Documentation
Duo Trusted Endpoints - Cisco Meraki Systems Manager Device Deployment
Last Updated: April 24th, 2025Contents
Certificate-based Trusted Endpoint verification for Cisco Meraki Systems Manager reached end-of-life on October 7, 2024. Duo device certificates will no longer renew after October 2024. Migrate existing iOS Certificate Configuration management integrations to iOS Configuration. Learn more about the end-of-life timeline and migration options in the Duo Trusted Endpoints Certificate Migration Guide.
Overview
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the access device's management status. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from devices not trusted by your organization.
Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Before enabling the Trusted Endpoints policy on your applications, you'll need to allow REST API access for Duo to your managed mobile devices, or deploy Duo Desktop to Windows and macOS managed systems.
This guide walks you through Cisco Meraki Systems Manager configuration for Windows and macOS endpoint clients and Android and iOS mobile devices.
Mobile Trusted Endpoints and Verified Duo Push: Trusted endpoint verification of iOS and Android devices with Duo Mobile uses the standard Duo Push approval process and will not prompt for a Duo Push verification code, even if the effective authentication methods policy for the user and application has "Verified Duo Push" enabled.
Prerequisites
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager administrative roles.
- Access to the Cisco Meraki Systems Manager Dashboard as an administrator with the rights to create managed apps, app profiles, API keys, and device profiles.
If you plan to verify trust status for Windows and macOS systems:
-
Add your Windows and macOS devices to the Meraki device list and enroll your devices in Meraki Systems Manager.
-
Deploy Duo Desktop for Windows 10 and later or macOS to your Meraki-managed endpoints. Refer to the Duo Desktop documentation to learn about different options for deploying the application.
Note that you do not need to configure a Duo Desktop policy in order to use Meraki with Duo Desktop.
Android Configuration
Duo determines trusted device status on Android devices by leveraging the installed and activated Duo Mobile application on a given device to verify device information. To enable this verification you'll need to grant Duo read-only access to those devices via your Meraki's API access.
Create the Cisco Meraki Systems Manager Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Cisco Meraki Systems Manager in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Android from the "Recommended" options, and then click the Add button.
The new Cisco Meraki Systems Manager integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration takes advantage of managed app configuration and therefore Duo Mobile must be installed by your MDM for the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Cisco Meraki Systems Manager management integration page to complete the Android configuration steps.
Configure Android Enterprise Managed Domain
-
Log on to the Meraki Dashboard as an administrator and navigate to Organization → Configure → MDM.
-
Scroll down to the "Android Enterprise" section of the "MDM settings" page.
-
Next to "Start a new enrollment", select Meraki managed deployment as the enroll type and then click the step 1 Get Signup URL button.
-
The Meraki UI updates step 2 with a link to the Google Play store. Click the Continue to Google to set up Android Enterprise link. If you're prompted to sign-in to Google, ensure the email address used is associated with your organization, and not associated with a G Suite domain.
-
Complete the Google Play for Work registration to return to the Meraki Dashboard. You should see your Google registration account's domain. Click Save.
Add Duo as a Managed App
-
In the Meraki Dashboard, navigate to Systems Manager → Manage → Apps.
-
Click the + Add app button on the right.
-
Click Android to filter to that platform, select the Play Store app app type, and click Next.
-
Search for the Duo Mobile app using the search bar on the "Add new Android app" page. Click the search result for Duo Mobile to select it.
-
Click “Select“ at the top of the app page.
-
In the "Targets" section of the Duo Mobile app page, change the Scope selection to All devices to apply to all Android devices, or with ANY of the following tags. If you choose the latter, select the Device tags you created to identify Android pilot or test devices.
-
Scroll down to the bottom of the page and click the Save button.
Add a Duo App Profile for Android Devices
-
In the Meraki Dashboard, navigate to Systems Manager → Manage → Settings.
-
Click the + Add Profile button on the right.
-
On the "Add new profile" dialog, leave Device profile (Default) selected and then click Continue.
-
Return to the Duo Admin Panel and copy the Name value shown in the "Add App Profile to Duo" section. Paste this in the Meraki Dashboard as the new profile's Name on the "New profile" page.
-
In the "Targets" section of the "New profile" page, change the Scope selection to with ANY of the following tags.
