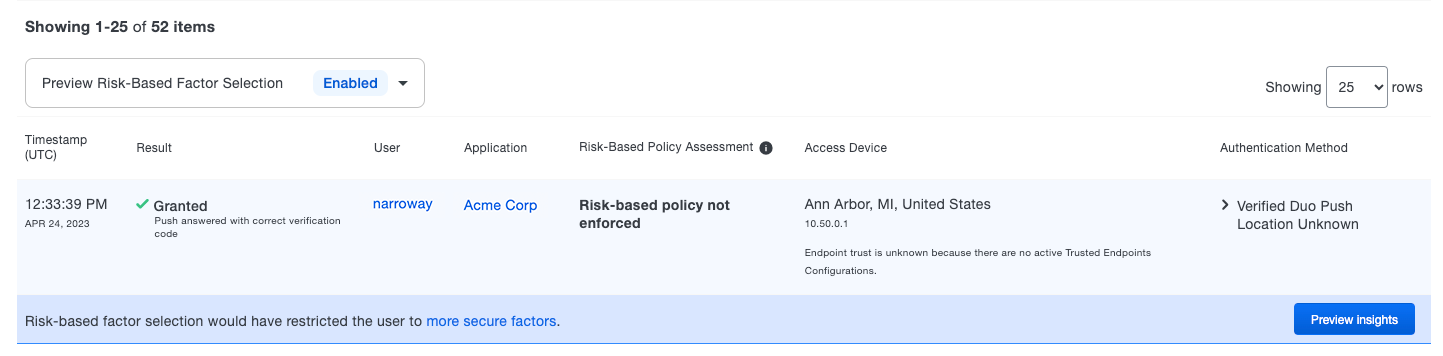
Click the Show preview mode UI elements toggle switch to off if you want to disable preview mode.
Risk-Based Policy Assessment
The risk-based policy assessment provides details about the user's step-up status, restrictions on authentication factors, and reasons why Duo took action. The risk-based policy assessment uses messaging, detection sequencing and tooltips to aid in prioritization during investigations.
Step-up States
The step-up states communicate a user's current step-up status. The following are step-up states that can be listed under the "Risk-Based Policy Assessment" column:
- Step-up initiated: The user is in a stepped-up state due to either marking the authentication as fraud or a risky pattern was detected post-authentication.
- Authentication stepped-up: The user is in a stepped-up state due to a previous authentication.
- Step-up cleared: The user is no longer in a stepped-up state after a successful authentication.
- Step-up initiated and cleared: The user was in a stepped-up state but the step-up state was immediately resolved by the user taking action.
