Documentation
Duo Trusted Endpoints - Chrome Enterprise Device Trust Connector
Last Updated: February 6th, 2025Contents
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known managed devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the access device's management status. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from devices not trusted by your organization.
Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Overview
Google Chrome Enterprise device trust connector is a hardware-backed and a browser-backed method of device identity and status confirmation. When a user authenticates via the Duo Universal Prompt using a Chromebook or a managed Chrome browser, the Chrome Enterprise Device Trust Connector management integration attests that the Chromebook or Chrome browser is enrolled in enterprise device management and is thus compliant with all enterprise policies.
Prerequisites
- The protected application must have the Duo Universal Prompt enabled.
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager administrative roles.
- ChromeOS devices must be enrolled in your Google Workspace domain for enterprise management.
- Chrome browsers on macOS and Windows must be enrolled in Chrome Browser Cloud Management.
The Chrome Enterprise Device Trust Connector management integration does not support Duo Passwordless authentication.
ChromeOS
Please note that ChromeOS Flex does not support Chrome Enterprise device trust connectors.
Create the Chrome Enterprise Device Trust Connector Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Chrome Enterprise Device Trust Connector in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Chrome OS from the "Recommended" options, and then click the Add button.
The new Chrome Enterprise Device Trust Connector integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Turning on this integration will take precedence over any other ChromeOS integration that is also active.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Chrome Enterprise Device Trust Connector integration page to complete the Google Workspace configuration steps.
Configure Chrome Device Connector in Google Workspace for ChromeOS
-
Log on to the Google Workspace Admin console as an administrator and navigate to Devices, and then use the left-side navigation to go to Chrome → Connectors.
-
Click NEW PROVIDER CONFIGURATION, locate Cisco in the provider list, and click SET UP underneath it.
-
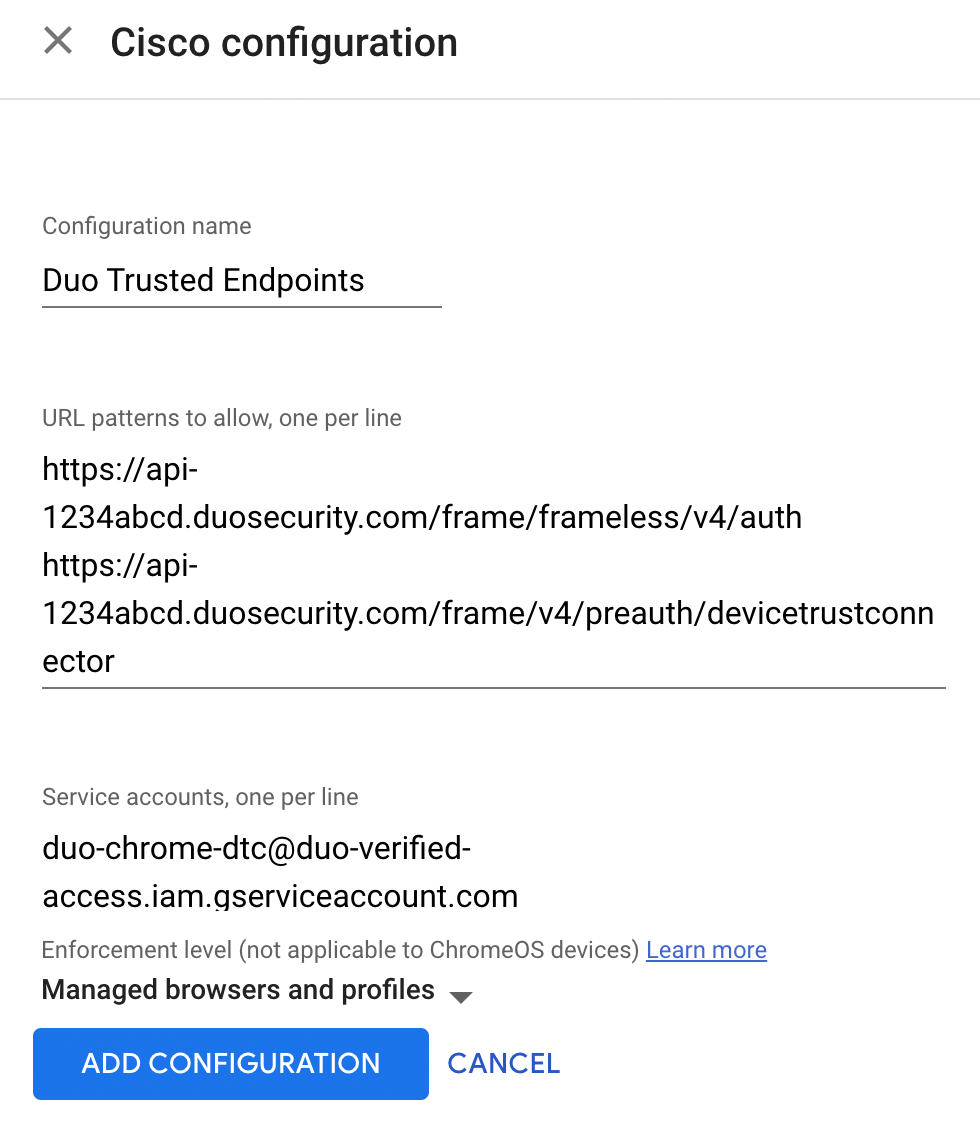
Give your new Cisco configuration any meaningful and unique Configuration name you wish. If you will be creating Chrome Enterprise Device Trust Connector integrations for multiple operating systems you might want to include the OS name here.