-
Use the Device tags drop-down menu to select Android devices, or you may select a tag you created to identify Android pilot or test devices.
-
Scroll down to the bottom of the New profile page and click the Save button.
-
Scroll back to the top of your new Duo Android app profile, and click + Add Settings on the left.
-
Use the search box to locate the Managed App Config settings payload. Click the Managed App Config tile to begin configuration.
-
Set the Platform to Android and the App to Duo Mobile.
-
Once you select the Duo Mobile app, Meraki fetches the app settings.
-
Click the Add button (+) to add keys to the application.
-
Return to the Duo Admin Panel and copy the Trusted Endpoints Configuration Key value. Paste this value in Meraki as the trustedEndpointConfigurationKey for Duo Mobile, with the "Type" as Text.
-
Set the trustedEndpointIdentifier "Type" as Device: ID.
-
Click the Save button.
Modify Firewall Rules for Duo
If you are using an on-premises installation of Meraki Systems Manager, you may need to modify your firewall rules so that Meraki Systems Manager APIs can communicate with Duo's service.
Use the IP ranges shown under the "Add a Firewall Rule" section on the Meraki Systems Manager management integration page in the Duo Admin Panel when updating your firewall rules and verifying connectivity.
Create the Duo REST API Key
-
Navigate to Organization → Configure → API & Webhooks.
-
Proceed to the API keys and access tab.
-
Click on the Generate API key button.
-
Copy the new API key from the Meraki Dashboard. Return to the Duo Admin Panel and paste the Meraki API key in the Meraki API Key box in the "Create a REST API key" section.
-
Click the Test Configuration button to verify Duo's API access to your Meraki instance. You'll receive a "Configuration Successful!" message if everything's correct. If the test fails, verify that you completed the Meraki configuration steps and entered the right information in the Duo Admin Panel.
-
After you successfully test your configuration, click the Save & Configure button.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify Android Device Information with Search
After you configure the connection between Meraki and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
Windows Configuration
This integration relies on having Duo Desktop present on your Meraki-managed Windows endpoints. When users authenticate to applications protected with Duo's browser-based prompt, Duo matches the device identifiers reported by Duo Desktop with managed device information obtained from Meraki in a nightly sync via read-only API access (note this sync can't be manually initiated or rescheduled at this time).
Modify Firewall Rules for Duo
If you are using an on-premises installation of Meraki Systems Manager, you may need to modify your firewall rules so that Meraki APIs can communicate with Duo's service.
Use the IP ranges shown under the "Add a Firewall Rule" section on the Meraki Systems Manager management integration page in the Duo Admin Panel when updating your firewall rules and verifying connectivity.
Create the Meraki with Duo Desktop Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Cisco Meraki Systems Manager in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Windows from the "Recommended" options, and then click the Add button.
The new Meraki with Duo Desktop integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration requires Duo Desktop to be installed on the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Cisco Meraki with Duo Desktop management integration page to complete the configuration steps.
-
Log on to the Meraki Dashboard as an administrator and navigate to Organization → Configure → API & Webhooks.
-
Proceed to the API keys and access tab.
-
Click on the Generate API Key button.
-
Copy the new API key from the Meraki Dashboard. Return to the Duo Admin Panel and paste the Meraki API key in the Meraki API Key box in the "Create a REST API key" section.
-
Click the Test Configuration button to verify Duo's API access to your Meraki instance. You'll receive a "Configuration Successful!" message if everything is correct. If the test fails, verify that you completed the Meraki configuration steps and entered the right information in the Duo Admin Panel.
-
After you successfully test your configuration, click the Save & Configure button.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify Windows Device Information with Search
After you configure the connection between Cisco Meraki Systems Manager and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
macOS Configuration
This integration relies on having Duo Desktop present on your Meraki-managed macOS endpoints. When users authenticate to applications protected with Duo's browser-based prompt, Duo matches the device identifiers reported by Duo Desktop with managed device information obtained from Meraki in a nightly sync via read-only API access (note this sync can't be manually initiated or rescheduled at this time).
Modify Firewall Rules for Duo
If you are using an on-premises installation of Meraki Systems Manager, you may need to modify your firewall rules so that Meraki APIs can communicate with Duo's service.