Detection Sequence
Detection Sequencing helps string together a list of authentication logs from the point where the user is initially stepped-up until they are out of step-up status. A detection sequence is available via a clickable icon that borders the step-up state information.
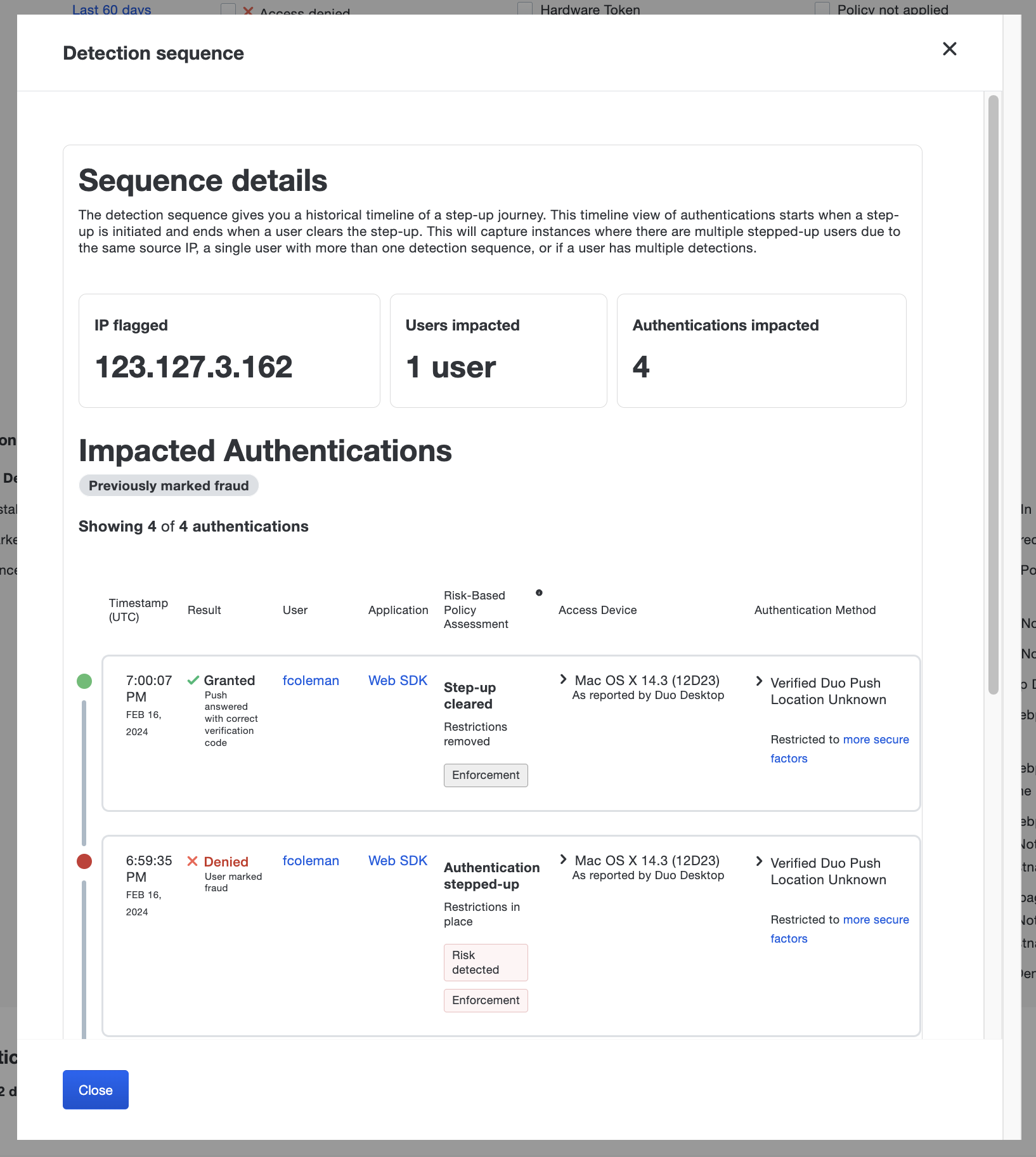
Tooltips
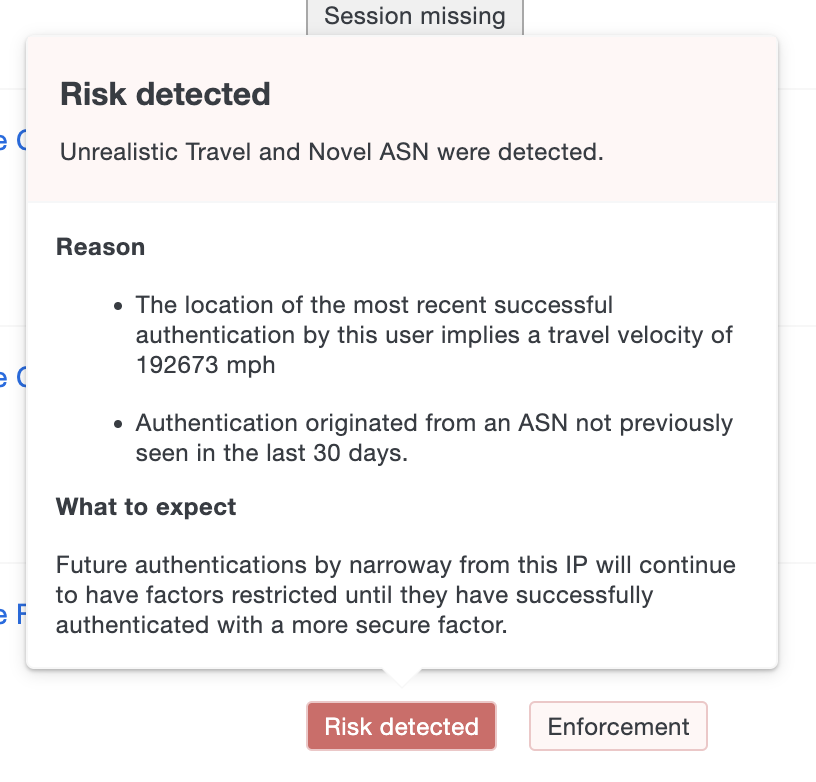
The tooltips shown under the "Risk-Based Policy Assessment" column contain additional information about the risk detected, reason for detection, restrictions on a user's authentication factors, the policy enforced, and expectations for subsequent authentications. The following are the tooltip colors and their meaning:
- Yellow: Signifies that the next authentication for the user will be stepped-up.
- Red: Signifies that the user's stepped-up state is unresolved and may need further investigation.
- Grey: Signifies that the user successfully authenticated and resolved the stepped-up state.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