-
Return to the Chrome Enterprise Device Trust Connector for Chrome OS management integration page in the Duo Admin Panel and copy the URL patterns to allow, and then paste it in the URL patterns to allow field.
-
Copy the account string from the Chrome Enterprise Device Trust Connector management integration page in the Duo Admin Panel and paste it in the Services accounts field. Setting the Enforcement level is not required.
-
Click ADD CONFIGURATION to save.
-
Proceed to add your Google Workspace domain information in Duo.
Learn more about Google Chrome Enterprise device trust connectors.
macOS
Create the Chrome Enterprise Device Trust Connector Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Chrome Enterprise Device Trust Connector in the list of "Device Management Tools" and click the Add this integration selector.
- Choose macOS from the "Recommended" options, and then click the Add button.
The new Chrome Enterprise Device Trust Connector integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Turning on this integration will take precedence over any certificate-based Trusted Endpoint integration that is also active. If the Chrome Enterprise Device Trust Connector trust check fails any active Duo Desktop based integrations will run a trust check as a fallback.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Chrome Enterprise Device Trust Connector integration page to complete the Google Workspace configuration steps.
Configure Chrome Device Connector in Google Workspace for macOS
-
Log on to the Google Workspace Admin console as an administrator and navigate to Devices, and then use the left-side navigation to go to Chrome → Connectors.
-
Click NEW PROVIDER CONFIGURATION, locate Cisco in the provider list, and click SET UP underneath it.
-
Give your new Cisco configuration any meaningful and unique Configuration name you wish. If you will be creating Chrome Enterprise Device Trust Connector integrations for multiple operating systems you might want to include the OS name here.
-
Return to the Chrome Enterprise Device Trust Connector for macOS management integration page in the Duo Admin Panel and copy the URL patterns to allow, and then paste it in the URL patterns to allow field.
-
Copy the account string from the Chrome Enterprise Device Trust Connector management integration page in the Duo Admin Panel and paste it in the Services accounts field. Setting the Enforcement level is not required.

-
Click ADD CONFIGURATION to save.
-
Proceed to add your Google Workspace domain information in Duo.
Learn more about Google Chrome Enterprise device trust connectors.
Windows
Create the Chrome Enterprise Device Trust Connector Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Chrome Enterprise Device Trust Connector in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Windows from the "Recommended" options, and then click the Add button.
The new Chrome Enterprise Device Trust Connector integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Turning on this integration will take precedence over any certificate-based Trusted Endpoint integration that is also active. If the Chrome Enterprise Device Trust Connector trust check fails any active Duo Desktop based integrations will run a trust check as a fallback.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Chrome Enterprise Device Trust Connector integration page to complete the Google Workspace configuration steps.
Configure Chrome Device Connector in Google Workspace for Windows
-
Log on to the Google Workspace Admin console as an administrator and navigate to Devices, and then use the left-side navigation to go to Chrome → Connectors.
-
Click NEW PROVIDER CONFIGURATION, locate Cisco in the provider list, and click SET UP underneath it.
-
Give your new Cisco configuration any meaningful and unique Configuration name you wish. If you will be creating Chrome Enterprise Device Trust Connector integrations for multiple operating systems you might want to include the OS name here.
-
Return to the Chrome Enterprise Device Trust Connector for Windows management integration page in the Duo Admin Panel and copy the URL patterns to allow, and then paste it in the URL patterns to allow field.
-
Copy the account string from the Chrome Enterprise Device Trust Connector management integration page in the Duo Admin Panel and paste it in the Services accounts field. Setting the Enforcement level is not required.

-
Click ADD CONFIGURATION to save.