Use the IP ranges shown under the "Add a Firewall Rule" section on the Meraki Systems Manager management integration page in the Duo Admin Panel when updating your firewall rules and verifying connectivity.
Create the Meraki with Duo Desktop Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Cisco Meraki Systems Manager in the list of "Device Management Tools" and click the Add this integration selector.
- Choose macOS from the "Recommended" options, and then click the Add button.
The new Meraki with Duo Desktop integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration requires Duo Desktop to be installed on the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Meraki with Duo Desktop management integration page to complete the configuration steps.
-
Log on to the Meraki Dashboard as an administrator and navigate to Organization → Configure → API & Webhooks.
-
Proceed to the API keys and access tab.
-
Click on the Generate API key button.
-
Copy the new API key shown in the Meraki Dashboard. Return to the Duo Admin Panel and paste the Meraki API key into the Meraki API Key box in the "Create a REST API key" section..
-
Click the Test Configuration button to verify Duo's API access to your Meraki instance. You'll receive a "Configuration Successful!" message if everything is correct. If the test fails, verify that you completed the Meraki configuration steps and entered the right information in the Duo Admin Panel.
-
After you successfully test your configuration, click the Save & Configure button.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify macOS Device Information with Search
After you configure the connection between Cisco Meraki Systems Manager and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
iOS Configuration
This integration relies on having the Duo Mobile app present and activated on your Meraki-managed iOS endpoints. When users authenticate to applications protected with Duo's browser-based prompt, Duo matches the device identifiers reported by the Duo Mobile app with managed device information obtained from Meraki in a nightly sync via read-only API access (note this sync can't be manually initiated or rescheduled at this time).
Create the Cisco Meraki with App Config Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Cisco Meraki Systems Manager in the list of "Device Management Tools" and click the Add this integration selector.
- Choose iOS from the "Recommended" options, and then click the Add button.
The new Cisco Meraki with App Config integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration takes advantage of managed app configuration and therefore Duo Mobile must be installed by your MDM for the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Cisco Meraki with App Config management integration page to complete the configuration steps.
Configure iOS Enterprise Managed Domain
-
Log on to the Meraki Dashboard as an administrator and navigate to Organization → Configure → MDM.
-
Find the "Apple MDM push certificate" section on the "MDM settings" page. If the current Apple MDM push certificate is valid, proceed to Add Duo as a Managed App. Continue with step 3 to renew your Meraki Apple MDM push certificate.
-
Select Review and download the certificate signing request (CSR) file from Meraki, named Meraki_Apple_CSR.csr.
-
Visit the Apple Push Certificate Portal and sign in with your Apple ID. Once logged in, select Create a certificate, and upload the Meraki CSR file you downloaded earlier.
-
Click Download and ensure the downloaded certificate file's name is MDM_Meraki_Inc._Certificate.pem.
-
Return to the Apple MDM settings in your Meraki Dashboard. Enter the Apple ID you used to generate the certificate in the field provided, and upload the Meraki .pem certificate file that you downloaded from Apple.
-
Click Renew after uploading the Apple push certificate.
-
Click Test to verify the new Apple push certificate.
For more information on Meraki Apple MDM Push Certificates, please refer to the Meraki Documentation for Apple MDM Push Certificates.
Add Duo as a Managed App
-
In the Meraki Dashboard, navigate to Systems Manager → Manage → Apps.
-
Click the + Add app button on the right.
-
Click iOS to filter to that platform, select the App Store app app type, and click Next.
-
Search for the Duo Mobile app using the search bar on the "Apps list" page. Click the search result for Duo Mobile iOS.
-
In the options for Duo Mobile, enable the Keep app up to date and Attempt to manage unmanaged additional options.
Meraki must manage Duo Mobile for Meraki to push information to the Duo Mobile app. Enabling Attempt to manage unmanaged informs users with Duo Mobile already installed that Meraki will now manage that application.
-
In the "Targets" section of the Duo Mobile app page, change the Scope selection to All devices to apply to all iOS devices, or with ANY of the following tags. If you choose the latter, select the Device tags you created to identify iOS pilot or test devices.
-
Scroll down to the bottom of the page and click the Save button.
Add a Duo App Profile for iOS Devices
-
In the Meraki Dashboard, navigate to Systems Manager → Manage → Settings.
-
Click the + Add Profile button on the right.
-
On the "Add new profile" dialog, leave Device profile (Default) selected and then click Continue.
-
Return to the Duo Admin Panel and copy the Name value shown in the "Add App Profile to Duo" section. Paste this in the Meraki Dashboard as the new profile's Name on the "New profile" page.
-
In the "Targets" section of the "New profile" page, change the Scope selection to with ANY of the following tags.
-
Use the Device tags drop-down menu to select iOS devices, or you may select a tag you created to identify iOS pilot or test devices.
-
Scroll down to the bottom of the New profile page and click the Save button.
-
Scroll back to the top of your new Duo iOS app profile, and click + Add Settings on the left.
-
Use the search box to locate the Managed App Config settings payload. Click the Managed App Config tile to begin configuration.
-
Set the Platform to iOS and the App to Duo Mobile.
-
Once you select the Duo Mobile app, Meraki fetches the app settings.
-
Click the Add button (+) to add keys to the application.
-
Return to the Duo Admin Panel and copy the Trusted Endpoints Configuration Key value. Paste this value in Meraki as the trustedEndpointConfigurationKey for Duo Mobile, with the "Type" as Text.
-
Set the trustedEndpointIdentifier "Type" as Device: ID.
-
Click the Save button.
Modify Firewall Rules for Duo
If you are using an on-premises installation of Meraki Systems Manager, you may need to modify your firewall rules so that Meraki APIs can communicate with Duo's service.
Use the IP ranges shown under the "Add a Firewall Rule" section on the Meraki Systems Manager management integration page in the Duo Admin Panel when updating your firewall rules and verifying connectivity.
Create the Duo REST API Key
-
Navigate to Organization → Configure → API & Webhooks in the Meraki Dashboard.
-
Proceed to the API keys and access tab.
-
Click on the Generate API key button.
-
Copy the new API key from the Meraki Dashboard. Return to the Duo Admin Panel and paste the Meraki API key in the Meraki API Key box in the "Create a REST API key" section.
-
Click the Test Configuration button to verify Duo's API access to your Meraki instance. You'll receive a "Configuration Successful!" message if everything's correct. If the test fails, verify that you completed the Meraki configuration steps and entered the right information in the Duo Admin Panel.
-
After you successfully test your configuration, click the Save & Configure button.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify iOS Device Information with Search
After you configure the connection between Meraki and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
iOS Certificate Configuration
End of Life Information
New Meraki certificate deployment management integrations may no longer be created as of October 2021, and reached end of life on October 7. 2024. Duo device certificates will no longer renew after October 2024. You must migrate your certificate-based iOS Cisco Meraki integration to Cisco Meraki with App Config. See the Duo Knowledge Base article Guide to updating Trusted Endpoints iOS integrations from certificates to AppConfig for more information about migrating your iOS certificate-based management integrations to App Config.
Use of the Duo Desktop for trust attestation provides several advantages over the use of device certificates:
- It provides a more accurate assessment of your managed devices, and removes concerns about long-lived certificates present on devices no longer managed by your organization.
- It extends support to Firefox users. Trusted Endpoint certificate detection only works with Chrome, Edge, Safari, and Internet Explorer (depending on the management system).
- Improves trust detection for web browsers and thick client applications.
See the Duo Trusted Endpoints Certificate Migration Guide for more information.
Finish Trusted Endpoints Deployment
Once your Meraki managed devices receive the Duo config you can set the Trusted Endpoints policy to start checking for managed device status as users authenticate to Duo-protected services and applications.
When your trusted endpoints policy is applied to your Duo applications, return to the Meraki trusted endpoint management integration in the Admin Panel. The "Change Integration Status" section of the page shows the current integration status (disabled by default after creation). You can choose to either activate this management integration only for members of a specified test group, or activate for all users. If you created more than one Cisco Meraki management integration, you must activate each one individually.