-
Proceed to add your Google Workspace domain information in Duo.
Learn more about Google Chrome Enterprise device trust connectors.
Add Google Workspace Domains to Duo
-
Return to your Chrome Enterprise Device Trust Connector management integration for Chrome OS, macOS, or Windows details page in the Duo Admin Panel.
-
Enter a comma-separated list of your Google Workspace domains in the "Enter Google Workspace Domains" box and click Save. Most organizations will only need to specify one Google Workspace domain.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Finish Trusted Endpoints Deployment
After creating the Chrome Enterprise Device Trust Connector Trusted Endpoints integration, set the Trusted Endpoints policy to start checking for Chromebook or Chrome browser enrollment as users authenticate to Duo-protected services and applications.
When your trusted endpoints policy is applied to your Duo applications, return to the Chrome Enterprise Device Trust Connector Trusted Endpoints integration in the Admin Panel. The "Change Integration Status" section of the page shows the current integration status (disabled by default after creation). You can choose to either activate this integration only for members of a specified test group, or activate for all users.
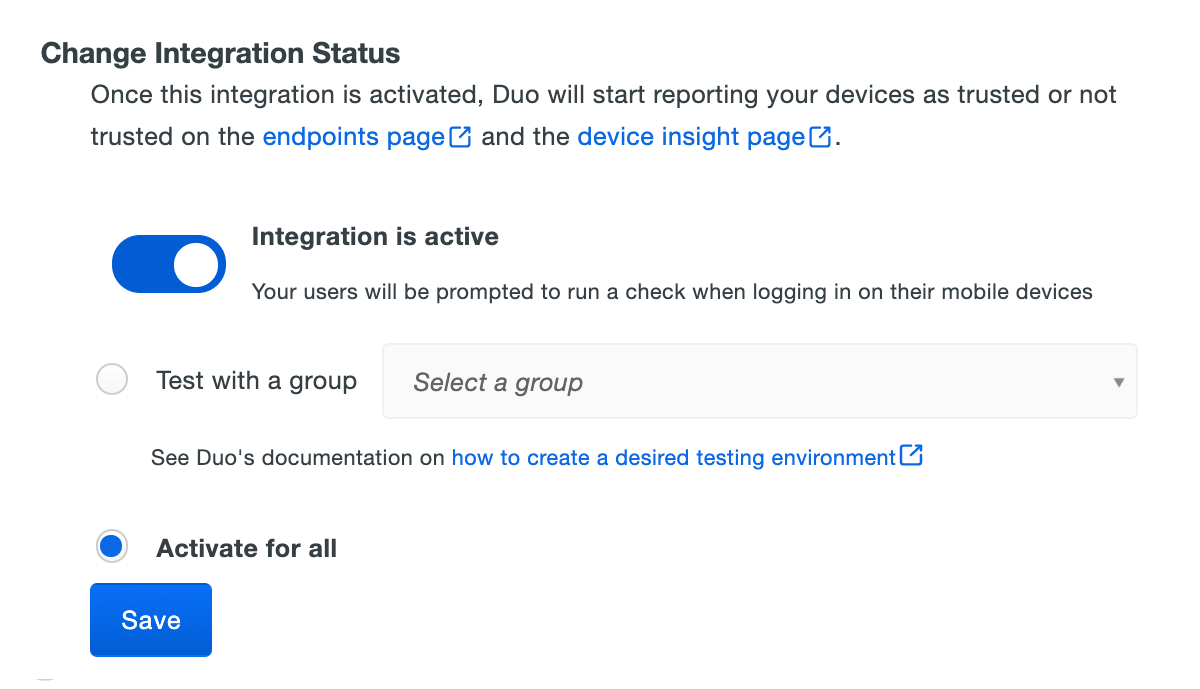
The Device Insight and Endpoints pages in the Duo Admin Panel show which access devices are Google verified.
Verify Your Setup
Authenticate to a protected application using an enrolled Chromebook or an enterprise-managed Chrome browser on macOS or Windows.
With the trusted endpoints policy set to "Allow all endpoints", users receive access to the application (assuming the Chromebook or managed Chrome browser passes all other policy verification), and Duo records the trusted or untrusted status of that device.
With the trusted endpoints policy set to "Require endpoints to be trusted" and Duo successfully verifies the Chromebook or managed Chrome browser's management status and configuration against the required policy settings, then the user receives access to the protected application.
With the trusted endpoints policy set to "Require endpoints to be trusted" and the Chromebook or managed Chrome browser fails the configuration and policy checks, then Duo blocks access to the application from the unmanaged device.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