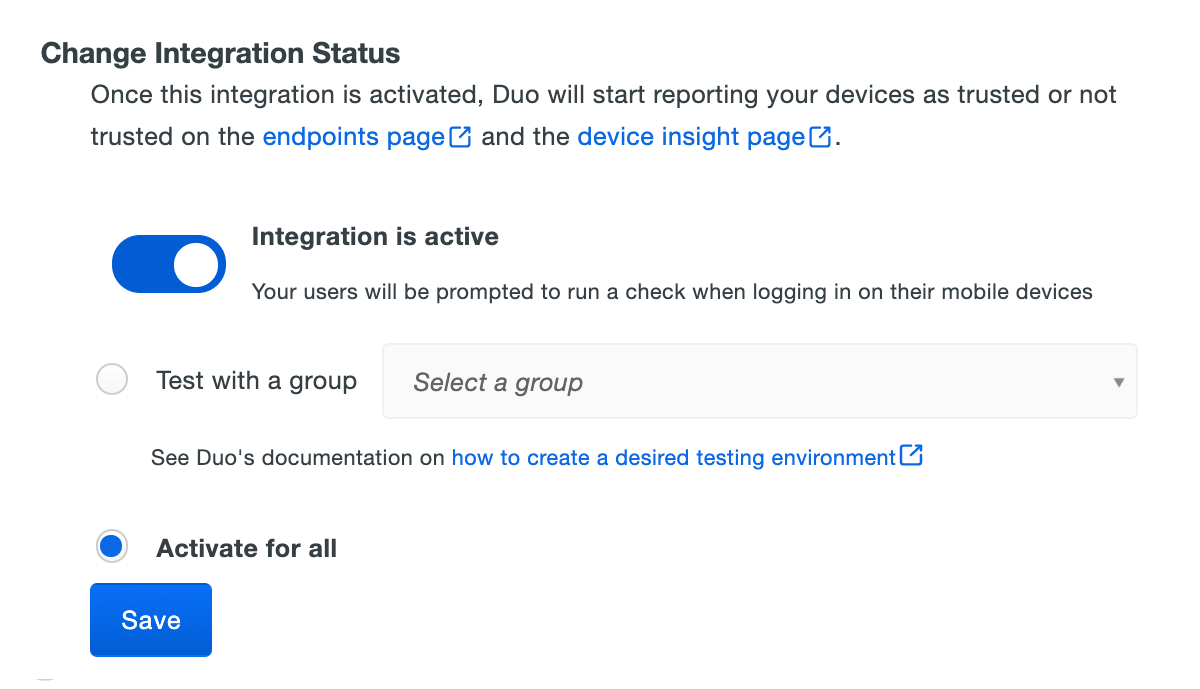
Duo Premier and Duo Advantage plans: The Device Insight and Endpoints pages in the Duo Admin Panel show which access devices are trusted/managed.
Verify Your Setup
Users see a device trust dialog on their iOS and Android devices when authenticating to a protected resource via the Duo Prompt.
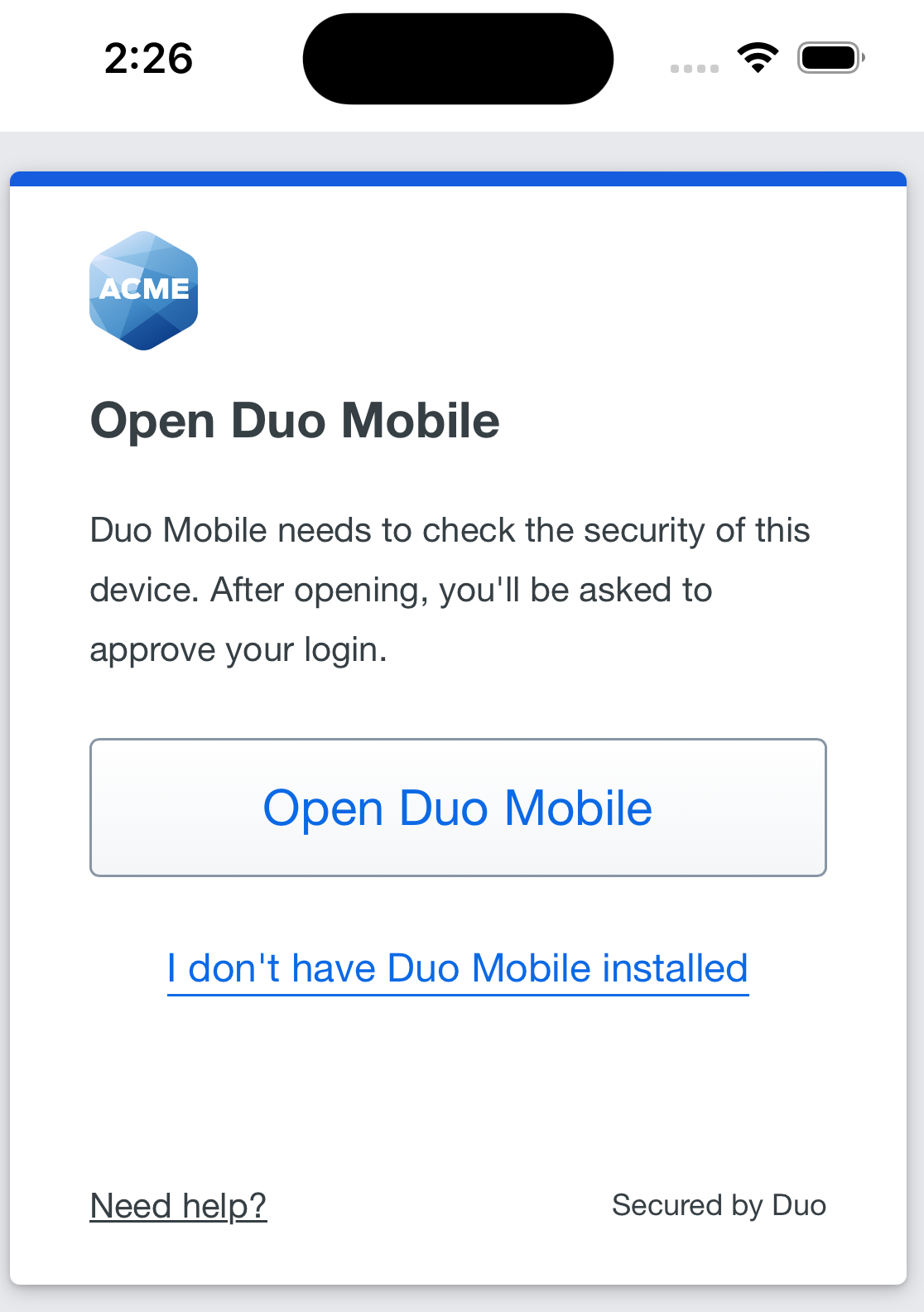
Duo uses the API access you granted in Meraki to perform a permissions check to verify device information.
If Duo successfully verifies the device information using the Meraki API access, and the user has Duo Mobile activated for Duo Push, then the user receives a login request on their phone.
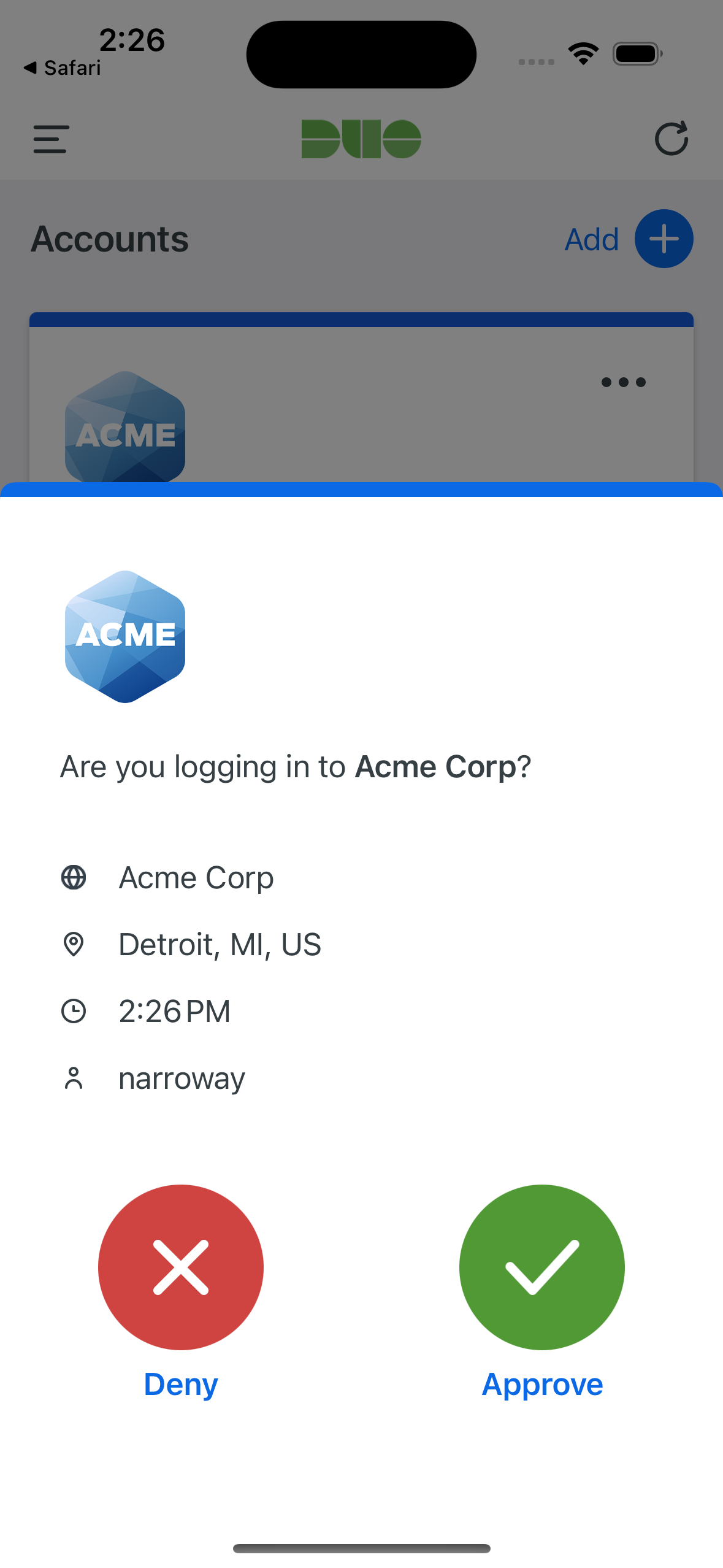
On Android devices, approving the request grants access and returns the user to the protected application. On iOS devices, after approving the Duo authentication request users tap the top-left of the Duo Mobile app to return to the application and complete login. The "Second Factor" logged for these approvals is shown as "Duo Mobile Inline Auth" in the Duo authentication log.
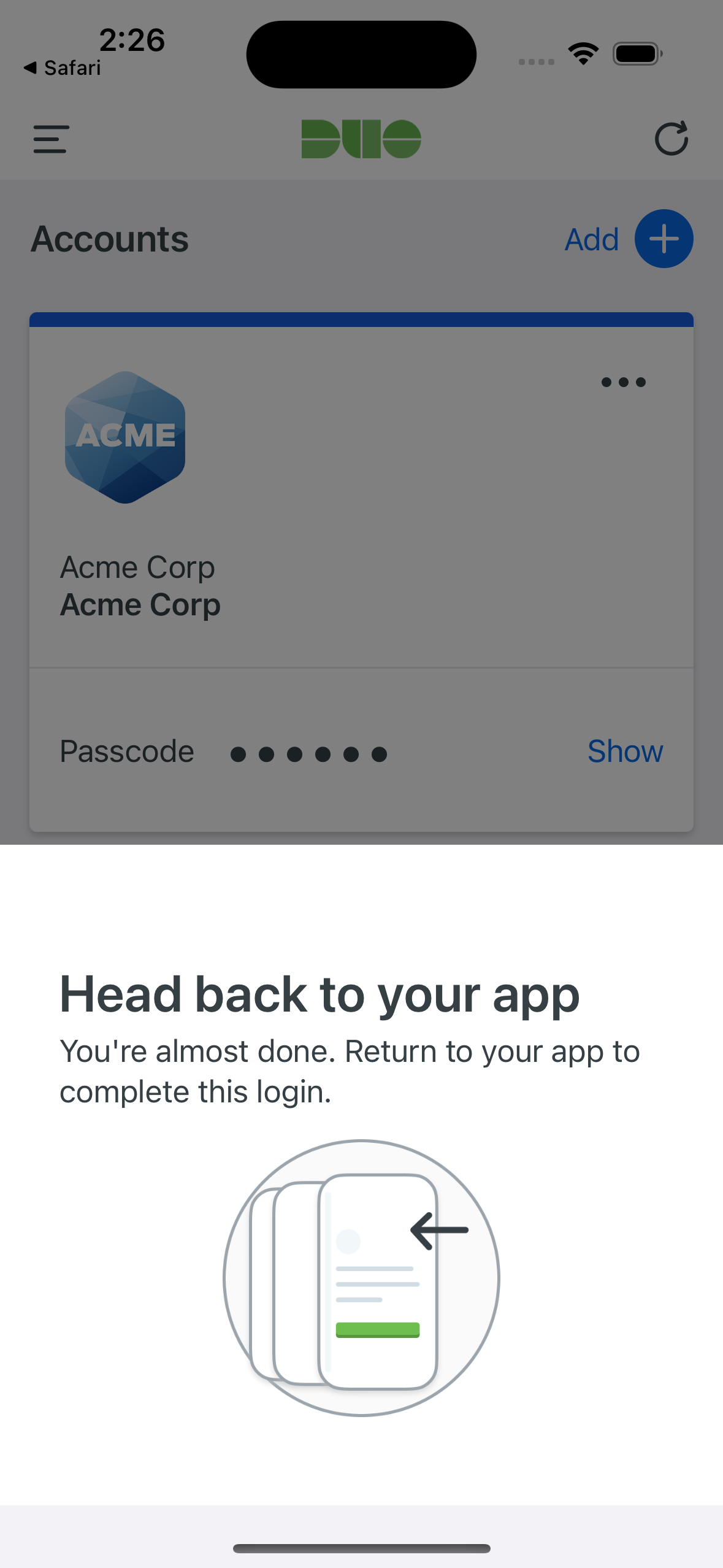
If the user does not have Duo Mobile activated for push, or does not approve the Duo request before it times out, the user returns to the Duo Prompt, where they may select from the available factors to complete 2FA.
Windows and macOS with Duo Desktop
When Windows or macOS users access Duo-protected resources, Duo Desktop provides device information to Duo. If the information from the device matches the information in Cisco Meraki Systems Manager, Duo grants access to the trusted device.
Search for Device Identifiers
If you configured Duo Desktop for Windows or macOS or Duo Mobile for iOS with App Config or Android to determine device trust, you may want to search for specific device identifiers to verify that the identifier information for a given trusted device exists in Duo. This can be useful to verify a device you expect to be trusted was imported from Meraki into Duo.
To search for a device identifier in Duo:
-
Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
-
Locate the Cisco Meraki Systems Manager, Meraki with Duo Desktop, or Cisco Meraki with App Config device management integration you want to search for a device identifier in the list and click on it to view its details.
-
In the Check if devices have synced section, enter the identifier for the device you want to check and click Search.
-
A message appears indicating if the device identifier was either found or not found. If the device identifier is not found, check your Meraki API configuration and wait 24 hours.
Use these instructions to find the device identifier for iOS and Android devices to search in Meraki:
-
Log in to the Meraki Systems Manager, navigate to Device list and select a device to view.
-
In the URL for the device view, there will be a URL parameter called "pn".
Example: /manage/pcc/list#pn=123456789123456789
-
The "pn" is the device identifier. Copy this value and use it to perform the search in Duo.
Use these instructions to find the device identifier for Windows and macOS devices to search in Meraki:
- Log in to the Meraki Systems Manager and navigate to Device list.
- Click the gear icon in the top-right corner of the device list table to make the UUID column visible.
- The "UUID" is the device identifier. Copy this value and use it to perform the search in Duo.
Removing the Meraki Management Integration
Be sure to unassign your trusted endpoints policy from all applications or remove the "Trusted Endpoints" configuration item from your global policy before deleting an existing Meraki integration from "Trusted Endpoints Configuration".
Leaving the policy settings in place after deleting a management tools integration may inadvertently block user access to applications.
Deleting a trusted endpoints management tool integration from the Duo Admin Panel immediately invalidates issued Duo device authentication certificates.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
